React2Shell: Critical RCE in React Server Functions Enables Full Remote Code Execution
December 9, 2025
By Aileen Ward

React Server Functions was observed to have a critical remote code execution vulnerability (RCE) with a CVSS of 10.0. This RCE vulnerability has since been patched with React 19.2.1. React Server Functions facilitate remote function calls, translating client requests into server-bound HTTP requests and back into function executions. However, an unauthenticated attacker can exploit a vulnerability in this deserialization process. By sending a maliciously crafted HTTP request to any Server Function endpoint, the attacker can achieve RCE on the server. This vulnerability initially had two separate submissions, CVE-2025-55182 (known as React2Shell) and CVE-2025-66478, however CVE-2025-66478 has since been closed as a duplicate.
Vulnerability Type (CWE)
CWE-502: Deserialization of Untrusted Data
Deserialization of client-provided data is performed without adequate validation, potentially allowing malformed or unsafe objects to be processed.
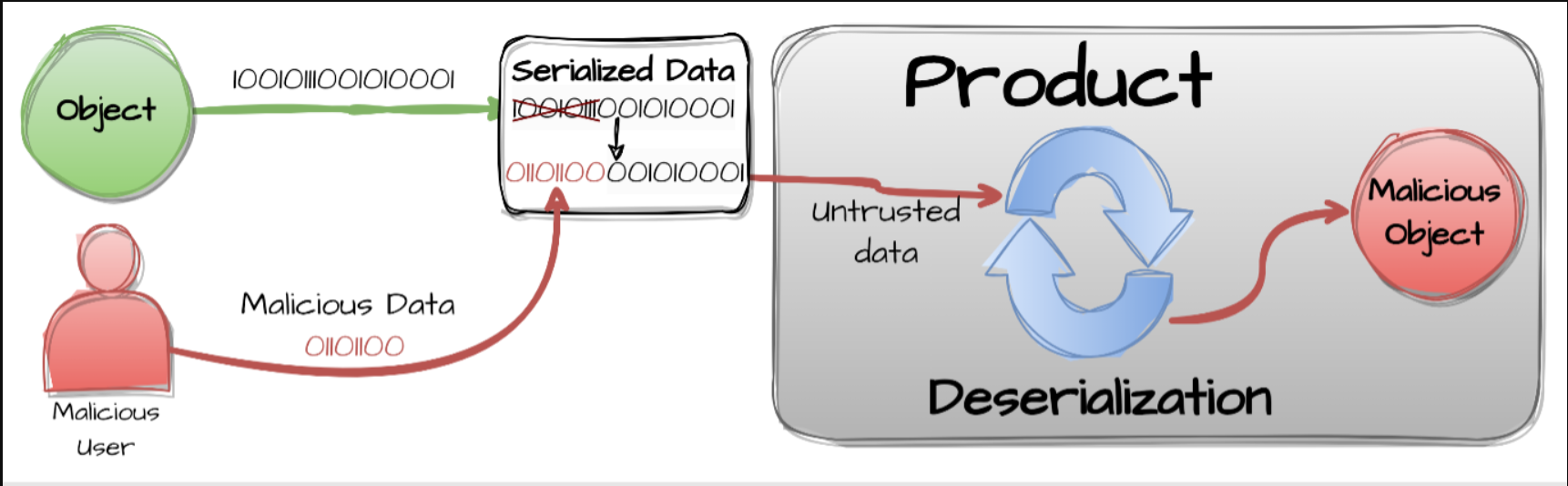
CVE-2025-55182
CVSS Score: 3.1
Base Score: 10 (Critical)
Attack Vector: (AV:N)
Attack Complexity: (AC:L)
Privileges Required: (PR:N)
**User Interaction: (**UI:N)
Scope: (S:C)
Impact on CIA:
- Confidentiality: High (C:H)
- Integrity: High (I:H)
- Availability: High (A:H)
CVE-2025-66478
Rejected by CVE as it is a duplicate of CVE-2025-55182. (CVE, 2025)
Impacted Versions
| Package Name | Vulnerable Versions | Fixed/Patched Versions (Minimum Upgrade) |
|---|---|---|
react-server-dom-webpack | 19.0, 19.1.0, 19.1.1, 19.2.0 | > 19.2.1 |
react-server-dom-parcel | 19.0, 19.1.0, 19.1.1, 19.2.0 | > 19.2.1 |
react-server-dom-turbopack | 19.0, 19.1.0, 19.1.1, 19.2.0 | > 19.2.1 |
In addition to the Impacted Versions above there were React frameworks and bundlers affected due to their dependency structure. Specifically their direct, peer, or bundled versions of the vulnerable React packages.
