By Anna Balabushko
Revolver Rabbit is one of the most prolific actors leveraging Registered Domain Generation Algorithms (RDGAs), a rising domain abuse tactic that evades traditional DGA detection by pre-registering algorithmically generated domains. Since 2022, the actor has registered over 500,000 domains on the .bond Top-Level-Domain (TLD), spending more than $1 million in domain registration fees, which reflects both scale and significant financial investment (Infoblox, 2024).
Their domains typically follow repeatable patterns, such as dictionary words plus numeric suffixes (e.g., private-jets-99557[.]bond) or geographic/time-based elements (e.g., ai-courses-2024-pk[.]bond). Additional variants use short alphanumeric suffixes or double dashes, complicating rule-based detection (Infoblox Blog, 2024). These syntactic variations often evade traditional string-matching techniques, requiring DNS-layer telemetry and clustering for full visibility (Infoblox Research Report, 2024).
From October 2023 to April 2024, over 2 million unique RDGA domains were detected, with Revolver Rabbit among the few groups linked to XLoader malware samples, where its domains served as both decoy infrastructure and active C2 endpoints. While later identified as an advertising network, its domains may have been repurposed by threat actors post-campaign, complicating attribution (BleepingComputer, 2024).
Our Intelligence Insight
In the past month, the CleanINTERNET® service identified outbound web traffic involving domains consistent with RDGA tradecraft attributed to Revolver Rabbit, specifically, logged to multiple .bond domains, each exhibiting syntax and structural patterns characteristic of the actor’s naming convention, such as dictionary word combinations with numeric or country-code suffixes (Figure 1.)
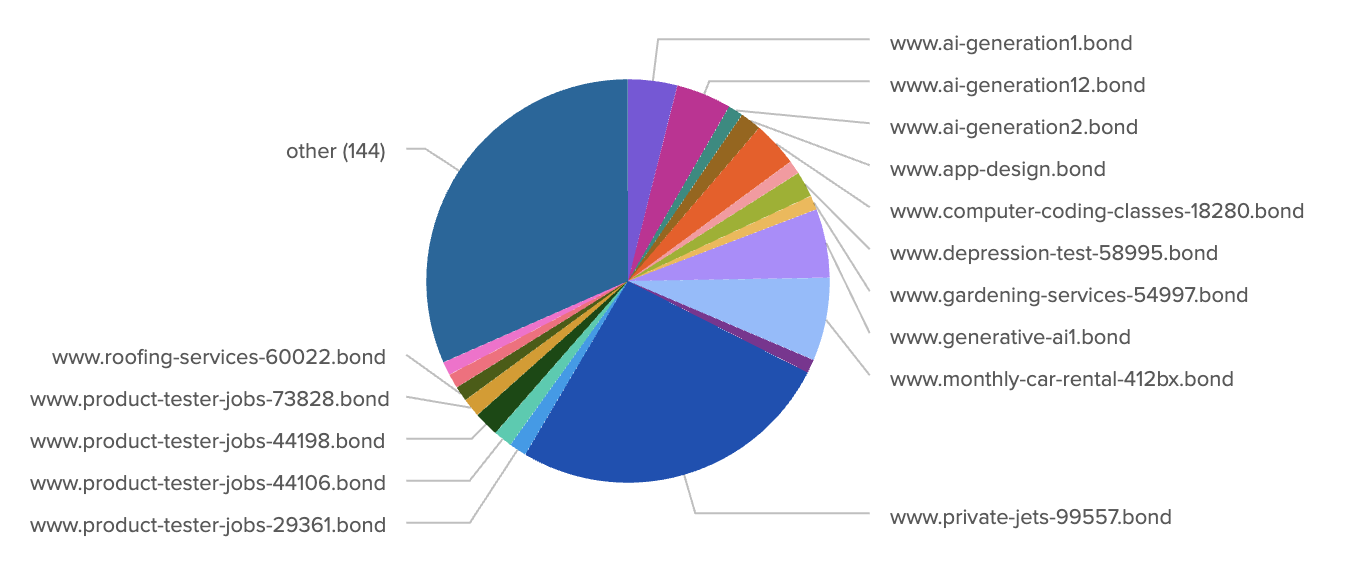
Figure 1. Examples of RDGA domains associated with Revolver Rabbit observed by CleanINTERNET
These domains have been linked to suspicious infrastructure in malware campaigns, functioning as C2 nodes or decoys while presenting as benign parked pages, a tactic used to avoid detection (Infoblox, 2024). Sandbox analysis from UrlQuery of a .bond domain being sinkholed by Quad9 DNS confirms that such domains often host link farms, with malicious functionality activated only under specific conditions (Figure 2).

