NPM Compromises Expose Critical Weakness in the Software Supply Chain
September 24, 2025
By Rodrigo Luna
In September of 2025, threat actors once again demonstrated the risk of supply chain attacks by targeting the Node Package Manager (NPM) ecosystem and exploiting the implicit trust developers place in open-source dependencies. Two separate incidents were observed: one involving credential abuse to publish malicious updates to legitimate packages, and another leveraging typosquatting and dependency confusion to deliver trojanized libraries. Both cases highlight the continued exploitation of the software supply chain to gain initial access, exfiltrate sensitive data, and compromise development environments.
Crypto-Focused Supply Chain Attack
The cryptocurrency-focused attack on September 8, 2025, was first identified after Aikido’s intelligence feed flagged a cluster of malicious packages being pushed to NPM. Analysis revealed the intrusion began with a phishing email impersonating NPMJS support, sent to reputable maintainer Josh Junon (Qix). The lure prompted a fraudulent account security update, leading to stolen credentials and compromise of his NPM account.
With this access, the attacker published multiple malicious package versions containing code designed to hook browser and wallet APIs. Once installed, the malware monitored transactions, replaced legitimate wallet addresses with attacker-controlled ones, and silently rerouted funds. Although the campaign lasted only a few hours before discovery, it demonstrated how quickly a targeted phishing attack against a single maintainer can escalate into a widespread supply chain compromise with direct financial impact on cryptocurrency users.
Shai-Hulud Worm Attack
The escalation of NPM-focused campaigns continued on September 15, 2025, with the emergence of the Shai-Hulud worm, described by Arctic Wolf as “one of the first self-spreading worms to propagate via the npm ecosystem.” (Arctic Wolf, 2025) Attackers compromised more than 40 developer accounts and published over 700 malicious package versions to the NPM registry (SecurityWeek, 2025).
Unlike prior incidents that relied solely on phishing or credential theft, Shai-Hulud demonstrated worm-like behavior. It spread automatically by leveraging compromised maintainer accounts to infect new packages and expand its reach across the ecosystem. The malicious packages contained obfuscated payloads designed to harvest developer credentials, exfiltrate environment variables, and implant persistence mechanisms within build pipelines.
The scale and automation of this campaign underscore a dangerous shift in supply chain threats from targeted compromises to self-propagating malware capable of cascading rapidly across open-source ecosystems.
The Attack Chain
Crypto-Focused Supply-Chain Attack
The sophisticated malware attack chain is both stealthy and automated. It exploits human perception and technical vulnerabilities by compromising a trusted NPM package, then spreading silently across environments, infecting websites, and stealing funds without raising immediate suspicion.
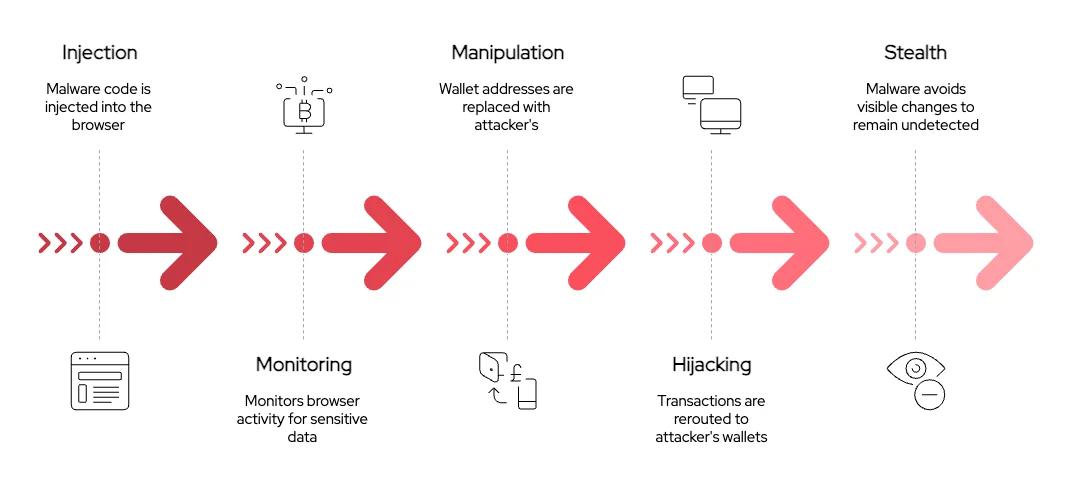
Figure 1 depicts a simplified step by step view of the malware’s behavior, as outlined in an analysis conducted by SOC Radar (SOCRadar, 2025). The following stages were identified:
- Injection The malware injected hooks into browser APIs (
fetch,XMLHttpRequest) and cryptocurrency wallet interfaces to intercept sensitive operations. - Monitoring It inspected network responses and page payloads for cryptocurrency wallet addresses and transaction metadata.
