Critical Zero-Day Vulnerabilities Identified in Cisco Adaptive Security Appliance and Firepower Threat Defense Software
By Aileen Ward
Cisco has issued an urgent warning about an active espionage campaign conducted by ArcaneDoor, a sophisticated state-sponsored threat actor. The group is exploiting two zero-day vulnerabilities, CVE-2025-20333 and CVE-2025-20362, in widely used Cisco ASA and FTD security appliances. These critical flaws allow the actor to execute code, install persistent malware, and exfiltrate sensitive data. By compromising these perimeter devices, ArcaneDoor can seize the "keys to the kingdom," gaining a powerful foothold into government and enterprise networks. A third vulnerability, CVE-2025-30363, has also been patched to prevent future exploitation.
CVE-2025-20333Vulnerability Type (CWE)CWE-120: Buffer Copy without Checking Size of Input ('Classic Buffer Overflow') CVSS ScoreBase Score: 9.9 - Critical Attack Vector: Network (AV:N) Attack Complexity: Low (AC:L) Privileges Required: Low (PR:L) User Interaction: None (UI:N) Scope: Changed (S:C) Impact on CIA:
| CVE-2025-20362Vulnerability Type (CWE)CWE-862: Missing Authorization CVSS ScoreBase Score: 6.5 - Medium Attack Vector: Network (AV:N) Attack Complexity: Low (AC:L) Privileges Required: None (PR:N) User Interaction: None (UI:N) Scope: Unchanged (S:U) Impact on CIA:
| CVE-2025-20363Vulnerability Type (CWE)CWE-122: Heap-based Buffer Overflow CVSS ScoreBase Score: 9 - Critical Attack Vector: Network (AV:N) Attack Complexity: High (AC:H) Privileges Required: None (PR:N) User Interaction: None (UI:N) Scope: Changed (S:C) Impact on CIA:
|
Impacted Versions
| Product | Software Release Train | Recommended Fixed Release | Status / Notes |
|---|---|---|---|
| Cisco ASA Software | 9.12 | 9.12.4.72 | Direct patch for impacted EoL versions. |
| Cisco ASA Software | 9.14 | 9.14.4.28 | Direct patch for impacted EoL versions. |
| Cisco ASA Software | 9.16 | 9.16.4.85 | Standard release patch. |
| Cisco ASA Software | 9.17 | Not Available | Upgrade to a newer, fixed release train. |
| Cisco ASA Software | 9.18 | 9.18.4.67 | Standard release patch. |
| Cisco ASA Software | 9.19 | Not Available | Upgrade to a newer, fixed release train. |
| Cisco ASA Software | 9.2 | 9.20.4.10 | Standard release patch. |
| Cisco ASA Software | 9.22 | 9.22.2.14 | Standard release patch. |
| Cisco ASA Software | 9.23 | 9.23.1.19 | Standard release patch. |
| Cisco FTD Software | 7 | 7.0.8.1 | Standard release patch. |
| Cisco FTD Software | 7.1 | Not Available | Upgrade to a newer, fixed release train. |
| Cisco FTD Software | 7.2 | 7.2.10.2 | Standard release patch. |
| Cisco FTD Software | 7.3 | Not Available | Upgrade to a newer, fixed release train. |
| Cisco FTD Software | 7.4 | 7.4.2.4 | Standard release patch. |
| Cisco FTD Software | 7.6 | 7.6.2.1 | Standard release patch. |
