Tycoon 2FA versus Sneaky 2FA: Two PhaaS Campaigns Targeting MFA Bypass
By Rodrigo Luna
The Tycoon 2FA and Sneaky 2FA campaigns are two prominent phishing as a service (PhaaS) operations active in 2025. Both aim to bypass multi factor authentication (MFA) using adversary in the middle (AiTM) tactics to steal credentials and session cookies (SOCRadar, 2025). These kits are sold or rented to cybercriminals with minimal technical skill, enabling scalable phishing campaigns.
While both campaigns share a common objective, credential theft, they differ in their infrastructure, delivery methods, and targeting strategy. Tycoon 2FA is a mature, scalable PhaaS platform with widespread adoption, whereas Sneaky 2FA operates in a more selective and evasive manner, with emphasis on stealth (Sekoia, 2025).
Malware/Campaign Details & Purpose
Tycoon 2FA
| Sneaky 2FA
|
Delivery & Attack Chain
Tycoon 2FA
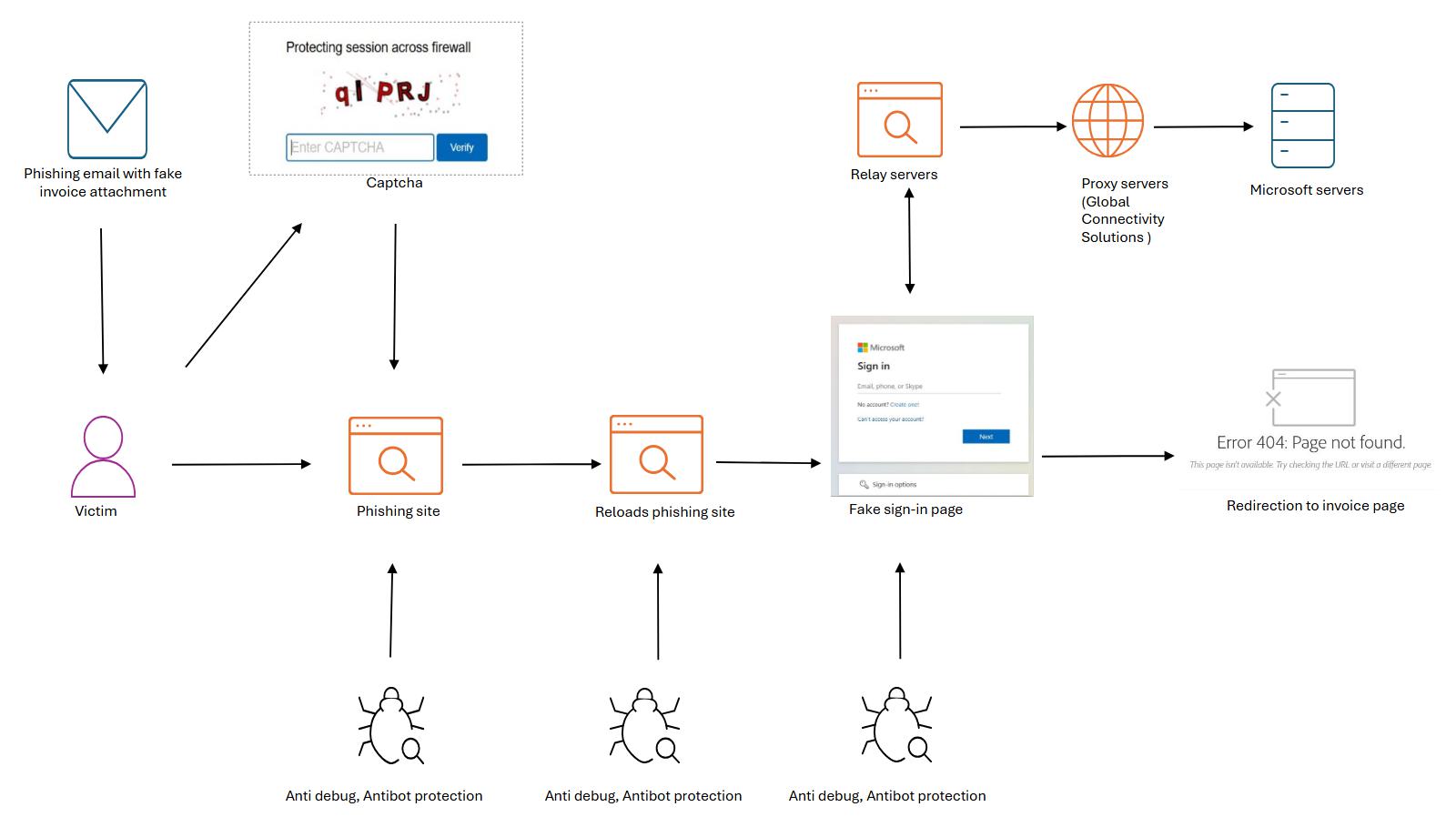
The following attack chain illustrates a real world example of a Tycoon 2FA phishing flow, as documented in an analysis by eSentire (eSentire, 2025). It highlights the use of CAPTCHAs, adversary in the middle (AiTM) proxies, and evasive infrastructure to harvest credentials and bypass MFA protections. (Figure1)
- Phishing email is sent with a fake invoice lure