- Manipulation When a valid wallet address was found, the code substituted it with an attacker-controlled lookalike.
- Hijacking Prior to transaction signing, the malware silently rerouted funds or approval flows to the attacker’s wallets.
- Stealth UI changes were suppressed so victims remained unaware of the manipulation.
Shai-Hulud Worm Attack
Multiple security researchers note that the attack structure described here resembles the techniques used by the same actors behind the Nx incident on 27 August 2025. The playbook mirrors that original intrusion but with a key change: the payload has been turned into a worm capable of harvesting secrets such as process.env, TruffleHog style scanning, and cloud metadata endpoints for AWS and GCP credentials, publishing those secrets to GitHub by creating a repo named Shai Hulud and committing JSON dumps, installing a GitHub Actions workflow that serializes toJSON(secrets) and exfiltrates them via an attacker webhook[.]site, and using discovered NPM tokens to enumerate and attempt updates to packages the compromised maintainer controls, finally iterating the victim’s accessible repositories to make them public or add workflows or branches that trigger further leaks. (Aikido, 2025).
The diagram below illustrates the Shai Hulud worm’s attack chain:
- Harvest Scans the host and CI environment for secrets (
process.env, TruffleHog-style scans, and cloud metadata endpoints) to collect credentials and tokens. - Exfiltration (repo) Creates a GitHub repository (Shai-Hulud) under the compromised account and commits JSON dumps containing system info, environment variables, and harvested secrets.
- Exfiltration (Actions) Installs a malicious GitHub Actions workflow that serializes secrets (
toJSON), POSTs them to an attacker webhook[.]site, and leaves encoded copies in the Actions logs. - Propagation Uses discovered NPM tokens to enumerate and attempt updates of packages the victim maintains, leveraging the software supply chain to spread the compromise.
- Amplify Iterates the victim’s accessible repositories to make them public or add workflows/branches that trigger further runs and additional data leaks.
Mitigation Strategies
Crypto-Focused Supply-Chain Attack
The crypto-focused attack lasted for only about two hours from the initial compromise to the deployment of malware in trusted dependencies. Anomaly alerts were triggered when server side errors emerged after repeated attempts by the malware to invoke the fetch() API in Node.js environments. These disruptions to integration workflows prompted early investigation by security teams. Post-discovery strategies have since been shared by multiple security researchers, and several have been compiled from various sources:
Affected Crypto Users
- Disconnect wallets from affected sites.
- Revoke token approvals before moving funds.
- Create a new wallet, back up the seed securely, and transfer assets.
- Monitor wallet activity for suspicious transactions.
Developers / Maintainers
- Audit dependencies for compromised versions and reinstall from lockfiles.
- Rotate/revoke NPM access tokens and enforce MFA on maintainer accounts.
- Remove malicious scripts, pin dependency versions, and commit lockfiles.
- Limit publish permissions and review CI/CD credentials.