| Cisco FTD Software | 7.7 | 7.7.10.1 | Standard release patch. |
The Attack Chain
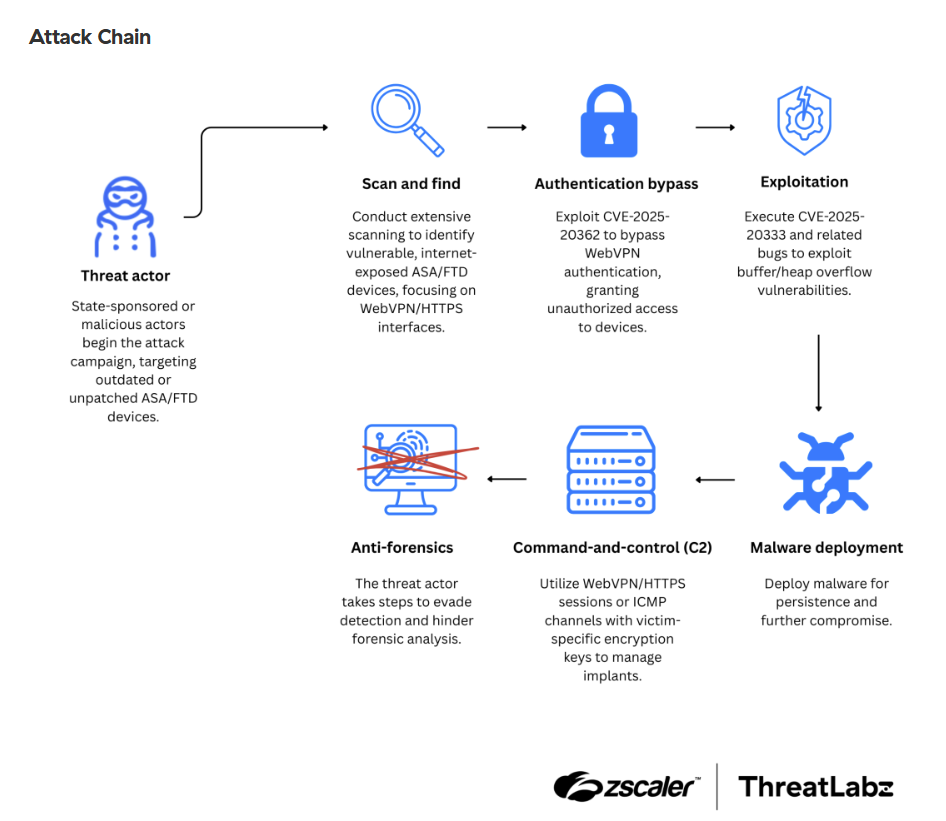
Reconnaissance and Initial Access
The attack begins with broad reconnaissance, where attackers scan the internet for vulnerable Cisco ASA/FTD devices, specifically targeting those with exposed WebVPN or HTTPS interfaces. After identifying a target, often an older ASA 5500-X series model nearing its end-of-support, they gain initial access by exploiting an authentication bypass vulnerability (CVE-2025-20362). This allows them to circumvent the login process and access protected parts of the system.
Exploitation and Execution
Once past the authentication step, the attackers chain the initial vulnerability with a second exploit (CVE-2025-20333) to achieve remote code execution. This allows them to deploy their primary payload, LINE VIPER, a modular malware system that runs directly in the device's memory. With LINE VIPER active, the attackers gain full control over the device's user-level processes.
Persistence and Command & Control
To ensure their access survives reboots and software updates, the attackers install RayInitiator, an advanced bootkit that modifies the device's GRUB bootloader. This firmware-level implant provides deep, persistent access. From there, the in-memory LINE VIPER malware establishes a covert command-and-control (C2) channel, communicating with the attackers using encrypted WebVPN sessions or ICMP tunnels.
Espionage and Anti-Forensics
With persistent control established, the attackers focus on their objective: espionage. Using LINE VIPER, they capture network traffic, exfiltrate device configurations, and create backdoor accounts. Throughout this phase, they employ aggressive anti-forensic techniques to remain undetected. This includes:
- Suppressing specific syslog IDs to hide their activity.
- Intercepting diagnostic CLI commands to return false "healthy" results.
- Intentionally crashing the device if a core dump or forensic analysis is initiated.
The entire operation is designed for stealthy data extraction from the perimeter device itself, with no evidence of the attackers moving further into the internal network.
Mitigation Strategies
Identification and Assessment
Determine Vulnerability Status First, identify your device model and software version. Cross-reference this information with Cisco's official security advisories to determine if your software release is affected.
Assess Device Configuration The primary attack vector is through VPN web services. Check if IKEv2 with client services or any SSL VPN configurations are enabled on your device.
If these services are not enabled, your device is not vulnerable to this specific campaign. However, Cisco still strongly recommends upgrading to a patched software release to protect against other threats.