Note that simply enabling support for React Server Components is sufficient to make an application vulnerable, regardless of whether server functions are actively used. (React, 2025)
Mitigation Steps
To mitigate the Remote Code Execution (RCE) vulnerability stemming from React Server Components, apply the following package updates immediately based on the framework or tool you are using.
Node.js Users
| Next.js Release Line | Mitigation Command |
|---|---|
| 15.0.x | npm install next@15.0.5 |
| 15.0.x | npm install next@15.1.9 |
| 15.0.x | npm install next@15.2.6 |
| 15.0.x | npm install next@15.3.6 |
| 15.0.x | npm install next@15.4.8 |
| 15.5.x | npm install next@15.5.7 |
| 16.0.x | npm install next@16.0.7 |
| Canary Releases | If using Next.js 14.3.0-canary.77 or later, downgrade to the latest stable 14.x release: npm install next@14 |
React Router
If using React Router's unstable RSC APIs, update all related dependencies to their latest stable versions.
npm install react@latest react-dom@latest react-server-dom-parcel@latest react-server-dom-webpack@latest @vitejs/plugin-rsc@latest
Frameworks and Specific Packages
If using the other affected frameworks or core packages.
| Affected Tool / Package | Mitigation Command |
|---|---|
| Expo | npm install react@latest react-dom@latest react-server-dom-webpack@latest |
| Redwood SDK (rwsdk) | Ensure you are on rwsdk>=1.0.0-alpha.0. For the latest beta version and RSC dependencies: npm install rwsdk@latest npm install react@latest react-dom@latest react-server-dom-webpack@latest |
| Waku | npm install react@latest react-dom@latest react-server-dom-webpack@latest waku@latest |
| @vitejs/plugin-rsc | npm install react@latest react-dom@latest @vitejs/plugin-rsc@latest |
| react-server-dom-parcel | npm install react@latest react-dom@latest react-server-dom-parcel@latest |
| react-server-dom-turbopack | npm install react@latest react-dom@latest react-server-dom-turbopack@latest |
| react-server-dom-webpack | npm install react@latest react-dom@latest react-server-dom-webpack@latest |
Exploit Process
Proof-of-concepts (PoCs) have been published relating to this CVE. The exploitation of this vulnerability has followed a systematic and opportunistic structure with attributes that correlate the activity with state-sponsored threat actors. (Amazon, 2025). Their multi-stage methodology for exploitation observed:
- Automated Scanning The use of these automated scanning tools is used for broad-spectrum vulnerability detection and is leveraged in conjunction with a number of anti-detection techniques like user-agent randomization for the evasion of security monitoring.
- Targeted Debugging Specific threat clusters follow up automated scans with active, manual exploitation and debugging against vulnerable targets. This involves persistent, extended attempts to refine attack payloads, including attempts to execute Linux commands, write files and read sensitive system files.
- Vulnerability Daisy-Chaining Concurrent exploitation of other 0 and N-day vulnerabilities were observed by Amazon threat intelligence teams to enhance the successful exploitation of vulnerable targets. (Amazon, 2025)
Suspected Exploiting Threat Actors
Threat actors appear to have prioritized the rapid weaponization of any available exploit, leading to high-volume scanning with flawed public PoCs for speed over accuracy. This volume-based approach generates significant log noise that can be leveraged to mask more sophisticated and persistent attacks aimed at bypassing security controls.
It is suspected that there is a state-sponsored element to the exploitation of CVE-2025-55182. Analysis from multiple sources observed the use of historically malicious infrastructure by PRC-nexus threat actors like Earth Lamia and Jackpot Panda. The large-scale use of shared anonymization networks and the Chinese-associated ASN infrastructure further this attribution. (Amazon, 2025) GreyNoise have observed 56 associated IPs with this vulnerability's exploitation and their data reflects this observation. (GreyNoise, 2025)
Earth Lamia
A Chinese state-sponsored threat actor active since 2023, primarily targets organizations in the finance, logistics, retail, IT, education, and government sectors across Brazil, India, and Southeast Asia. The group's operational methods include exploiting publicly known vulnerabilities.