Shai-Hulud Worm Attack
The Shai-Hulud worm operated rapidly once it gained a foothold in developer or CI environments. Within a short window, it scanned hosts and pipelines for secrets, committed harvested data into newly created repositories, and deployed malicious GitHub Actions workflows that exfiltrated credentials to attacker-controlled endpoints. Anomaly signals, such as unexpected repository creation, sudden workflow additions, or unusual outbound webhook activity from GitHub Actions prompted accelerated triage by security teams. Following discovery, recommendations from multiple incident responders and researchers were collected and consolidated.
Affected Organizations / Developers
- Revoke and rotate exposed GitHub, NPM, and cloud tokens.
- Audit repos for unauthorized commits, new repos, or suspicious workflows.
- Review GitHub Actions logs for encoded payloads or unexpected outbound POSTs.
- Enforce MFA and least-privilege on all accounts.
CI/CD Security Teams
- Disable or quarantine untrusted workflows and block unknown webhooks.
- Require reviews and signed commits for workflow changes.
- Integrate secret-scanning and policy checks into CI.
- Regularly rotate and scope CI credentials.
Package Maintainers
- Audit and re-publish clean package versions if tampered.
- Revoke/reissue registry tokens; enforce MFA.
- Limit publish permissions and require approvals.
- Pin dependencies and commit lockfiles.
Downstream Consumers
- Validate packages against lockfiles/checksums; pin to known-good versions.
- Monitor for anomalous version bumps or repo changes.
- Treat suspicious repos/logs as potential incident indicators.
- Share IOCs with platforms (GitHub/NPM) and peer organizations.
TTPs & IOCs
Crypto-Focused Supply-Chain Attack
Over 18 NPM packages and versions with over 2 billion weekly downloads were compromised in a crypto-focused supply chain attack according to Sygnia (Sygnia, 2025). A comprehensive appendix containing details on affected versions, targeted wallets, and malware code characteristics is available here.
Additionally, the following indicators of compromise (IOCs) were identified in the same analysis:
Phishing infrastructure
- npmjs[.]help
- 185.7.81[.]108
- support@npmjs[.]help
- static-mw-host.b-cdn[.]net
- img-data-backup.b-cdn[.]net
- websocket-api2.publicvm[.]com
- https://www[.]npmjs[.]help/settings/qix/tfa/manageTfa?action=setup-totp
Shai-Hulud Worm Attack
The number of IOCs linked to this attack is extensive, reflecting the large volume of compromised packages. A complete list published by Reversing Labs (ReversingLabs, 2025). In addition, Checkmarx (Checkmarx, 2025) has highlighted the following IOCs as particularly important to monitor:
- Connections to “
webhook[.]site“ with ID “bb8ca5f6-4175-45d2-b042-fc9ebb8170b7“ - File “
bundle.js“ in a distribution with hash “46faab8ab153fae6e80e7cca38eab363075bb524edd79e42269217a083628f09“ - Presence or loading of a GitHub Actions workflow named like “
shai-hulud-workflow.yml“ - Presence of a repository branch “
shai-hulud“ - Private GitHub repos suddenly becoming public
Centripetal’s Perspective
At Centripetal, we are aware of the significant risk phishing poses across cyber campaigns, and we continuously monitor for emerging phishing threats. These campaigns often serve as the initial gateway, enabling attackers to steal credentials or deliver malicious payloads that pave the way for broader compromise.
The September NPM incidents illustrated this clearly; phishing led to the theft of maintainer credentials, which were then abused to push malicious updates to trusted packages. Detecting and disrupting phishing at an early stage remains one of the most effective ways to prevent downstream impacts such as package tampering, credential abuse, and widespread propagation. This part of the analysis will focus on the tactics, techniques, and procedures (TTPs) used in this initial stage of compromise.