Figure 2. UrlQuery sandbox analysis of a domain seen by CleanINTERNET®
This reflects the core strategy behind Revolver Rabbit’s RDGA operations is mass domain registration with minimal individual signals, enabling them to slip past traditional blocklists. The observed clustering highlights the critical need for DNS-layer visibility and behavioral analytics, since superficial analysis often misses the infrastructure’s malicious function.
DGAs vs RDGAs?
Registered Domain Generation Algorithms (RDGAs) represent a tactical shift from traditional Domain Generation Algorithms (DGAs) used in malware campaigns. While both produce large numbers of domain names algorithmically, their mechanisms and applications differ significantly:
- Traditional DGAs– pseudo-random generators used by malware to create domain names, that may use random strings or dictionary words, with dictionaries either hardcoded or sourced externally. Most generated domains remain unregistered, aiding evasion but enabling detection through pattern analysis.
- Registered DGAs, by contrast, keep the algorithm secret and pre-register all generated domains in advance. These domains are operational immediately and often resemble legitimate services, making them harder to detect through traditional static analysis.
Unlike DGAs, which are primarily used for malware C2, RDGAs support a broader range of activities, including phishing, spam, fraud, and scam distribution. They are also used by both malicious actors and legitimate businesses, with tools like Namecheap’s “Beast Mode” enabling large-scale domain registration by anyone (Infoblox, 2024).
This distinction is critical for defenders: RDGA infrastructure cannot be dismantled through DGA-based blocking alone and requires advanced DNS telemetry and behavioral analytics to detect.
The following table summarizes key differences between traditional DGAs and RDGAs:
| Aspect | Traditional DGA | RDGA |
|---|---|---|
| Generation Location | Within the malware | External, controlled by the attacker |
| Domain Registration | Few domains registered by attacker | All generated domains registered by attacker |
| NXDOMAIN Responses | High (many unregistered domains) | Low (all domains registered) |
| Detection Difficulty | Easier due to NXDOMAIN patterns | Harder due to fully registered domains |
| Use Cases | Primarily for malware C2 communication | Malware, phishing, spam, scams, TDSs, VPNs, etc. |
Campaign Purpose
Revolver Rabbit is threat actor that operates at scale, leveraging domain infrastructure for what appears to be a dual-use model, serving both legitimate advertising and, potentially, malicious operations. Although initially suspected of direct threat activity due to RDGA domain overlap with malware campaigns, subsequent research identified the group as an advertising affiliate network. However, telemetry shows that their infrastructure has been repeatedly co-opted by malware operators post-campaign (Infoblox, 2024).
Infoblox’s analysis of over 40 XLoader samples from 2023–2024 revealed domains registered under Revolver Rabbit’s naming conventions (e.g., [keyword]-[year]-[country].bond) being used as command-and-control (C2) nodes. In many cases, these domains appeared in DNS telemetry as outbound beacons or redirectors. Initially serving as benign advertising “parked” pages during active campaigns, many were later observed delivering payloads or facilitating malicious callbacks once abandoned.
Infoblox notes that domains are often dropped or rotated out of use within weeks of an ad campaign’s conclusion, creating a window of opportunity for threat actors to register expired RDGA domains or hijack infrastructure that remains dormant but routable. This temporal ambiguity makes attribution difficult: while domains may have been benign at the time of registration, they are demonstrably reused for malware operations shortly after.
The Revolver Rabbit case demonstrates the operational gray zone between advertising networks and cybercrime infrastructure. It also reinforces the value of timing, telemetry, and DNS-layer behavioral analysis in distinguishing between RDGA domains actively supporting malicious activity versus those that are passively abused or impersonated.