- Victim is directed to a phishing site equipped with CAPTCHA and anti-bot protections
- CAPTCHA is presented to filter out automated tools and create a sense of legitimacy
- The page reloads and displays a fake Microsoft login form acting as an AiTM proxy
- Credentials and MFA session cookies are captured and forwarded via proxy infrastructure
- Victim is redirected to a decoy or error page (e.g., invoice or 404) to minimize suspicion
- Anti-debug and anti-analysis measures remain active throughout the flow to evade detection
New evasion features observed in Tycoon 2FA attacks since December 2024, according to AnyRun's campaign analysis, include: (AnyRun, 2025)
- Keystroke Interception
- Context Menu Blocking
- Invisible Obfuscation
- Disabling Clipboard Copy
- Rotating CAPTCHAs
- Obfuscation via Encryption
- Context Menu Blocking
- Complex JavaScript Logic
- Custom Fake Page Redirects
- Custom Binary Encoding
- Debugger Timing Checks
- Custom CAPTCHAs
- Extended Redirect Chains
- Browser Fingerprinting
Sneaky 2FA
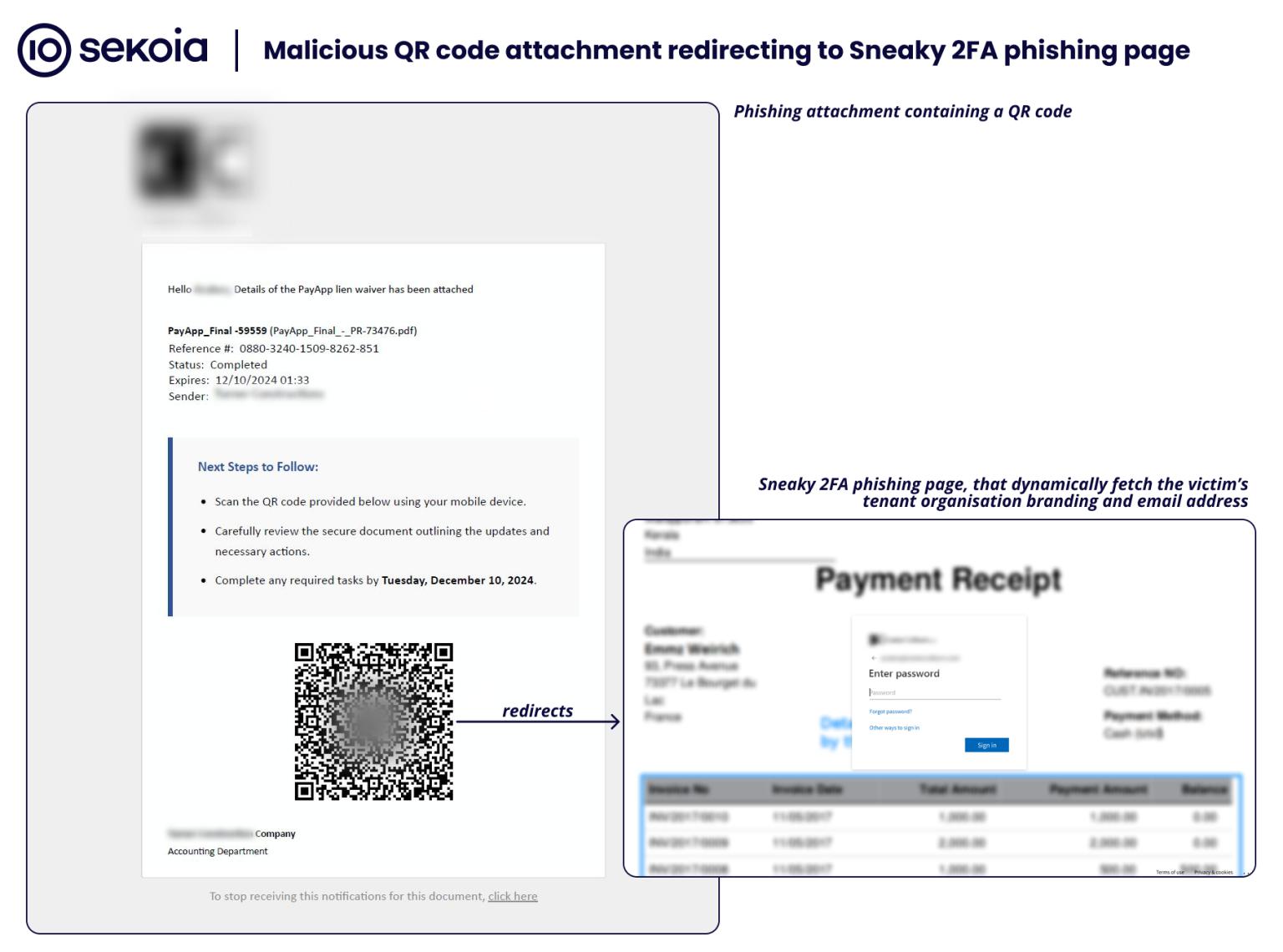
The following attack chain is based on observed Sneaky 2FA activity detailed by Sekoia (Sekoia, 2025). It demonstrates how the phishing kit uses evasion, brand impersonation, and AiTM techniques in a stealthier, more targeted campaign flow.