Phishing infrastructure
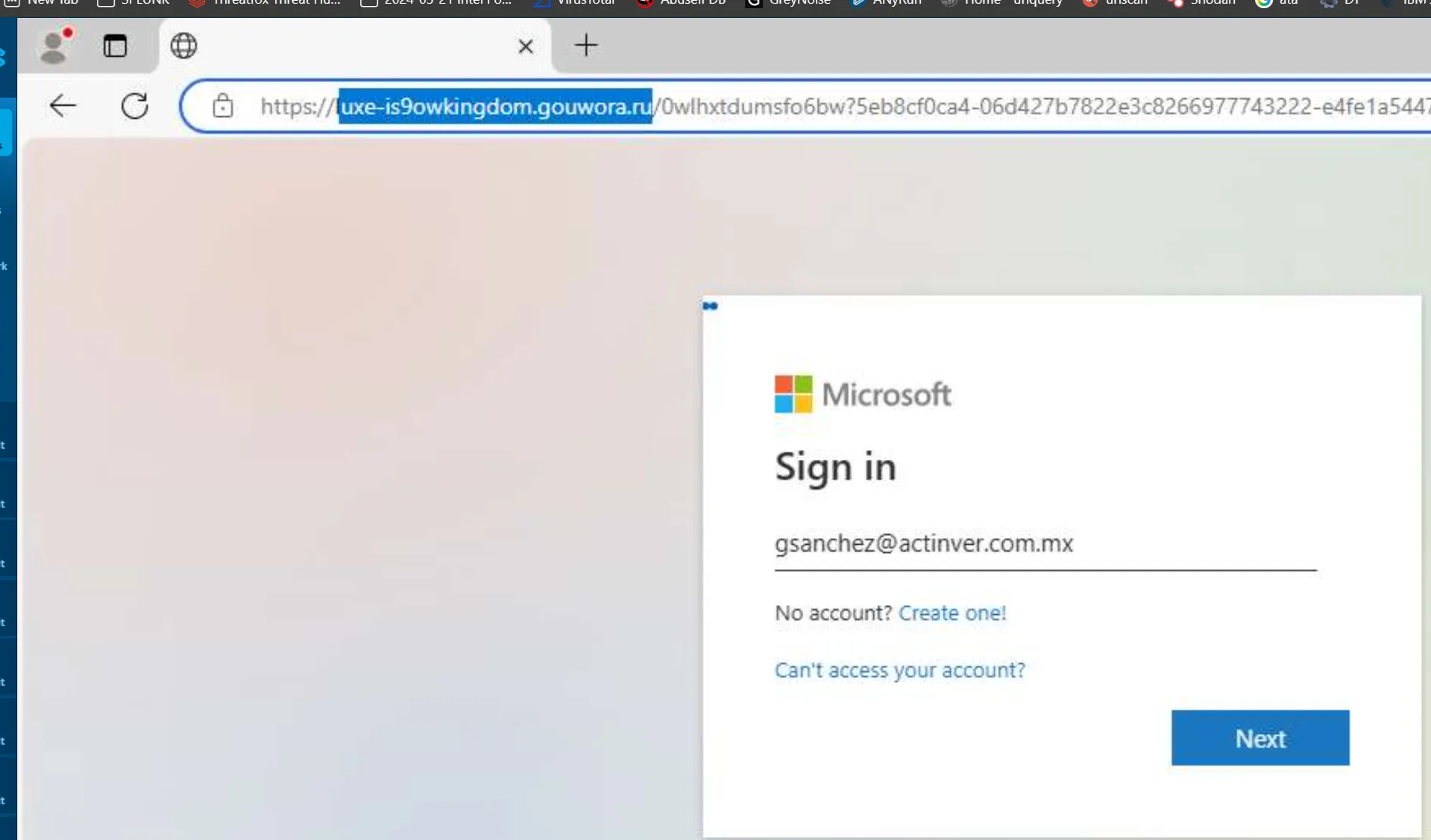
Analysis of the phishing infrastructure behind the cryptocurrency-focused attack observed several documented artifacts after the developer/maintainer, Josh Junon (Qix), publicly confirmed the compromise. One key domain - npmjs[.]help, was used to steal NPM credentials and served content that closely mimicked the legitimate npmjs domain. As shown in Figure 3, the fake domain was nearly indistinguishable from the authentic site, making it easy to confuse at a glance.