Delivery & Attack Chain
Rather than following a fixed linear kill chain, Revolver Rabbit’s infrastructure supports a modular attack flow:
- Initial Access is achieved through phishing lures, trojanized downloads, or malvertising chains. These vectors frequently embed or redirect to Revolver Rabbit–registered domains that appear benign or thematically relevant (e.g.,
online-jobs-42681[.]bond,ai-courses-2024-pk[.]bond), increasing the likelihood of bypassing URL filtering. - Payload Delivery or Callback occurs via these RDGA domains, which may serve multiple roles:
- Malware distribution nodes, as seen in XLoader samples (info-stealing malware, the successor of Formbook) referencing
.bondRDGA domains. - Command-and-Control (C2) endpoints, which may resolve to attacker infrastructure only under specific conditions or remain dormant until activated.
- Decoy infrastructure, used to mislead sandbox analysis by presenting parked domains or generic landing pages.
- Malware distribution nodes, as seen in XLoader samples (info-stealing malware, the successor of Formbook) referencing
The domains commonly follow recognizable linguistic patterns: concatenated dictionary words with numeric suffixes (e.g., security-surveillance-cameras-42345[.]bond), country codes (ai-courses-2024-in[.]bond), or even syntactic anomalies such as double dashes (welding-machines--56717[.]bond). These variants often resemble legitimate services, leveraging trust in seemingly innocuous topics like education, health, or travel.
This polymorphic naming strategy enhances evasiveness by blending into the open web, frustrating static detection logic and enabling flexible domain rotation. DNS telemetry indicates that many of these domains initially behave like legitimate parked sites or advertising redirects, only later weaponized or repurposed post-campaign. Infoblox researchers note that many were “no longer actively used in the advertising network at the time of analysis,” though they appeared in malware samples functioning as C2 nodes or redirectors (Infoblox, 2024).
Operation Model
Revolver Rabbit’s infrastructure reveals an industrialized domain registration pipeline, where vast swaths of internet real estate are claimed algorithmically in advance. This registered-DGA (RDGA) strategy enables long-term planning of campaigns while avoiding the predictability of real-time domain generation algorithms, often flagged by endpoint or DNS security tools.
The actor’s use of patterned domain sets (e.g., dictionary-word + number, country-code + year, or semantic phrases) suggests a blend of automation and linguistic engineering, possibly to preserve plausibility or to mimic legitimate domain portfolios. According to Infoblox, many domains followed “obvious human-readable formats that wouldn’t be caught by simple string matching,” demanding context-aware clustering and DNS enrichment to map the full infrastructure (Infoblox Blog, 2024).
The operation is supported by:
- Heavy upfront investment, with hundreds of thousands of .bond domains acquired (costing more than $1 million in registration fees) before any public abuse is observed.
- Ephemeral domain usage, where domains may be used briefly for a campaign and then dropped, or may serve dual purposes (advertising and malicious callbacks).
- Ambiguity by design, blurring the line between legitimate and malicious use cases. Even after publication, Revolver Rabbit’s relationship to malware campaigns remains unclear due to the fluid reuse of domains by third parties (BleepingComputer, 2024).
This model reflects a paradigm shift in attacker infrastructure strategy, where threat actors no longer rely solely on domain generation malware but instead build large, persistent, and repurposable registries. The result is a cost-effective, resilient platform that serves the needs of both financially motivated cybercriminals and legitimate-looking front operations, posing a sustained challenge to defenders relying on static threat intelligence or URL reputation alone.
Centripetal’s Perspective
CleanINTERNET® has maintained persistent monitoring for RDGA-based infrastructure, with continuous detections and protections in place across all customer environments. In this analysis, we focused specifically on the 42 domain-based Indicators of Compromise (IOCs) published in Infoblox’s July 17, 2024 research on the RGDA threat actors including “Revolver Rabbit”. This curated set of IOCs formed the foundation of a targeted retrospective analysis spanning July 17, 2024 through May 13, 2025, aiming to assess coverage, behavior, and attribution fidelity across our internal telemetry.
