Insights into the Persistence and Resilience of Bulletproof Hosting: A Case Study on Stark Industries Solutions
January 5, 2026
By Esmé Newell
A bulletproof host is a web hosting provider who, through a lassiez-faire approach to malicious activity, enables cybercriminals to continue operating. They do not directly carry out cyber-attacks; however, they provide the underlying infrastructure and look the other way, ignoring regulation and complaints. Researchers claim that the most effective way of defending against such providers is to identify those with the highest risk profile and block them, using threat intelligence and active behavioral tracking aligned to the specific environment. This research examines the world of bulletproof hosting and applies Stark Industries Solutions Ltd. as a real-world example to illustrate the threat posed by, and the resilience of, bulletproof hosting providers.
Bulletproof Hosting: An Overview
What is BPH?
Internet Service Providers (ISPs) act as a channel to reach the internet and share content with the world. Operating this service comes with influence and responsibility, and in the context of cybersecurity, ISPs play a major role in investigating and preventing malicious activity. Users can submit abuse complaints against content hosted by ISPs, resulting in investigation and mitigating actions. Some legislation holds ISPs accountable for what they host, such as the Digital Services Act in the EU. Bulletproof Hosting (BPH) refers to web hosting providers who disregard regulation, ignore abuse complaints and are publicly known to be lenient with the content they serve, making them an attractive place for threat actors to conduct malicious activity.
Ignoring abuse complaints gives threat actors the confidence that an attack can be carried out before action is taken — or that it may not be stopped at all. BPHs often carefully choose the kind of illegal activity they allow and will locate themselves in regions with less capacity to regulate and sanction this activity, building their reputation along the way. Complex technical configurations also create difficulties in reporting abuse, such as rapidly changing IPs associated with domains. A concerning trend observed recently by Silent Push sees threat actors using multiple BPH providers to ensure continuity of attack infrastructure and campaigns.
The most effective way of defending against BPH providers is to proactively use threat intelligence to monitor their activity and block those positively identified in real-time. The decision to block all traffic coming from a BPH is a subjective one, that relies on the specific business and operational context of a specific organization. This means one cannot simply block all known BPH providers, as some host legitimate services that may be business critical. However, research suggests some general guidelines and characteristics which assist in mapping BPHs and determining the risk associated with a web hosting service, outlined below.
How Do You Identify a Bulletproof Host?
The first step in tracking and mapping BPHs is being able to identify them. Previous research highlights key characteristics possessed by BPHs, and they include the following:
- Anonymised Payments: Often BPH providers will request methods of payment which hide the identities involved in the transaction and are difficult to trace, like cryptocurrency such as Bitcoin or Ethereum.
- Delayed Abuse Response Times: BPHs will typically ignore or elongate the abuse complaint process as they are aware of and allow malicious activity to be conducted using their infrastructure. Even if a response is eventually made to a complaint, the threat actor will have had time to carry out a full attack, making the investigation pointless.
- Domain Generating Algorithms: Domains belonging to a BPH will often have been generated algorithmically.
- BPH Language: BPHs will sometimes clearly state that they are a BPH — and in many cases that declaration should be taken at face value. Common language used includes phrases like ‘DMCA ignored hosting’, which relates to US legislation on copyright.
- Lack of Business Attributes: Some BPHs lack an official associated domain or a physical address, attributes that indicate legitimacy and cultivate trust of an organization.
- Low IP Density: Researchers at Silent Push have observed that the vast majority of known BPHs have ownership over a low IP address density.
- Existence of Peering Issues: Autonomous Systems (ASs) often peer with each other to allow for ease and efficiency of traffic flow across the internet, but having a reputation as a BPH leads to difficulties as many legitimate services do not want to be associated and therefore decline to peer. This topic has raised additional discussions on holding those that peer with known BPH providers more accountable, as they assist in keeping BPHs online, making them complicit in enabling malicious content.
For security teams to effectively defend against BPHs they need to analyze web hosting providers against known BPH characteristics, track BPH activity in real time through use of threat intelligence, and determine the level of risk they are willing to accept within their environment. To illustrate the persistent nature of BPHs and the risks they pose, the following case study is presented on Stark Industries Solutions Ltd. The web hosting provider’s characteristics, historical activity and its recent evasive changes to infrastructure embody what it is to be a BPH.
Case: Stark Industries Solutions Ltd.
Who are they?