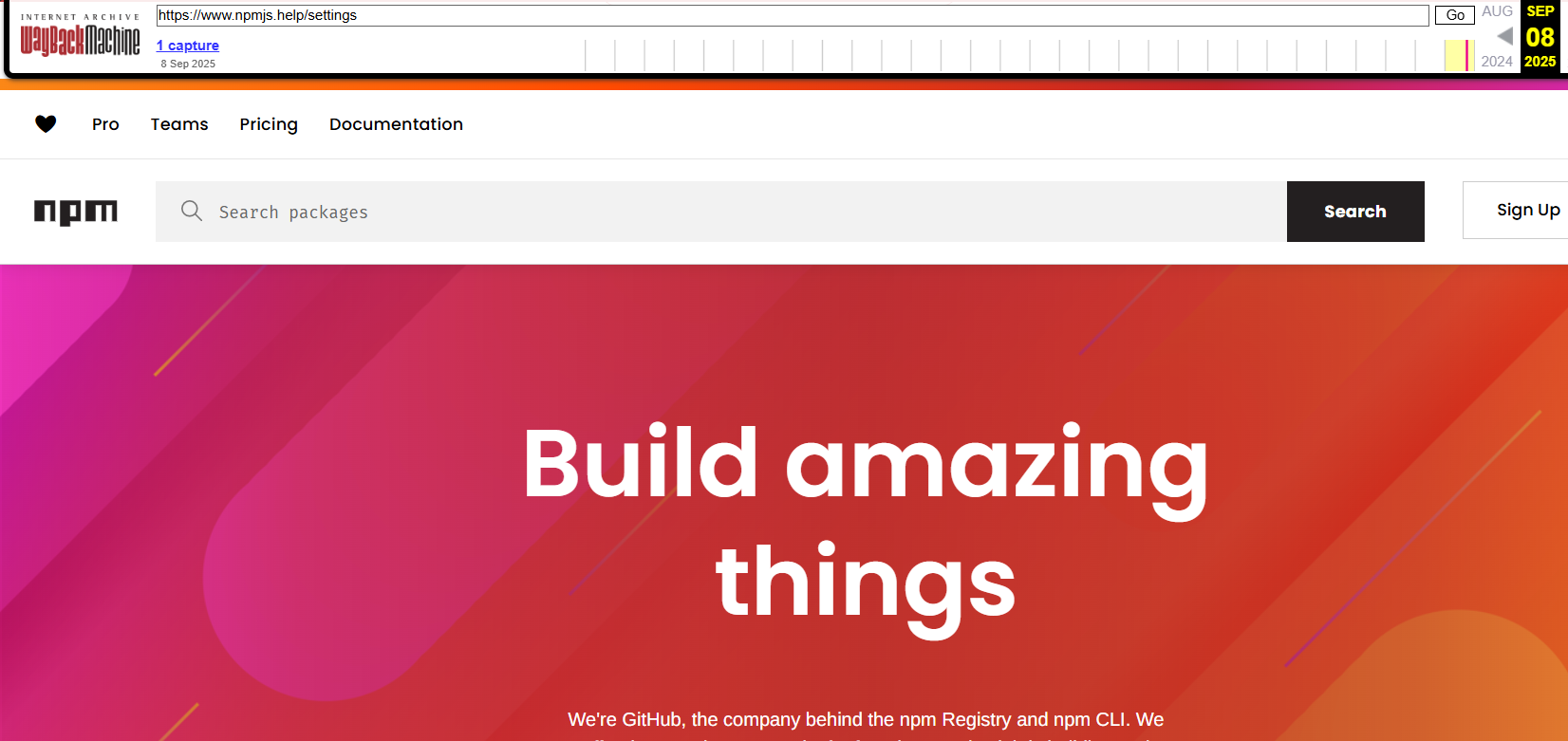
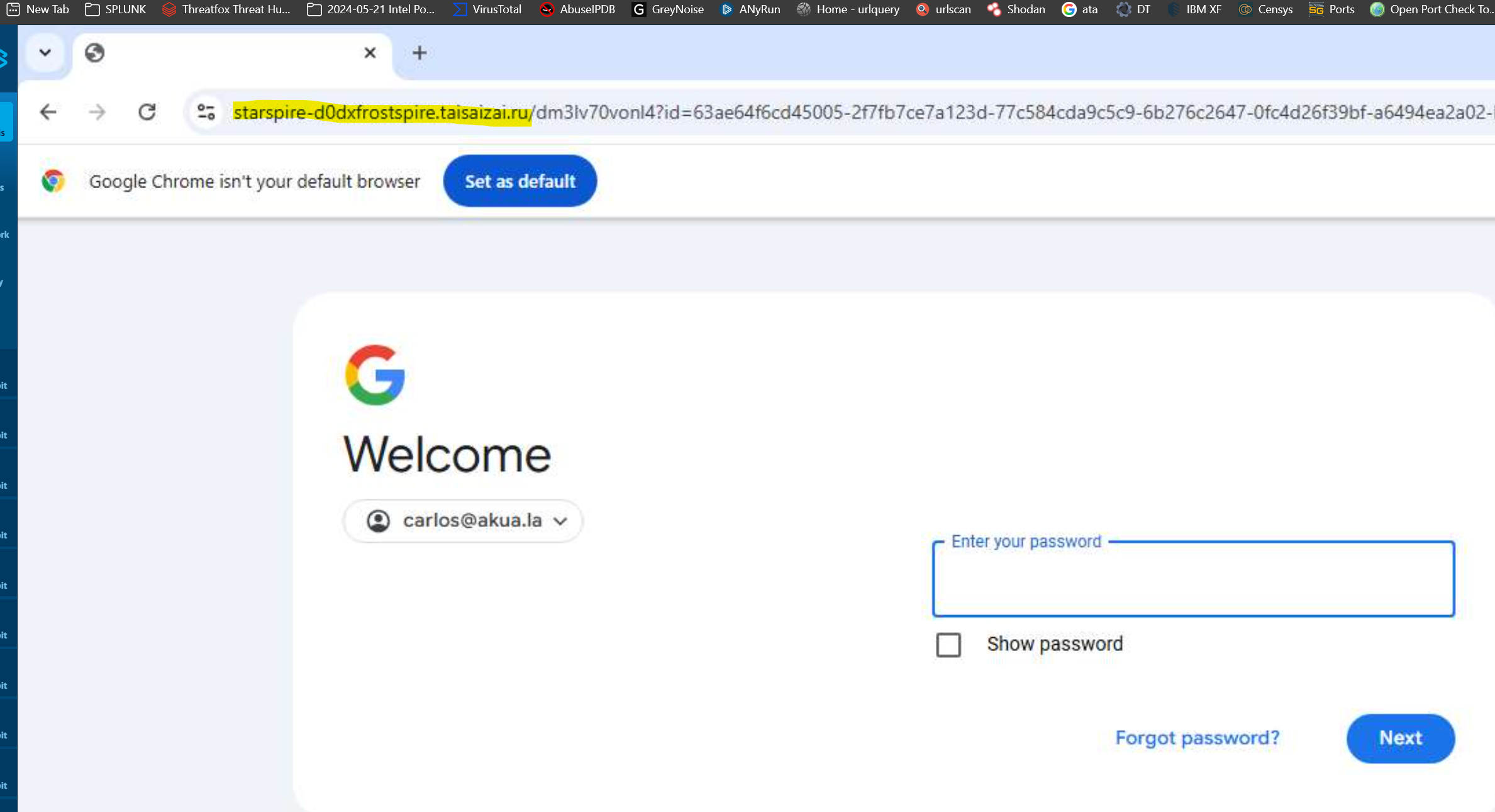
Threat actors are known to impersonate reputable infrastructure providers such as Microsoft and Google in credential harvesting campaigns like Tycoon2FA and Salty2FA. These operations typically follow the same pattern: creating login pages that closely mimic legitimate services in order to intercept credentials in real time.