While CleanINTERNET® sources threat intelligence from a wide range of partners and feeds, this analysis is limited to the domains explicitly identified by Infoblox. It does not represent the full extent of RDGA visibility within our ecosystem. In fact, throughout the extended reporting window from October 1, 2023, to May 17, 2025, CleanINTERNET® ingested over 2.17 million unique domain-based indicators tied to RDGA “Revolver Rabbit” infrastructure by pattern matching. Many of these extend well beyond the scope of the Infoblox report. Figure 3 visualizes this expansion, plotting a cumulative chart of RDGA-related domains over time. The trajectory is distinctly sigmoidal: initial activity was sparse, as infrastructure was seeded through late 2023 and early 2024, followed by a steep acceleration in Q2 and Q3 of 2024 as the adversary industrialized its registration cadence. Growth gradually tapers in Q1 2025, leveling off above 2.17 million unique domains by mid-May. The result underscores both the industrial scale of the operation and the visibility achievable through combined internal and partner telemetry. On the other hand, the current analysis focuses on how well the specific indicators surfaced by Infoblox align with our visibility and partner telemetry. Centripetal plans to perform additional analysis which focuses on this larger set of identified campaign related domains which fall outside the scope of this initial report.
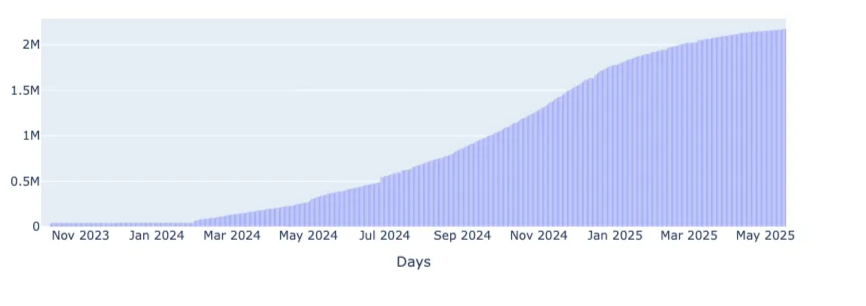
Figure 3.Cumulative Domain-Based IOCs Attributed to Revolver Rabbit RDGA Infrastructure Observed by CleanINTERNET® (Oct 2023 – May 2025)
Initial results show that 88% of the Infoblox-attributed IOCs were observed within our threat intelligence environment (Figure 4). The small delta is consistent with Infoblox’s own stance that not all domains were active during the period of study. Dormant, parked, or unreleased domains likely account for the remaining 12%, which were not surfaced by our internal or partner feeds.
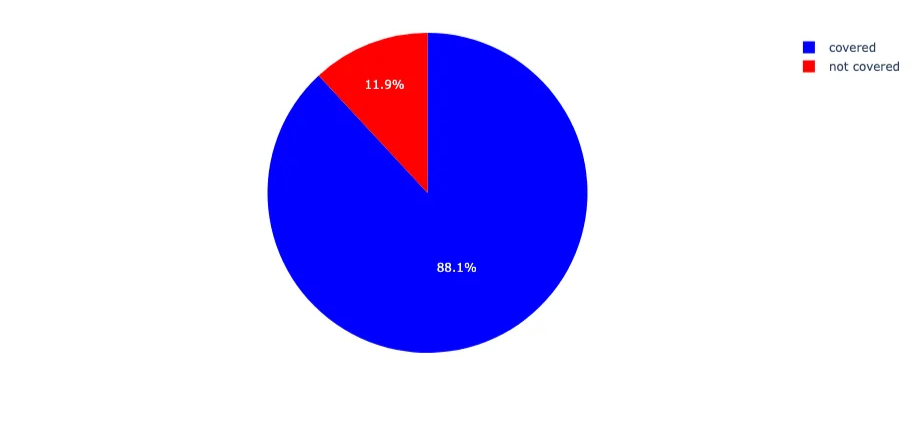
Figure 4. Overall BDN coverage
A temporal breakdown (Figure 5) highlights minimal visibility prior to October 2024, with fewer than 10 IOCs detected. Activity accelerated in Q4 2024, with monthly domain sightings exceeding 40. This trend supports Infoblox’s note that RDGA-generated domains may be activated in waves or reused in later stages of an operation, depending on campaign evolution.