- Spear phishing email is sent with a lure (QR code or fake invoice attachment)
- Victim scans the QR code or clicks a malicious link that redirects to a phishing site
- The phishing page is hosted on a domain mimicking a legitimate SaaS or corporate service (OneDrive, Adobe)
- The site uses cloaking to only serve the phishing page under specific conditions (user-agent, referrer, IP range)
- A fake login portal is displayed that proxies credentials and MFA session cookies via an AiTM mechanism
- Once harvested, the victim is redirected to a benign or blank page to avoid suspicion
- The phishing domain is taken offline shortly after use to minimize detection and IOC propagation
Operational Model
Tycoon 2FA
Tycoon 2FA operates as a commercial PhaaS offering, available through dark web forums and marketplaces. Access is typically granted to affiliates via subscription. The platform includes a management dashboard, hosting infrastructure, and regularly updated phishing templates.
Notable operational characteristics include:
- Affiliate dashboard: Users can view harvested credentials, configure new campaigns, and rotate domains
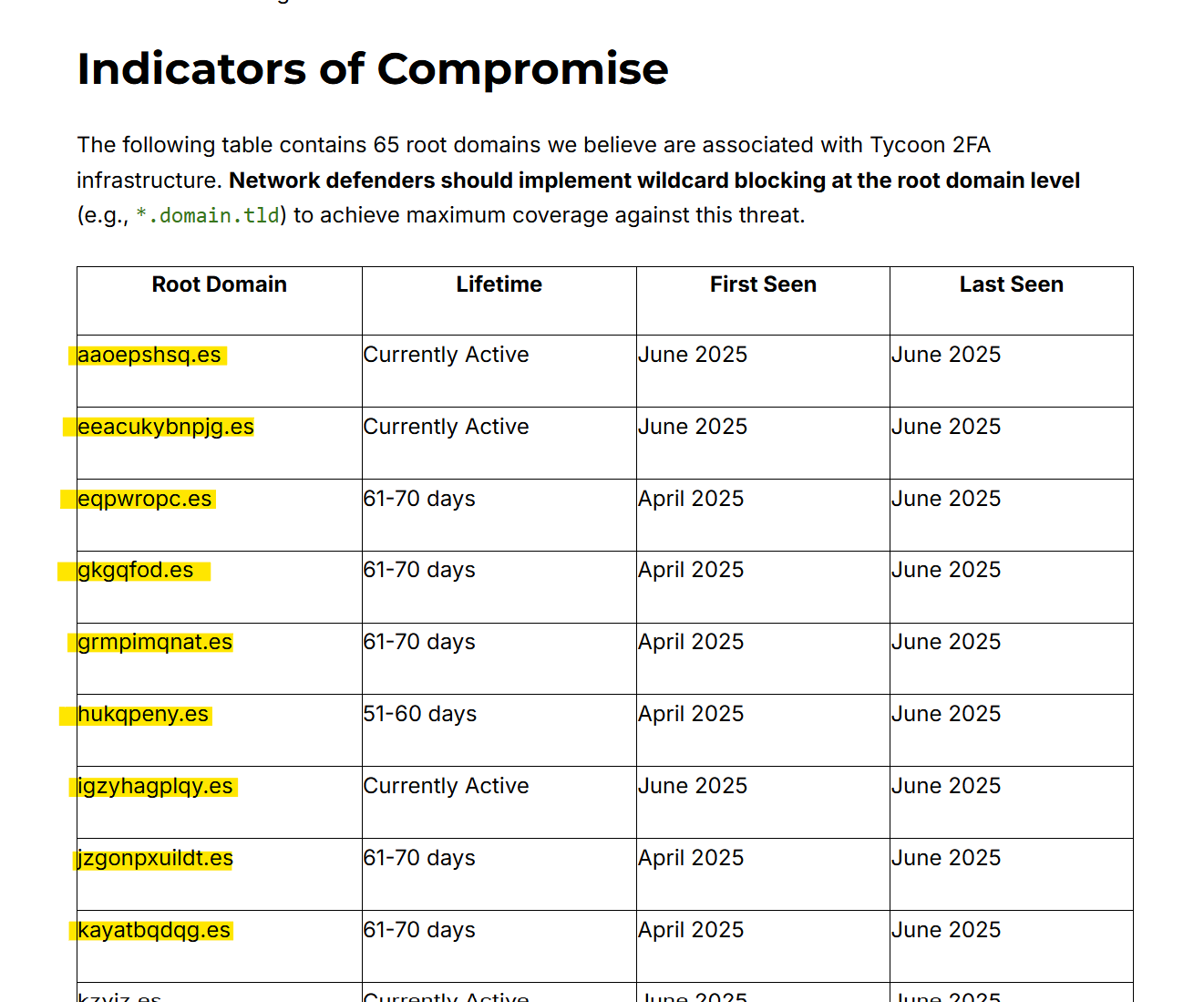
- Infrastructure at scale: DNSFilter reported at least 65 root domains tied to Tycoon infrastructure (DNSFilter, 2025)
- Coordinated Expansion into Spanish (.es) Domains: DNS Filter reported an operational surge in .es infrastructure starting April 7,2025 (DNSFilter, 2025). This significant increase represents a more intensive subdomain generation compared to other top TLD in recent months for this campaign
- Resilience through automation: New infrastructure is spun up regularly to evade takedowns
- Support and feature development: Frequent updates to maintain evasion and effectiveness (AnyRun, 2025)
Sneaky 2FA
Sneaky 2FA follows a more exclusive and stealth focused operational model. It is not broadly advertised or sold in public marketplaces. Instead, it appears to be distributed privately or used by a smaller number of actors.