Stark Industries Solutions Ltd. (AS44477), not to be confused with the Marvel universe tech giant, is a well-known BPH provider that has recently come under much scrutiny after facing sanctions from the European Union. Founded by brothers Iurie Neculiti and Ivan Neculiti, the web hosting provider offers virtual private servers (VPSs), proxies and virtual private networks (VPNs) from multiple locations. Stark Industries is incorporated in the UK, and its servers are connected through a data center in the Netherlands, using established infrastructure from other companies for operations, like MIRHosting. The organization is technically an intermediary in communications with PQ Hosting, the parent company, acting as a layer of obfuscation for malicious activities. It is evident from the services they offer, their low-price range ,and payment through cryptocurrency, that the BPH is enabling anonymity and malicious activity. Threat actors such as NoName057(16), FIN7 and GrayAlpha have all been observed utilising Stark Industries’ infrastructure for their campaigns.
Researchers from the Recorded Future Insikt Group classify Stark Industries as a Threat Activity Enabler (TAE). A TAE is an organization whose assets and services are continuously used by malicious actors; therefore, they are often not the direct instigator of a campaign but support it through infrastructure. Some TAEs operate with awareness of the part they play and actively enable it, while others support malicious actors unconsciously, unaware of how their infrastructure is being used. It is difficult to take punitive action against TAEs as they sit in a grey area between legitimacy and illegality and are adaptable to many situations. Stark Industries is a web hosting TAE which actively evades legislation, abuses Réseaux IP Européens (RIPE) resources, and assists threat actors in their campaigns. Stark Industries’ categorization as a conscious TAE is highlighted by its historical and current activity.
Historical Activity and Threat Enablement
Stark Industries emerged approximately two weeks prior to the Russian invasion of Ukraine in 2022, followed by the launch of targeted Distributed Denial of Service (DDoS) attacks against the UK and Europe, allies of the Ukrainian forces. Since this time, the BPH’s infrastructure has supported many Russian state-sponsored attacks along with disinformation campaigns. The technical configuration of this infrastructure makes it difficult to trace, attribute and prosecute, giving rise to European Union (EU) sanctions on Stark Industries itself.
Stark Industries has also been linked to the resurfacing of threat actor FIN7 in 2024. FIN7 has used Stark Industries domains to conduct attacks such as phishing and typosquatting, usually with a landing page that resembles one of a legitimate service like Microsoft and by taking advantage of older domains to bypass security controls conditioned on newly emerging domains. FIN7 hosts its command-and-control (C2) servers with the BPH provider, allowing for coordination and expansion of operations. This example of a threat actor using Stark Industries’ infrastructure demonstrates how the web hosting provider is an enabler for malicious activity, sustaining and protecting cyber-criminals online.
Sanctions, Evasion, and Recent Developments
As of May 20, 2025, EU sanctions have been placed on Stark Industries and key individuals involved in its operations. These come as a response to the company’s involvement in Russian cyber activity against the EU and its allies, including enabling disinformation campaigns and providing infrastructure to threat actors carrying out attacks. The sanctions mean Stark Industries is subjected to asset freezing and provision of funding is forbidden. Additionally, the Neculiti brothers are barred from entering EU territory, even for travel purposes.
The effectiveness of these sanctions, however, is being questioned by researchers as Stark Industries has been observed taking pre-emptive and evasive actions against them. Starting prior to the official announcement from the EU, Stark Industries made several infrastructural and branding changes in order to continue operations with largely no impact from sanctioning. Recorded Future has uncovered evidence that suggests the Neculiti brothers could have learned in advance that they were included in the next EU sanctions package, through a Moldovan news outlet who reported on leaked documents on May 8th and 9th, 2025. On May 13th, 2025, a new organization was created in RIPE, PQ Hosting Plus S.R.L., and three days later AS44477 (Stark Industries Solutions’ ASN) was transferred to this entity.
At the end of May, PQ Hosting rebranded to THE Hosting, transferring control over all assets and resources of Stark Industries’ parent company to the new legal entity. WorkTitans B.V. was named as the organization responsible for THE Hosting, however all references to it have been removed from THE Hosting’s website. AS209847, assigned to a local internet registry named WorkTitans B.V,. was registered in late June of 2025 with RIPE. WorkTitans B.V. is classified as a recruitment company, an area with little relevance to hosting providers, making its connection to Stark Industries increasingly suspicious. The Insikt Group at Recorded Future deem this association to be another attempt by the BPH to obfuscate true activity and control, further avoiding EU sanction impact.
There are signs to suggest the Neculiti brothers may have known of the sanctions earlier than the Moldovan news reports, or anticipated some punitive action from a legal perspective during the year. In April 2025, over a month prior to the sanctions package, Stark Industries began to migrate its infrastructure in Russia to UFO Hosting LLC. (AS33993). IP addresses and domains previously related to PQ Hosting and Stark Industries are now being attributed to AS33993. The transfer of Russian-based assets and resources to UFO Hosting is widely assessed to be a way for Stark industries to continue its services despite EU sanctions.
