Urgent Advisory: Active Exploitation of Cisco ASA and Firepower, CVE-2025-20333 & CVE-2025-20362
November 14, 2025
By Aileen Ward
CISA has issued Emergency Directive 25-03 in response to actively exploited critical vulnerabilities in Cisco ASA and Firepower devices (CVE-2025-20333: Remote Code Execution; CVE-2025-20362: Privilege Escalation). These security flaws enable remote threat actors to bypass authentication to access restricted URL endpoints and execute code on vulnerable Cisco appliances. If chained, these vulnerabilities allow a remote, unauthenticated actor to gain complete control of an unpatched device. Verification activities have identified a critical compliance gap: devices reported as "patched" are running software versions that remain vulnerable, and CISA is tracking active exploitation of these versions within FCEB agencies. This guidance clarifies that a device is considered patched only when running a software version that mitigates both CVEs. The directive requires agencies to immediately update all ASA and Firepower devices including internal, non-public-facing systems to specified minimum software versions, and to implement additional mitigation actions for devices that remain unpatched or were updated after September 26, 2025. (Centripetal, 2025)
Impacted Versions
| Product | Software Release Train | Recommended Fixed Release | Status / Notes |
|---|---|---|---|
| Cisco FTD Software | 7.1 | Not Available | Upgrade to a newer, fixed release train. |
| Cisco FTD Software | 7.2 | 7.2.10.2 | Standard release patch. |
| Cisco FTD Software | 7.3 | Not Available | Upgrade to a newer, fixed release train. |
| Cisco FTD Software | 7.4 | 7.4.2.4 | Standard release patch. |
| Cisco FTD Software | 7.6 | 7.6.2.1 | Standard release patch. |
| Cisco FTD Software | 7.7 | 7.7.10.1 | Standard release patch. |

| Product | Software Release Train | Recommended Fixed Release | Status / Notes |
|---|---|---|---|
| Cisco ASA Software | 9.12 | 9.12.4.72 | Direct patch for impacted EoL versions. |
| Cisco ASA Software | 9.14 | 9.14.4.28 | Direct patch for impacted EoL versions. |
| Cisco ASA Software | 9.16 | 9.16.4.85 | Standard release patch. |
| Cisco ASA Software | 9.17 | Not Available | Upgrade to a newer, fixed release train. |
| Cisco ASA Software | 9.18 | 9.18.4.67 | Standard release patch. |
| Cisco ASA Software | 9.19 | Not Available | Upgrade to a newer, fixed release train. |
| Cisco ASA Software | 9.2 | 9.20.4.10 | Standard release patch. |
| Cisco ASA Software | 9.22 | 9.22.2.14 | Standard release patch. |
| Cisco ASA Software | 9.23 | 9.23.1.19 | Standard release patch. |
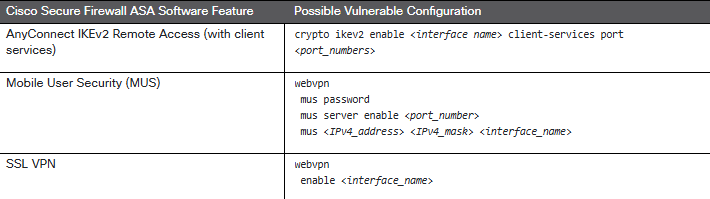
Mitigation Steps
Where applicable patch immediately according to the above table. No workarounds are available to address these vulnerabilities.
Validate that WebVPN services are not enabled to ensure a device is not public-facing.
For all Public-Facing ASA or FTD instances
Daily Checks
Perform the following checks once per day:
- Configuration Review Examine
running-configandstartup-configfor unauthorized changes. Look for:- Newly created or unfamiliar user accounts.
- Alterations to the AnyConnect WebVPN client configuration.
- Modifications that lower security (e.g., SSH vs. Telnet, weak SNMP configurations).
- Unfamiliar IPSec tunnels or site-to-site VPNs.
- WebVPN Customization Review Run
show import webvpn AnyConnect-customization. Search the output for.pdfand.batfiles not validated as legitimate. - Filesystem Search Run
dir /recursive disk0:to list active contents. Review for the same suspect.pdfor.batfiles. The commanddir /recursive all-filesystemsprovides a more verbose listing. If possible, acquire the eUSB to search for deleted items in unallocated space.
4-Hour Checks
Run the show checkheaps command every 4 hours:
- Confirm and notate the time of the
show checkheapscommand. - Copy and save the output to an isolated, external system.
- Wait 5 or more minutes and run the command again.