Jackpot Panda
Active throughout 2023 and into 2025, the China-nexus threat actor JACKPOT PANDA has evolved its operations, moving from deploying sophisticated trojanized executables with custom malware like the CplRAT-related XShade implant, to exploiting supply chain vulnerabilities. The group consistently exploits trusted relationships and newly disclosed flaws. Their tactics include exploitation of public-facing applications and client execution methods.
IOCs
Network-based:
- Malicious HTTP POST Requests Observed HTTP POST requests targeting application endpoints that include specific, potentially triggering, HTTP headers like
next-actionorrsc-action-id. - Command Injection Patterns Request bodies within these POST requests contained anomalous patterns, specifically the $@ string, which is often used in attempts at command injection or exploitation.
- Suspicious Response Patterns Request bodies exhibited the pattern
"status":"resolved_model", which could indicate a specific response or status message related to the malicious activity or exploit payload execution.
Host-based:
- Unexpected Reconnaissance Commands Execution of common system reconnaissance commands (
whoami,id,uname) originating from unexpected sources or contexts, suggesting the attacker is attempting to map the compromised environment. - Sensitive File Access Attempts to read the
etc/passwdfile, a key step in gathering system user information for potential privilege escalation or lateral movement. - Suspicious File Writes The creation of new, unexpected files in the volatile
/tmp/directory (e.g., a file namedpwned.txt), which often serves as a staging area for malicious tools or results. - Anomalous Process Spawning The appearance of new, unauthorized child processes that were initiated by the typically constrained Node.js/React application processes, indicating successful code execution or compromise of the application layer.
Infrastructure:
GreyNoise have tagged multiple IPs associated with the exploitation of this vulnerability. They can be found here: GreyNoise, 2025 . Additionally AWS stated threat actor infrastructure used as:
IP Address, Date of Activity, Attribution
206[.]237.3.150, 2025-12-04, Earth Lamia
45[.]77.33.136, 2025-12-04, Jackpot Panda
143[.]198.92.82, 2025-12-04, Anonymization Network
183[.]6.80.214, 2025-12-04, Unattributed threat cluster
CVE-2025-55182 presents a significant risk to organizations who run React v19 or React Server, it is paramount to clarify what version the organizations running and if it is public facing and remediate according to React’s advisories.
Centripetal is also pleased to offer Penetration Testing and Vulnerability Assessment services to help organizations identify vulnerabilities and reduce risk. If interested, please contact our Professional Services team at profservs@centripetal.ai or reach out to your Centripetal Account Representative.
Resources
- https://react.dev/blog/2025/12/03/critical-security-vulnerability-in-react-server-components
- https://www.aikido.dev/blog/react-nextjs-cve-2025-55182-rce
- https://www.tenable.com/blog/react2shell-cve-2025-55182-react-server-components-rce
- https://www.helpnetsecurity.com/2025/12/04/react-node-js-vulnerability-cve-2025-55182/
- https://cloud.google.com/blog/products/identity-security/responding-to-cve-2025-55182
- https://socket.dev/blog/critical-security-vulnerability-in-react-server-components
- https://slcyber.io/research-center/high-fidelity-detection-mechanism-for-rsc-next-js-rce-cve-2025-55182-cve-2025-66478/
- https://www.tenable.com/cve/CVE-2025-66478
- https://www.tenable.com/cve/CVE-2025-55182
- https://react.dev/blog/2025/12/03/critical-security-vulnerability-in-react-server-components
- https://cwe.mitre.org/data/definitions/502.html
- https://vercel.com/changelog/cve-2025-55182
- https://viz.greynoise.io/query/cve:CVE-2025-55182
- https://react2shell.com/
Know what’s coming. Stop what’s next.
Sign up for our free threat alert bulletin service here.
The Cybercrime Barrier Your Organization Deserves
Sign up for a custom demonstration from our security team of how we bring together the best minds and most complete collection of threat intelligence to provide you with a shocking level of relief.