Operational characteristics include:
- Private or invite only distribution, limiting access to vetted actors
- High value targeting: Prioritizes corporate credentials, especially those linked to administrator or SaaS access
- Short lived infrastructure: Many domains are live for only a few days, with limited overlap (Sekoia, 2025)
- Evasion by design: Built-in cloaking and anti-analysis features make Sneaky 2FA harder to detect and attribute (Sekoia, 2025)
Centripetal’s Perspective
Centripetal has been closely monitoring the evolution of the Tycoon and Sneaky 2FA phishing campaigns. While Tycoon 2FA, a more robust adversary in the middle (AiTM) operation, has demonstrated broader distribution and higher operational sophistication, Sneaky 2FA continues to surface across various threat actor infrastructures.
For this analysis, we reviewed over 170 Sneaky 2FA IOCs sourced from GitHub repositories maintained by eSentire and Sekoia. In parallel, we examined 306 Tycoon related IOCs from the same repositories, supplemented by an additional feed from DNSFilter that included some of the most recent top level domains leveraged in the campaign.
This section compares the Sneaky 2FA and Tycoon 2FA campaigns using the IOCs referenced in this report, focusing on Centripetal’s 2025 coverage, preferred registrars, domain detection timeframes, and top-level domain usage. The goal is to supplement internal findings with additional context from external sources.
Domain Detection Time Frame
The initial analysis of the timeframe between domain creation and first appearance in CTI for the Sneaky 2FA campaign shows an average of 113 days for domains not previously identified in Centripetal’s threat intelligence. Notably, over 32% of these IOCs went undetected for more than 90 days before being aggregated into threat intelligence datasets.
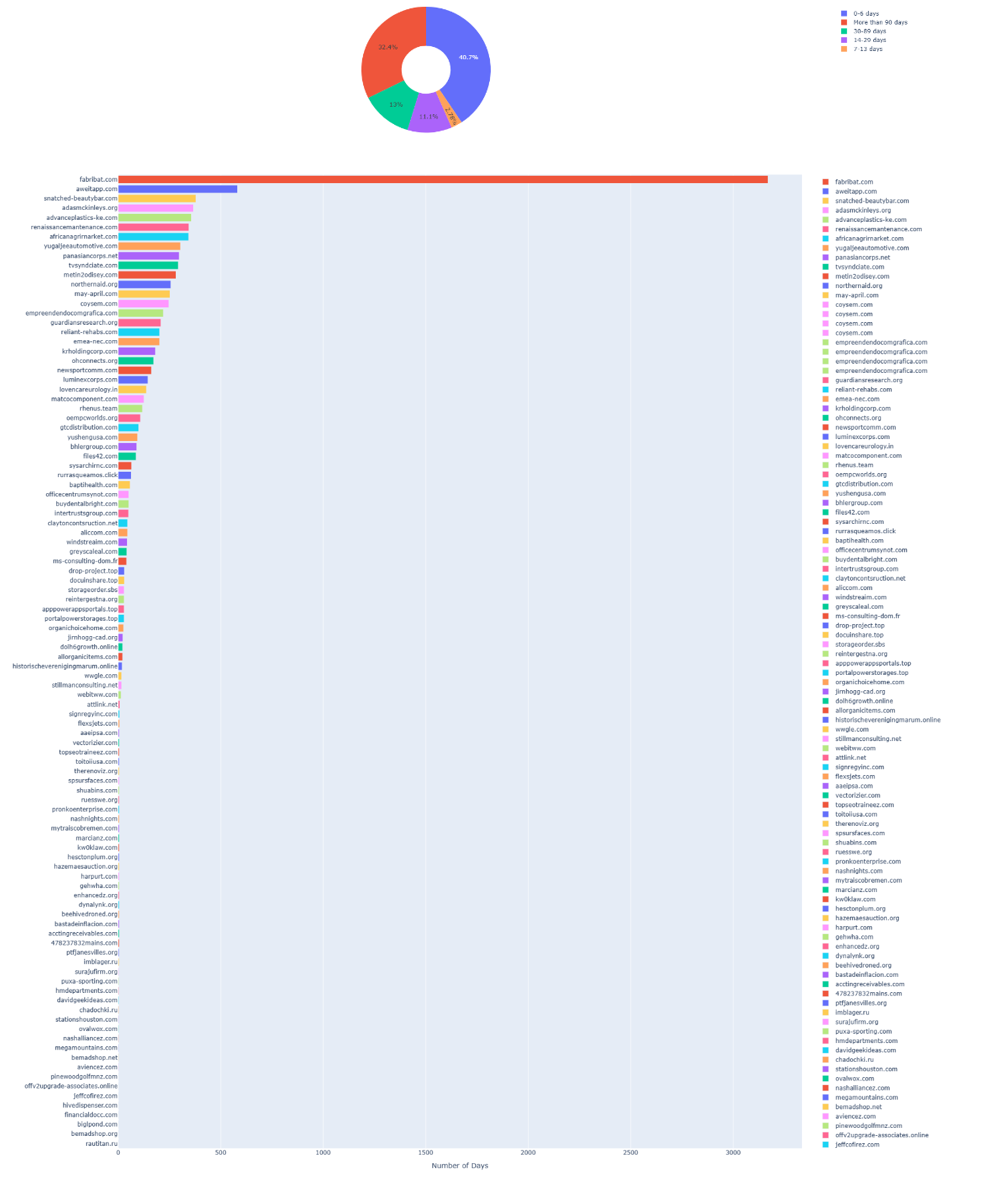