If these services are enabled, your device is vulnerable.
Remediation
You have two options for remediation. Upgrading is the only permanent solution.
Option 1: Upgrade to a Fixed Release (Recommended)
This is the most effective, long-term solution.
- Upgrade Software Install a patched software release provided by Cisco to permanently resolve the vulnerabilities.
- Replace End-of-Life Devices If your device is vulnerable but has passed its end-of-life (EoL) or end-of-support date, migrate immediately to supported hardware and software.
Option 2: Mitigate via Service Disablement (Temporary)
This is a temporary workaround if you cannot immediately upgrade. It involves disabling the affected services, which will impact functionality.
A. Disable IKEv2 Client Services This will prevent VPN clients from receiving software and profile updates from the device, but IKEv2 IPsec VPN functionality will be retained.
For Cisco ASA Software (CLI): Bash
# Identify interfaces with client services enabled firewall# show running-config crypto ikev2 | include client-servicesDisable client services on the identified interfacefirewall(config)# crypto ikev2 enable <interface_name>- For FTD managed by FMC In the Remote Access VPN Policy, edit each crypto map and uncheck Enable Client Services.
- For FTD managed by FDM This platform does not support the vulnerable configuration.
B. Disable All SSL VPN Services Important: All remote access SSL VPN features will cease to function after this action.
**For Cisco ASA Software (CLI):**Bash
firewall(config)# no webvpn- For FTD managed by FMC In the Remote Access VPN Policy, edit the Access Interface tab and uncheck Enable SSL for each interface listed.
- For FTD managed by FDM In the Remote Access VPN configuration, delete all Connection Profiles.
Recovery for Potentially Compromised Devices
If you suspect or have confirmed a compromise, remediation alone is not enough. You must recover the device to a trusted state.
- Boot a Fixed Release to Remove Persistence For Cisco ASA 5500-X devices without Secure Boot, booting a patched software release will automatically scan for and remove the actor's persistence mechanism.
- If persistence is found and removed, a log file named
firmware_update.logwill be created ondisk0:, and the device will reboot into a clean system. The presence of this file is a strong indicator of prior compromise.
- If persistence is found and removed, a log file named
- Rebuild the Device Configuration (Critical Step) A compromised device's configuration, including all passwords, certificates, and keys, must be considered untrusted.
- The only way to ensure the device is clean is to reset it to factory defaults after the software upgrade.
- Reconfigure the device from scratch with new local passwords, and re-generate all certificates and keys. Do not restore a backup of the old configuration.
- How to Reset to Factory Defaults:
- Cisco ASA Software Use the
configure factory-defaultcommand. If not supported, usewrite erasefollowed byreload. - Cisco FTD Software Follow Cisco's official documentation for a complete re-image of your specific hardware series (e.g., 1000/2100/3100 or 4100/9300).
- Cisco FTD Virtual The virtual appliance must be completely re-deployed from a fresh image.
- Cisco ASA Software Use the
Threat Actor
ArcaneDoor
In April 2024, Cisco Talos released an article on the espionage campaign known as ArcaneDoor (Talos Intelligence, 2025), being conducted by the sophisticated state-sponsored threat actor UAT4356 or STORM-1849. this group has been observed to target Cisco ASAs in critical sectors previously by daisy chaining two zero-day vulnerabilities (CVE-2024-20353 and CVE-2024-20359) to deploy custom Lua-written malware. This included LineDancer, a memory-resident tool for network surveillance and configuration changes, and Line Runner, a persistent backdoor that cleverly used the device's boot process to maintain access. UAT4356 employed variety of advanced tricks to evade detection and remain persistence; employing anti-forensic measures, such as disabling logging and using hooking techniques to intercept system functions, effectively hiding their malicious activities.
In the most recent wave of attempted exploitation, Cisco identified that ArcaneDoor (Cisco, 2025) had undergone a significant evolution in attack patterns and capabilities which were observed in two new malware variants used; RayInitiator and LINE VIPER. This new toolset targets older end-of-life Cisco ASA devices that lack secure boot. RayInitiator operates as a highly persistent bootkit, flashed directly to a device's firmware to survive reboots and upgrades. Once embedded, it deploys LINE VIPER, an advanced in-memory payload. Compared to its predecessors, LINE VIPER demonstrates a greater emphasis on operational security, featuring robust anti-forensic techniques to evade detection and using victim-specific RSA keys to encrypt its command-and-control communications.