As shown in Figures 4 and 5, taken from Any.Run’s latest analysis, these pages can appear legitimate at first glance. However, a closer look at the URL reveals that the domains are not owned by Google or Microsoft and are instead hosted on top-level domains (TLDs) that are uncommon for legitimate services.

Domains and Hosting IPs
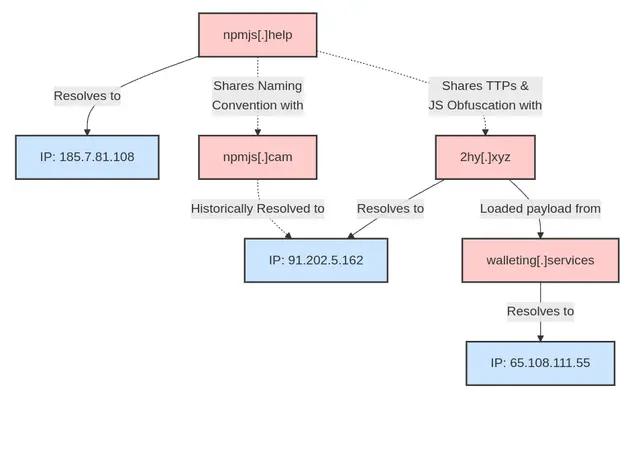
Previous analysis conducted by Security Alliance (SecurityAlliance, 2025) identified two additional domains that were not listed in any of the other public research tied to these attacks. Researchers were able to extract these indicators by examining data traces from npmjs[.]help, and attributed them to the same actor or to a phishing-as-a-service (PhaaS) infrastructure leveraged by similarly motivated threat groups.
To reinforce attribution, researchers noted that:
- The domain registration timelines aligned closely with the other phishing infrastructure already documented (June–September 2025).
- Code artifacts such as obfuscated JavaScript and iframe injections mirrored those observed on npmjs[.]help and 2hy[.]xyz, strengthening the link to the same operator.
- The naming conventions and TLD selections suggested a deliberate effort to mimic trusted services while evading detection.
These additions provide further evidence of a persistent and adaptive phishing campaign, one that not only recycles infrastructure but also extends its scope to target different verticals within the blockchain and developer ecosystems. It also highlights how less-visible domains may play supporting roles in staging or redirecting traffic before users are presented with a spoofed login page. (Figure 6)
It is indicative to say that based on the attack pattern and success, the threat actors behind these two attacks are not malware-focused but rather phishing-oriented operators. Their campaigns consistently relied on credential harvesting, domain impersonation, and malicious iframes, rather than the deployment of complex malware families. This reinforces the hypothesis that the group has limited malware development expertise and instead invests in phishing-as-a-service infrastructure to scale operations.