The notable trigger domain driving the higher average in this analysis is fabribat[.]com (Figure 3), a 9 year old domain that illustrates the reuse of aged infrastructure commonly observed in phishing campaigns. Historical records show that although the domain is mature, it was originally created in 2017 to impersonate an Ecuadorian battery business. (Figure 5)
In comparison, the legitimate business domain (Figure 4) is 22 years old, with no evident ties to fabribat[.]com in terms of registrant information or other ownership details. Historical snapshots of fabribat[.]com (Figure 5) show that it hosted content for only a short period, suggesting it was unweaponized or dormant for much of its lifetime. This pattern aligns with recycled phishing infrastructure that is cycled through multiple campaigns, often evading detection, particularly when the domain remains inactive between operations.


This tactic, frequently observed in the Sneaky 2FA campaign, allows threat actors to significantly extend the operational lifetime of their domains and evade detection by most security analysis tools and automated sandboxes. By keeping infrastructure dormant or serving only benign content until shortly before launch, actors minimize their exposure in threat intelligence datasets and reputation feeds. Once activated, these domains often deliver short high impact phishing bursts, frequently gated behind bot detection and geofencing to conceal malicious content from automated crawlers, before being cycled out of use, as shown in domain activity data from DomainTools history (Figure 6). The rotation of such infrastructure, combined with the reuse of aged or previously legitimate domains, makes them considerably more difficult to correlate and track across related campaigns.
This finding reinforces our assessment of Sneaky 2FA as a more targeted and stealthier campaign, using brief, controlled activity windows to evade detection and extend infrastructure lifespan. This contrasts with the higher volume, more detectable operations of Tycoon 2FA.