Timeline
- August 1, 2025 - Centripetal observes surges in reconnaissance activity from the IPs
- September 25, 2025 - Cisco releases Security Advisories for ASA AND FTD software VPN Web server vulnerabilities CVE-2025-20333, CVE-2025-20362 and CVE-2025-30363. NIST also publishes details of CVEs. CISA issues Emergency Directive ED 25-03: Identify and Mitigate Potential Compromise of Cisco Devices.
- September 26, 2025 - Cisco publishes event response article: Continued Attacks Against Cisco Firewalls. Deadline for CISA ED 25-03 required actions.
- October 2, 2025 - Those in use of affected Cisco products deadline to report to CISA, including all utilized devices in scope and actions taken to mitigate vulnerabilities.
TTPs

Detection Guide (Cisco, 2025)
- Searching for Missing Logs Analyze syslog data for a sudden decrease or complete absence of specific message IDs, particularly
"302013","302014","609002", and"710005", as their suppression in memory is a key indicator of compromise. - Checking for Disabled Functions Verify system integrity by running the
show checkheapscommand several times over a five-minute period; if the "Total number of runs" counter does not increase, the function may be disabled by the actor. - Identifying Suspicious Logins Monitor VPN authentication logs for "impossible travel" events, where a single user account connects from two geographically distant locations in a timeframe that would be physically impossible.
- Verifying Firmware After Upgrades After upgrading a Cisco ASA 5500-X series device, check for prior compromise by searching for a file named
"firmware_update.log"ondisk0:or by monitoring the console during boot for messages like"Bootloader verification failed"or"ROMMON verification failed".
Centripetal’s Perspective
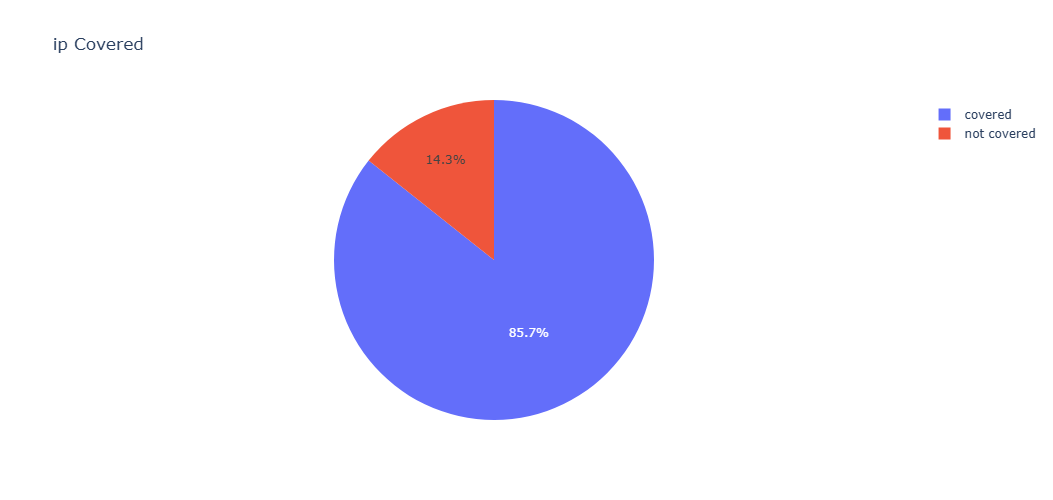
Centripetal’s aggregated threat intelligence solution observed a ~86% coverage against the IPs observed to be conducting the extensive reconnaissance against these appliances (GreyNoise, 2025).