- Observe the "Total number of runs" value in the last row. This value should increase by approximately 1 every 60 seconds (e.g., an increase of ~5 over five minutes).
- If there is no observable positive change, this indicates a potential compromise.
Continuous Monitoring
Continuously examine syslog events
- Login Events Review logs for impossible travel or logon activity. Enable informational level syslogs (if disabled) and consider enabling debug level syslogs.
%ASA-6-716002: WebVPN session terminated: Idle Timeout%ASA-7-722029: SVC Service Termination%ASA-7-722030: SVC Service Termination%ASA-7-722031: SVC Service Termination
- Command Execution Review logs from an external repository (e.g., SIEM) for the following message IDs:
%ASA-7-111009: User 'user' executed cmd: string%ASA-5-111010: %ASA-5-111008: User 'user' executed the 'string' command.%ASA-5-111008: User, running application-name from IP, executed cmd.- Hunt for commands such as
"import webvpn anyConnect-customization", which will also cover more specific variations.
Unpatched Cisco ASA 5500-X Series Guidance
For unpatched public-facing ASA 5500-X appliances without secure boot capabilities (e.g., 5555-X, 5545-X, 5525-X, 5585-X) hosting WebVPN services, perform the following actions in addition to the above steps.
Daily Check (Prior to 1200 Local Time)
Collect a core dump and submit it for processing (e.g., to Malware NextGen) per the Core Dump and Hunt Instructions for ED 25-03.
4-Hour Checks
Perform the following checks every 4 hours:
Implant Check Run the following command. Any output indicates compromise. Save the output to an isolated, external system.
more /binary system:/text | grep 55534154 41554156 41575756 488bb3a0- Heap Check Run the
show checkheapscommand:- Confirm and notate the time of the
show checkheapscommand. - Copy and save the output to an isolated, external system.
- Wait 5 or more minutes and run the command again.
- Observe the "Total number of runs" value in the last row. This value should increase by approximately 1 every 60 seconds.
- If there is no observable positive change, this indicates a potential compromise.
- Confirm and notate the time of the
Recently Patched Device Guidance
For all public-facing devices patched after September 26, 2025, perform the following actions to check for previous compromise.
- Review WebVPN Customizations Run
show import webvpn AnyConnect-customization. Search the output for references to.pdfand.batfiles not validated as legitimate. - Examine Command Execution Logs Review logs (preferably from a SIEM) for command execution events.
%ASA-7-111009: User 'user' executed cmd: string%ASA-5-111010: %ASA-5-111008: User 'user' executed the 'string' command.%ASA-5-111008: User, running application-name from IP, executed cmd.- Hunt for commands such as
"import webvpn anyConnect-customization".
- Search Disk0 Run
dir /recursive disk0:(ordir /recursive all-filesystems) and search the output for illegitimate.pdfor.batfiles. If possible, acquire the eUSB to search for deleted items in unallocated space.
To review the extended attack chain, analysis of this campaign, and for extra material, please consult our October advisory (Centripetal, 2025) and the Cisco Security Advisories CVE-2025-20362 and CVE-2025-20333 which also contains a software checking tool if you require additional support (Cisco, 2025). Full patching to the latest versions on affected devices is strongly advised on all devices as soon as possible.
Centripetal is pleased to offer Penetration Testing and Vulnerability Assessment services to help organizations identify vulnerabilities and reduce risk. If interested, please contact our Professional Services team at profservs@centripetal.ai or reach out to your Centripetal Account Representative.
Resources
- https://www.cisa.gov/ed-25-03-guidance-device-updates-and-patching?utm_source=https://www.cisa.gov/ed-25-03-guidance-device-updates-and-patching&utm_medium=GovDelivery
- https://www.cisa.gov/temporary-risk-mitigation-guidance-agencies-process-ed-25-03-compliance
- https://www.cve.org/CVERecord?id=CVE-2025-20333
- https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-asaftd-webvpn-z5xP8EUB
- https://www.cve.org/CVERecord?id=CVE-2025-20362
- https://nvd.nist.gov/vuln/detail/cve-2025-20333
- https://www.bleepingcomputer.com/news/security/cisa-warns-feds-to-fully-patch-actively-exploited-cisco-flaws/
Know what’s coming. Stop what’s next.
Sign up for our free threat alert bulletin service here.
The Cybercrime Barrier Your Organization Deserves
Sign up for a custom demonstration from our security team of how we bring together the best minds and most complete collection of threat intelligence to provide you with a shocking level of relief.