For Tycoon 2FA, the average time from domain creation to first appearance in CTI is 35 days. While the dataset analyzed for Tycoon is significantly larger than that of Sneaky 2FA, an important factor influencing the average, it is notable that the longest period a Tycoon domain went unflagged in threat intelligence was just over 300 days, compared to more than 3,000 days in the Sneaky 2FA analysis. Additionally, only 9.63% of Tycoon IOCs were first observed in CTI more than 90 days after creation, compared to 32.4% in the previous Sneaky 2FA analysis. (Figure 7)
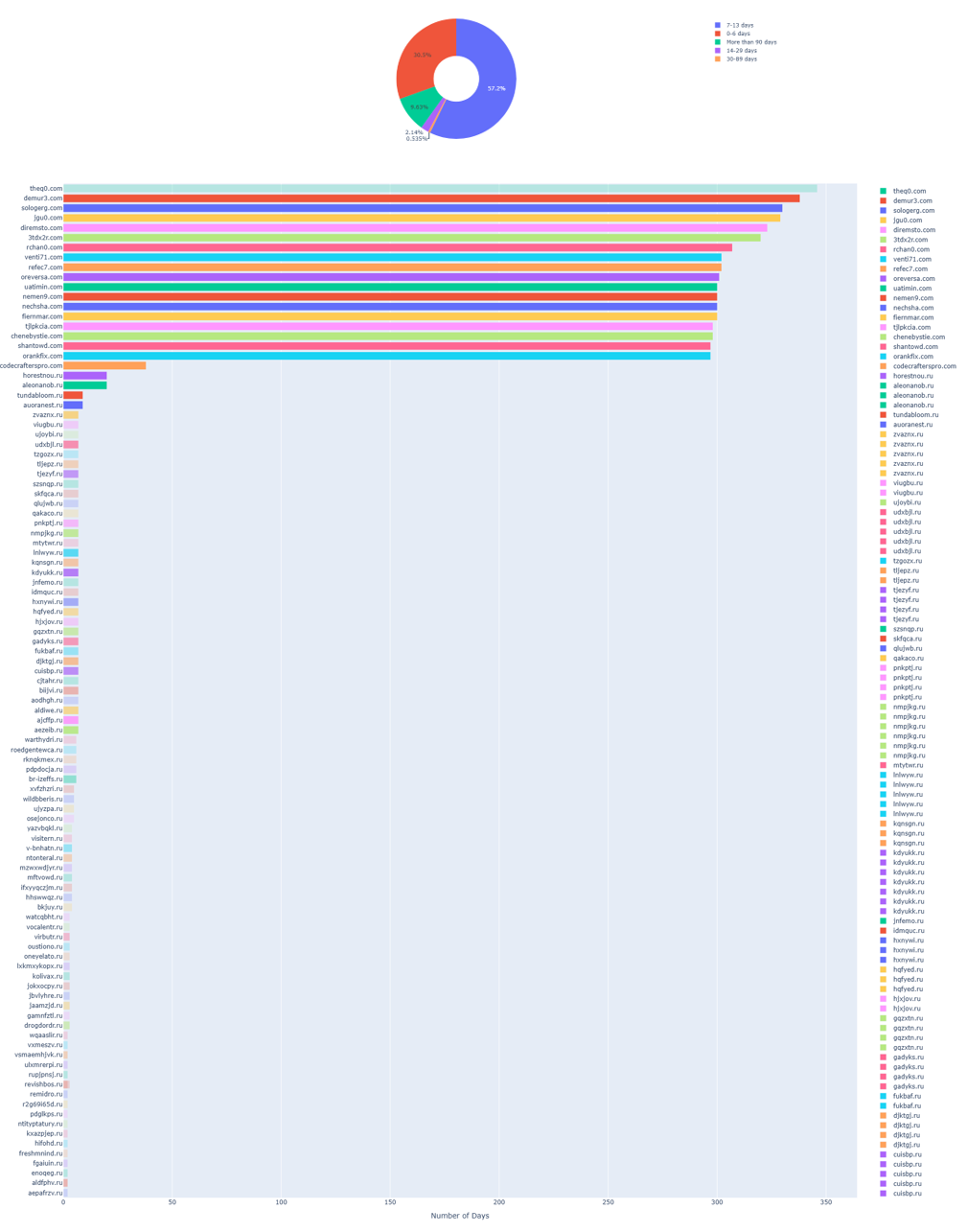
The vast majority of IOCs for this campaign are identified in threat intelligence feeds shortly after creation, driven by the short-lived domain strategy employed. These domains are typically registered in bulk, often following a domain generation algorithm (DGA) pattern, and make use of burnable fully qualified domain names (FQDNs). A notable example of this trend was documented by DNSFilter, which shared a list of recent IOCs highlighting the campaign’s shift toward the Spanish (.es) top-level domain (Figure 8). Such strategies commonly trigger “pattern-matching rules” within threat intelligence platforms, enabling the rapid identification of newly registered domains that match known Tycoon templates.
Registrar Trends
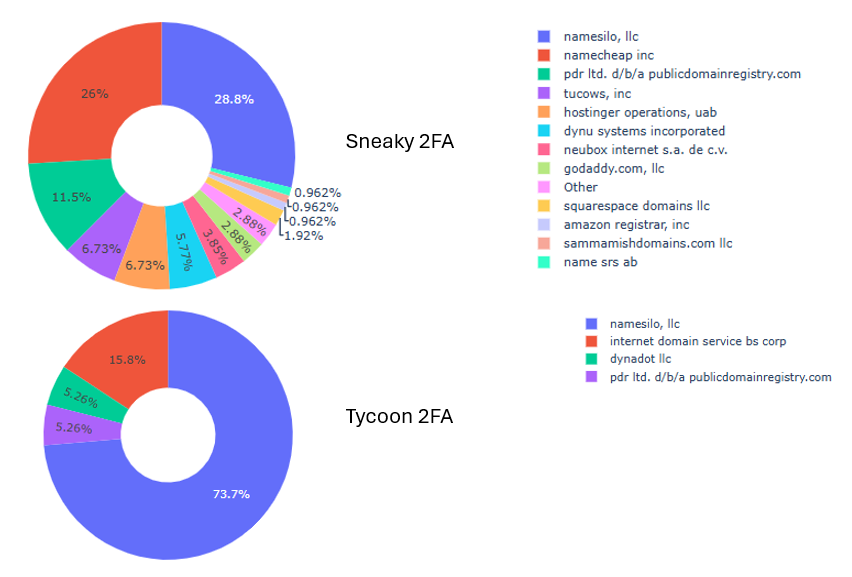
Namesilo LLC emerges as the most frequently used registrar for both campaigns, comprising 28.8% of Sneaky 2FA domains and 73.7% of Tycoon 2FA domains, as shown in figure 9 below. This indicates a strong preference for Namesilo in both operations.
Registrar Profile: Namesilo LLC is an ICANN-accredited American domain registrar, founded in 2010 and managing over 3 million active domains by late 2019, placing it among the top global registrars.