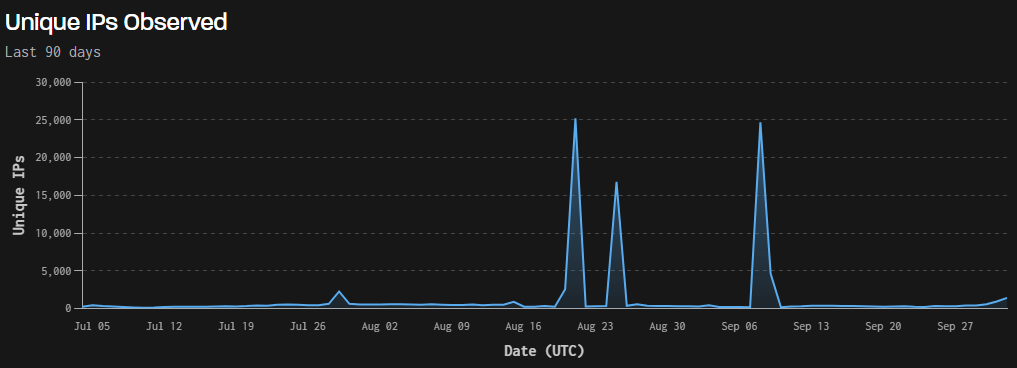
Our internal analysis showed that there was a surge in reconnaissance activity at the beginning of August from the identified IPs associated with this campaign across Centripetal’s Customer base.

Observing Figure 4 with the activity observed by GreyNoise (Figure 5; GreyNoise, 2025) at the end of September would infer that the targeted scanning was being conducted in waves in advance.
Conclusion
In the wake of another wave of ArcaneDoor, it becomes clear that network edge devices remain to be a bullseye target for threat actors. The methodical exploitation of zero-day vulnerabilities, especially on aging hardware lacking modern protections like Secure Boot, highlights a persistent and calculated strategy to undermine the foundations of network security. Weeks before these vulnerabilities were disclosed, there were reports of massive, anomalous spikes in scanning activity targeting these devices similar to foreshocks before the earthquake - there can be clear indicators of a focused, reconnaissance effort.
While zero-day exploits will always represent a formidable challenge, the future of defense cannot solely rely on a reactive posture of patching after a compromise is revealed. The continued security of our most critical infrastructure depends on our collective ability to fuse intelligence - to connect the dots between an actor's known preference for legacy hardware, observable scanning anomalies, and evolving malware tradecraft. These consolidated insights are the signals that can transform our defense from a frantic response into a proactive, intelligence-driven posture, allowing us to harden the most likely targets before they appear in the headlines.
Centripetal is also pleased to offer Penetration Testing and Vulnerability Assessment services to help organizations identify vulnerabilities and reduce risk. If interested, please contact our Professional Services team at profservs@centripetal.ai or reach out to your Centripetal Account Representative.
Public Resources
- https://sec.cloudapps.cisco.com/security/center/resources/asa_ftd_continued_attacks
- https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-asaftd-webvpn-YROOTUW
- https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-http-code-exec-WmfP3h3O
- https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-asaftd-webvpn-z5xP8EUB
- https://nvd.nist.gov/vuln/detail/cve-2025-20333
- https://nvd.nist.gov/vuln/detail/CVE-2025-20363
- https://nvd.nist.gov/vuln/detail/cve-2025-20362
- https://www.cisa.gov/news-events/directives/ed-25-03-identify-and-mitigate-potential-compromise-cisco-devices
- https://unit42.paloaltonetworks.com/zero-day-vulnerabilities-affect-cisco-software/
- https://www.zscaler.com/blogs/security-research/cisco-firewall-and-vpn-zero-day-attacks-cve-2025-20333-and-cve-2025-20362
- https://www.securityweek.com/cisco-firewall-zero-days-exploited-in-china-linked-arcanedoor-attacks/
- https://www.greynoise.io/blog/scanning-surge-cisco-asa-devices
- https://blog.talosintelligence.com/arcanedoor-new-espionage-focused-campaign-found-targeting-perimeter-network-devices/
- https://attack.mitre.org/campaigns/C0046/
Know what’s coming. Stop what’s next.
Sign up for our free threat alert bulletin service here.
The Cybercrime Barrier Your Organization Deserves
Sign up for a custom demonstration from our security team of how we bring together the best minds and most complete collection of threat intelligence to provide you with a shocking level of relief.