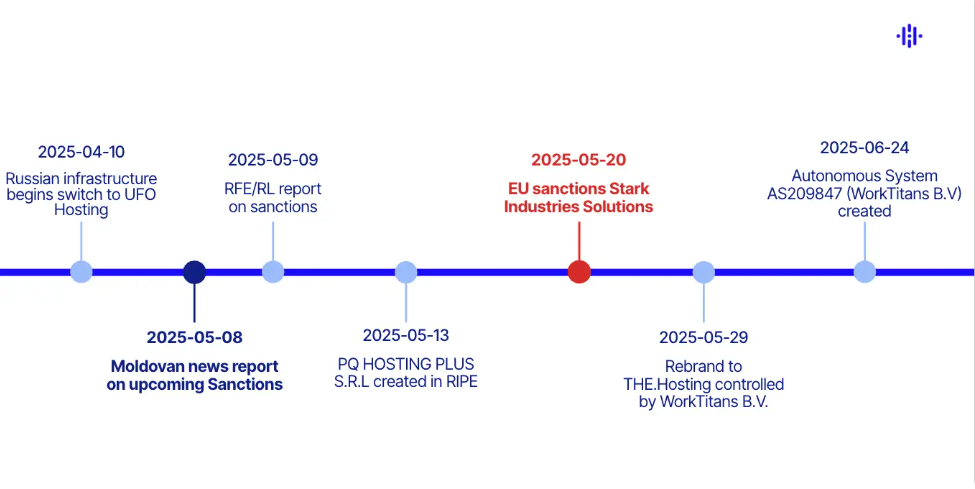
As observed above in Figure 1, from these infrastructural changes, it is clear Stark Industries continues to offer its services with little to no interruption. The now dissolved company has expanded its web of partners to include those above and, one can only assume, many more. For example, Krebs on Security mentions MIRHosting, which does not appear in sanctions but plays a role in keeping Stark Industries online. Research continues to investigate the network Stark Industries has established, with expectation of further discovery over time.
Centripetal Perspective: Addressing the Risk of Bulletproof Hosting
Centripetal is acutely aware of the threats posed by BPHs and recognize the structural weakness they represent in the global internet ecosystem. Through our intelligence services and research teams, we continually monitor and deepen our understanding of well-known BPH infrastructure, such as Stark Industries Solutions. Our objective is to ensure relevant, current, and actionable threat intelligence is applied to customer environments as part of our CleanINTERNET service — helping prevent attacks before they ever reach the network.
Pairing the largest collection of third-party threat intelligence with Centripetal Intelligence Services creates a comprehensive dataset — closing knowledge and visibility gaps that would otherwise remain unaddressed. To illustrate the value of this collaboration, we can examine the five most recently associated CIDRs with Stark Industries by BGP Tools: 104.253.158.0/24 154.205.255.0/24 104.253.165.0/24 45.38.42.0/24 23.230.101.0/24
In the case of Stark Industries, Centripetal Intelligence Services have derived and deployed intelligence feeds which capture known CIDRs attributed to the BPH through related ASNs, such as AS44477. These feeds are actively monitoring and shielding traffic, where applicable to a customer’s environment, taking down any potential attack chain at the source. The CIDRs listed above are contained within such feeds, demonstrating Centripetal’s ability to monitor BPH behavior and infrastructure to provide our customers with timely, operationally-ready intelligence.
Analysis of third-party threat intelligence feeds from our providers reveals only 2% coverage of the CIDRs identified by BGP Tools. This illustrates the value of pairing ingested data from external sources with Centripetal’s internal intelligence, creating the highest level of IOC coverage possible for our customers.