Attraction Factors for Adversaries:
- Offers low pricing, no hidden fees, and free WHOIS privacy, making bulk domain registration cost-effective and more private (namesilo)
- Provides anti-abuse tools such as Domain Defender, transfer locks, account monitoring, and DNSSEC support, which may help adversaries manage infrastructure while delaying detection (namesilo)
Top Level Domains
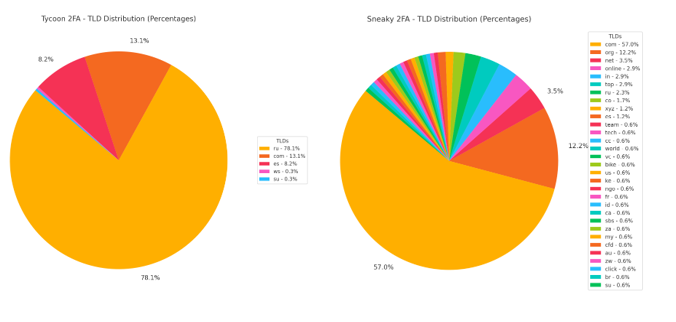
Figure 10 shows distinct TLD preferences across the two campaigns. For Tycoon 2FA, the top three TLDs are .ru first, followed by .com and .es. The heavy use of .ru is notable, as this TLD belongs to a country under U.S. sanctions, often resulting in immediate or near immediate blocking by many organizations and security providers. According to KnowBe4 Threat Lab (KnowBe4, 2025), there was a 98% spike in phishing campaigns leveraging .ru domains between December 2024 and January 2025, with over 1,500 unique malicious .ru domains identified. Many of these domains were hosted by bullet proof providers that ignore abuse reports, enabling long dwell times and sustained campaign operations. This makes .ru domains especially attractive for phishing operators seeking to remain online longer and complicate attribution efforts. While the use of .ru domains can sometimes indicate infrastructure linked to Eastern Europe, it’s important to emphasize that TLD usage alone is not a reliable indicator of attribution for these two campaigns. The inclusion of .es reflects a recent shift in Tycoon’s infrastructure, as mentioned earlier, where this ccTLD has been increasingly leveraged to diversify domain registrations and bypass TLD based blocking.
For Sneaky 2FA, the top three are .com, .org, and .net, reflecting a preference for broadly trusted, mainstream TLDs that can blend more easily into legitimate traffic.
Overall, Tycoon’s concentration on .ru suggests a high-risk, high-volume model with predictable blocking patterns, while Sneaky’s approach favors persistence through reputable TLDs and a more balanced distribution.
Campaign Traffic Comparison
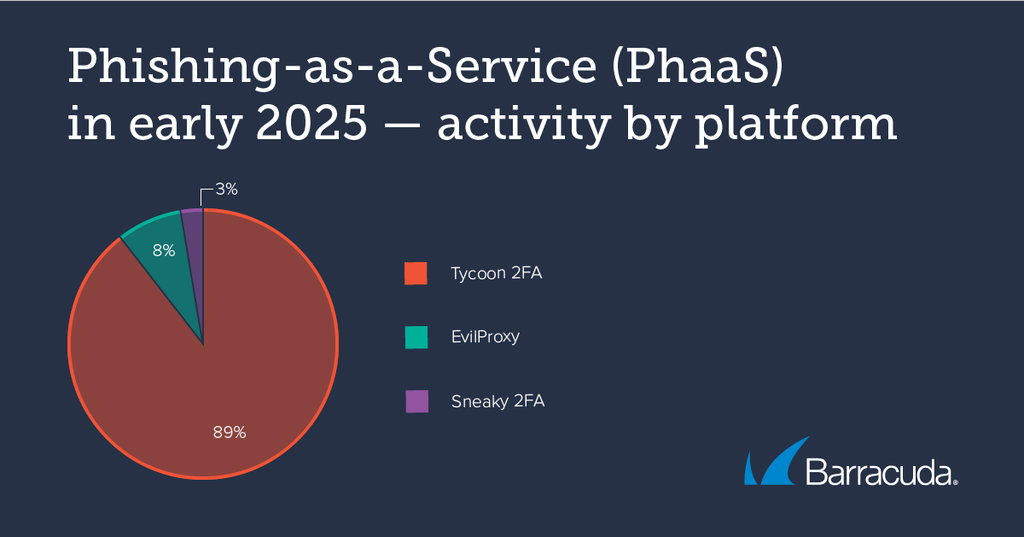
A report by Barracuda (Barracuda,2025) on phishing-as-a-service (PhaaS) attacks highlighted a sharp increase in early 2025, with PhaaS campaigns accounting for the majority of incidents observed in January. According to Barracuda, more than 89% of these incidents were attributed to Tycoon 2FA, 8% to EvilProxy (another PhaaS tool), and 3% to Sneaky 2FA (Figure 11).