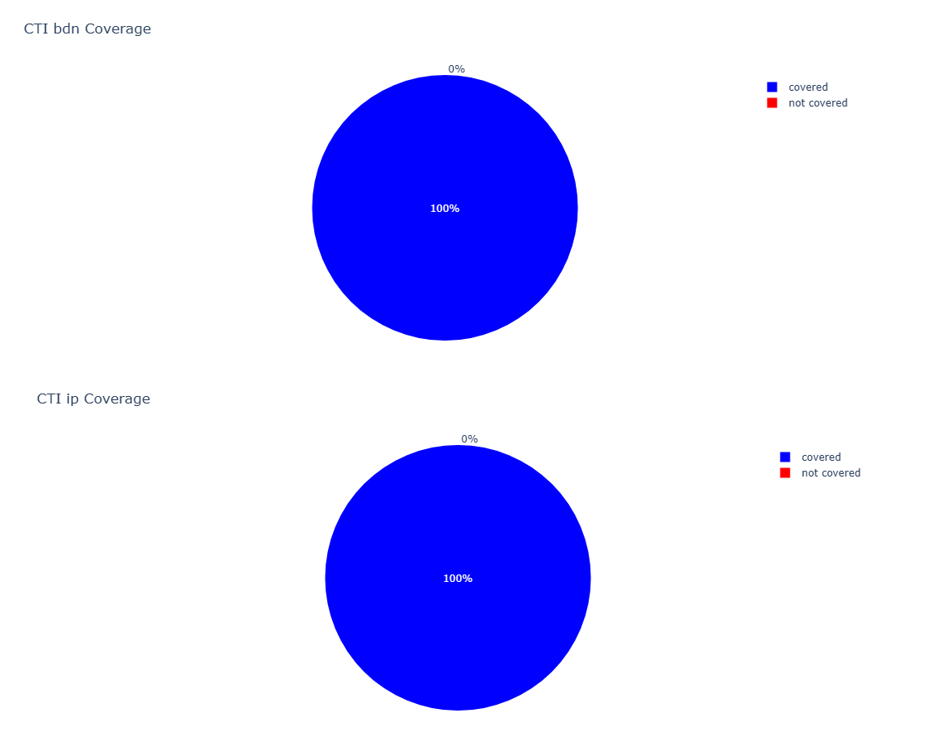
Centripetal’s Threat Intelligence Coverage
Centripetal’s aggregated threat intelligence covering this NPM-targeted campaign revealed 100% coverage during our internal analysis, with full inclusion of both IP addresses and domains associated with the attacks. While our threat intelligence primarily focuses on network indicators of compromise (IOCs), the value lies in its ability to disrupt the attack chain at the very earliest stages, before adversaries can advance further into the environment. (Figure 7)
The September 2025 Node Package Manager compromises underscore the evolving nature of software supply chain threats, with attackers shifting from targeted phishing and credential abuse to large scale, worm like propagation across open source ecosystems. Both the crypto focused campaign and the Shai Hulud worm demonstrate how phishing remains the critical gateway for initial access, enabling credential theft and subsequent package tampering. Once access is gained, malicious code can propagate rapidly through trusted dependencies, amplifying the impact on developers and end users alike. These incidents highlight the urgent need for early detection of phishing activity, rigorous package integrity controls, and continuous monitoring of both developer accounts and build pipelines to reduce the risk of downstream compromise.
Centripetal is also pleased to offer Penetration Testing and Vulnerability Assessment services to help organizations identify vulnerabilities and reduce risk. If interested, please contact our Professional Services team at profservs@centripetal.ai or reach out to your Centripetal Account Representative.
Resources
- Aikido - npm debug and chalk packages compromised
- PaloAltoNetworks - Breakdown: Widespread npm Supply Chain Attack Puts Billions of Weekly Downloads at Risk
- Sygnia - 16 Minutes to Impact: npm Supply Chain Abuse Deploys crypto-draining malware
- SOCRadar - Massive npm Supply Chain Attack Exposes Millions to Crypto-Stealing Malware
- ReversingLabs - Crypto wallets targeted in widespread hack of npm, GitHub
- BleepingComputer - Hackers hijack npm packages with 2 billion weekly downloads in supply chain attack
- ArticWolf - Wormable Malware Causing Supply Chain Compromise of npm Code Packages
- SecurityWeek - Shai-Hulud Supply Chain Attack: Worm Used to Steal Secrets, 180+ NPM Packages Hit
- Aikido - S1ngularity/nx attackers strike again
- ReversingLabs - Self-replicating Shai-hulud worm spreads token-stealing malware on npm
- Checkmarx - NPM Hit By Shai-Hulud, The Self-Replicating Supply Chain Attack
- SecurityAlliance - Following up on 'The Largest (Failed) Supply Chain Attack in History'
Know what’s coming. Stop what’s next.
Sign up for our free threat alert bulletin service here.
The Cybercrime Barrier Your Organization Deserves
Sign up for a custom demonstration from our security team of how we bring together the best minds and most complete collection of threat intelligence to provide you with a shocking level of relief.