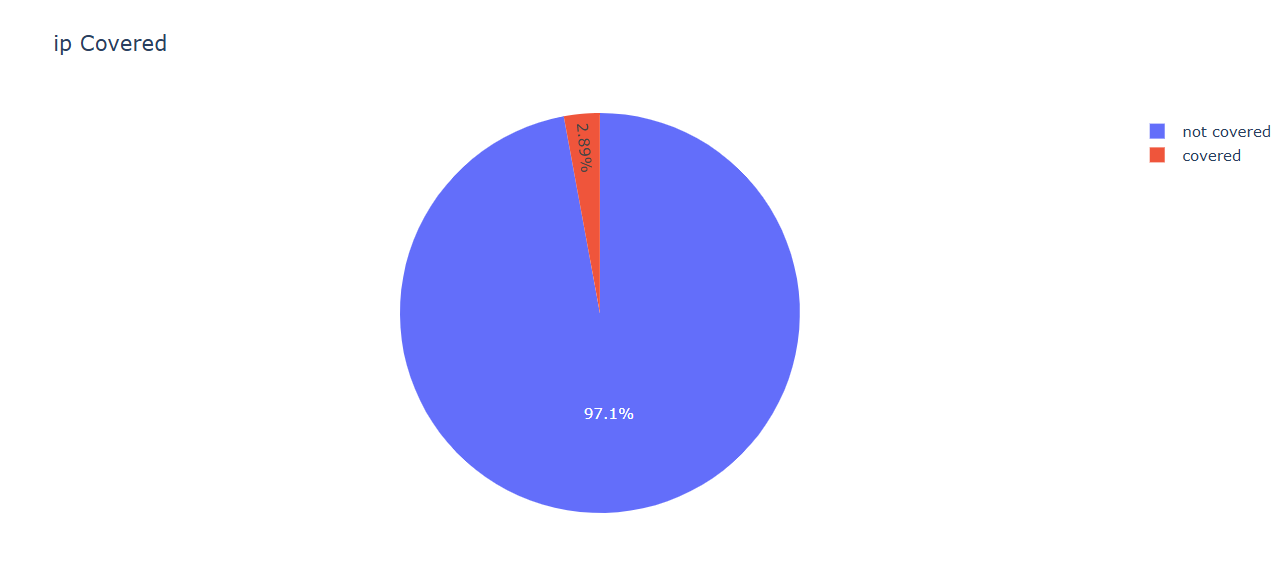
The above pie chart highlights that if third-party intelligence feeds alone were applied to customer environments, there would be 2.89% coverage of the defined Stark Industries CIDRs, meaning only 2.89% could be shielded on. However, Centripetal’s intelligence feeds have 100% coverage of the CIDRs, giving our customers 100% shielding potential.
What This Means for Defenders
Evidenced through the example of Stark Industries Solutions, BPHs pose a threat to organizations as a TAE. Connections to associated IPs/domains come with an additional risk of malicious activity. BPH characteristics and their ability to migrate quickly make them difficult to track, highlighting the need for application of real-time threat intelligence. Centripetal’s CleanINTERNET service provides this from both our internal and external intelligence sources, giving security teams the ability to analyse the risk of a given BPH to their organization, and take action on those deemed outside of the levels of risk willingly accepted. There is no doubt BPHs will continue to enable threat actors of all motives; the responsibility now lies with security and research teams to understand their exposure, determine their impact, and proactively reduce it.
Centripetal is also pleased to offer Penetration Testing and Vulnerability Assessment services to help organizations identify vulnerabilities and reduce risk. If interested, please contact our Professional Services team at profservs@centripetal.ai or reach out to your Centripetal Account Representative.
Resources
- https://www.sentinelone.com/cybersecurity-101/threat-intelligence/bulletproof-hosting/
- https://intel471.com/blog/bulletproof-hosting-a-critical-cybercriminal-service
- https://krebsonsecurity.com/2025/02/notorious-malware-spam-host-prospero-moves-to-kaspersky-lab/
- https://www.silentpush.com/webinar/webinar-bulletproof-hosting/
- https://krebsonsecurity.com/2024/05/stark-industries-solutions-an-iron-hammer-in-the-cloud/
- https://www.bleepingcomputer.com/news/security/european-union-sanctions-stark-industries-for-enabling-cyberattacks/
- https://dailysecurityreview.com/security-spotlight/eu-sanctions-stark-industries-and-leadership-for-supporting-russian-cyber-operations/
- https://www.silentpush.com/blog/fin7/#h-rented-fin7-infrastructure-stark-industries
- https://arachnedigital.medium.com/stark-industries-fuelling-russias-cyber-offensive-a16b3fac8123
- https://krebsonsecurity.com/2024/07/the-stark-truth-behind-the-resurgence-of-russias-fin7/
- https://www.recordedfuture.com/research/one-step-ahead-stark-industries-solutions-preempts-eu-sanctions
- Bulletproof Host Stark Industries Evades EU Sanctions – Krebs on Security
- Search - bgp.tools
Know what’s coming. Stop what’s next.
Sign up for our free threat alert bulletin service here.
The Cybercrime Barrier Your Organization Deserves
Sign up for a custom demonstration from our security team of how we bring together the best minds and most complete collection of threat intelligence to provide you with a shocking level of relief.