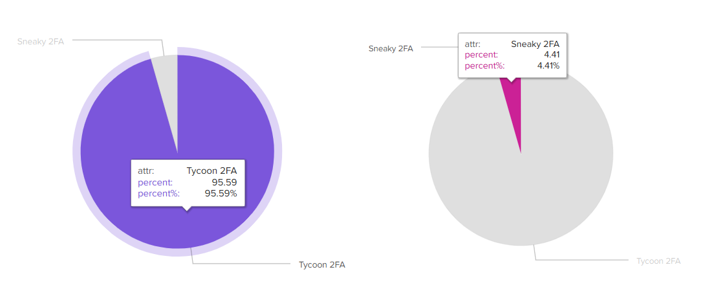
We conducted a separate internal analysis to determine how much of this information remains valid as of August 2025. Our findings align with Barracuda’s report, showing that Tycoon 2FA accounted for 95.59% of all observed events and findings, while Sneaky 2FA represented 4.41% across Centripetal’s customer base. This evidentiary data confirms that Sneaky 2FA continues to be actively leveraged in high-profile, low volume spear phishing campaigns and is operating as originally intended. (Figure 12)
Centripetal’s Coverage
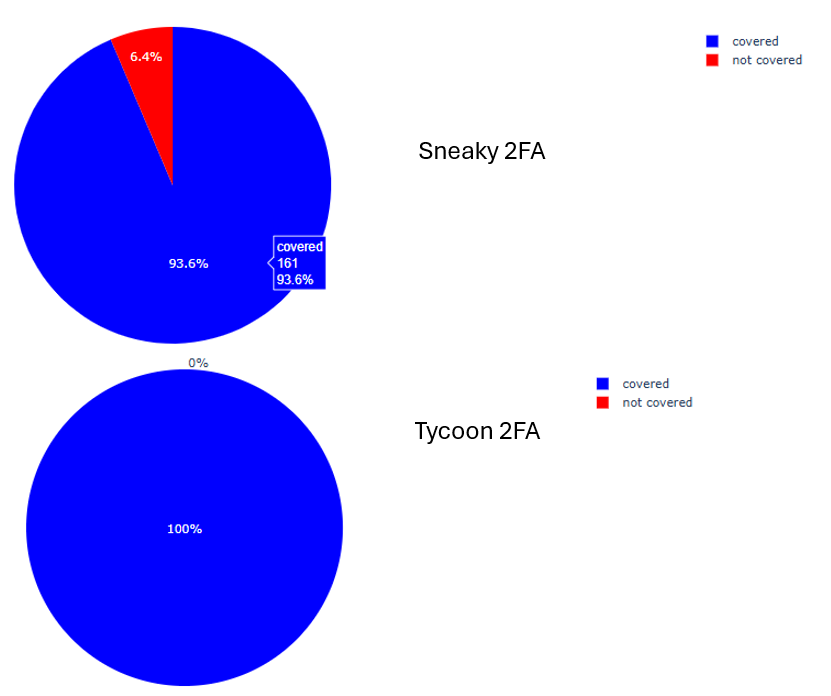
Centripetal’s threat intelligence coverage for the Sneaky 2FA and Tycoon 2FA IOCs referenced in this report for 2025 shows a notable disparity between the two campaigns. Sneaky 2FA maintained a high coverage rate of 93.6%, with 6.4% of IOCs not covered at the time of sampling. Although there are some IOCs identified as not covered in the Sneaky 2FA campaign, the low percentage of recorded findings suggests minimal impact on overall detection capability. In contrast, Tycoon 2FA achieved full coverage, with 100% of identified IOCs included in Centripetal’s detection scope. These findings indicate consistently strong visibility for both campaigns, though a small portion of Sneaky 2FA infrastructure remained outside immediate coverage. (Figure 13)
The Tycoon 2FA and Sneaky 2FA campaigns illustrate two distinct but equally dangerous models of AiTM-enabled phishing. Tycoon 2FA thrives on scale, automation, and predictable infrastructure patterns, making it more visible but also more prolific, while Sneaky 2FA prioritizes stealth, aged infrastructure reuse, and selective targeting to evade detection for extended periods. Centripetal’s analysis confirms strong coverage for both campaigns, with Tycoon achieving complete detection and Sneaky maintaining high visibility despite its evasive approach. Centripetal will continue to closely monitor both operations for any shifts in infrastructure, targeting, or tactics to ensure timely detection by CleanINTERNET service and maintain proactive protection for our customers against evolving AiTM phishing threats.
Centripetal is also pleased to offer Penetration Testing and Vulnerability Assessment services to help organizations identify vulnerabilities and reduce risk. If interested, please contact our Professional Services team at profservs@centripetal.ai or reach out to your Centripetal Account Representative.
Resources
- Barracuda - Threat Spotlight: A million phishing-as-a-service attacks in two months highlight a fast-evolving threat
- NordPass - Phishing-as-a-service: like car rental for smugglers
- SOCRadar - Tycoon 2FA: An Evolving Phishing Kit Powering PhaaS Threats
- Infosecurity Magazine - Sneaky 2FA Joins Tycoon 2FA and EvilProxy in 2025 Phishing Surge
- PR Newswire - DNSFilter Research Warns Tycoon 2FA Expanding Phishing-as-a-Service Operation
- DNSFilter - Tycoon 2FA Infrastructure Expansion: A DNS Perspective, and Release of 65 Root Domain IOCs
- ANYRUN - Evolution of Tycoon 2FA Defense Evasion Mechanisms: Analysis and Timeline
- GitHub - Sneaky & Tycoon IOCs Repo (Esentire)
- GitHub - Sneaky & Tycoon IOCs Repo (Sekoia)
- Sekoia - Sneaky 2FA: exposing a new AiTM Phishing-as-a-Service
- ESENTIRE - Your MFA Is No Match for Sneaky2FA
- Domain Tools - Fabribat[.]com domain information
- Namesilo - Domains, cheap, easy and secure
- knowbe4 - 98% Spike in Phishing Campaigns Leveraging Russian (.ru) Domains.
Know what’s coming. Stop what’s next.
Sign up for our free threat alert bulletin service here.
The Cybercrime Barrier Your Organization Deserves
Sign up for a custom demonstration from our security team of how we bring together the best minds and most complete collection of threat intelligence to provide you with a shocking level of relief.