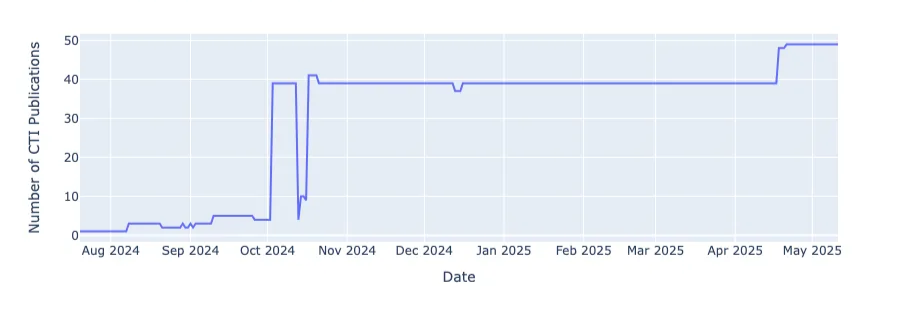
Figure 5. Monthly Entry of Infoblox-Attributed IOCs into CleanINTERNET® Threat Intelligence
Behavioral classification (Figure 6) reveals that the majority of matched IOCs were flagged as command-and-control (C2) infrastructure, consistent with Infoblox’s assessment of Revolver Rabbit domains being used for beaconing and payload staging. Other domains were remained behaviorally uncategorized due to inactivity or evasion tactics.
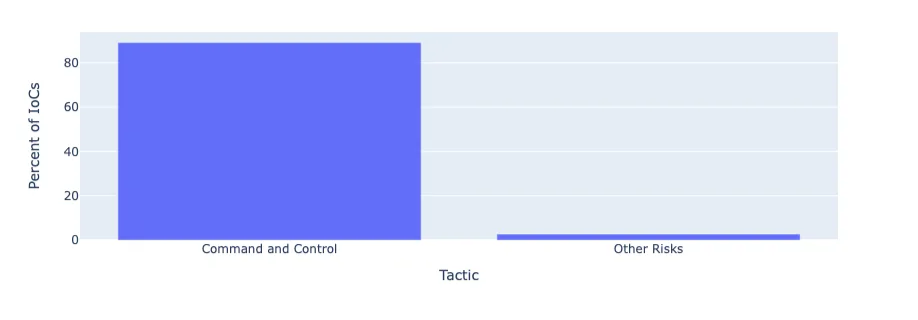
Figure 6. Percentage of BDN IoCs Associated with a Tactic
Ultimately, this retrospective validates that CleanINTERNET® retains substantial coverage of known RDGA threats, including those highlighted in public threat research. However, it also underscores the importance of broader visibility: the Infoblox list represents a focused snapshot, while CleanINTERNET®’s telemetry reflects the industrial scale of RDGA usage across the global threat landscape.
The Revolver Rabbit campaign exemplifies the growing sophistication and scale of RDGA-based threat infrastructure. By pre-registering algorithmically generated domains, often in human-readable formats, the actor blurs the line between benign advertising networks and malicious operations. While initial attributions linked these domains to potentially legitimate services, subsequent telemetry, malware correlations, and domain reactivation patterns suggest their repeated repurposing by cybercriminals.
CleanINTERNET®’s targeted analysis of Infoblox’s July 17, 2024 RDGA IOCs confirms high visibility across our internal and partner telemetry, with 88% of observed domains aligning with malicious or suspicious behavior, predominantly command-and-control activity. However, this snapshot represents only a fraction of the broader RDGA ecosystem observed in the wild, which includes millions of domains created and leveraged by Revolver Rabbit and other threat actors for malicious activity.
This campaign highlights the critical need for defenders to evolve beyond static detection and embrace DNS-layer telemetry, behavioral analytics, and clustering techniques to track RDGA infrastructure. As threat actors continue to industrialize domain registration and weaponize dormant infrastructure, comprehensive visibility and adaptive threat modeling will be key to sustained protection.
Centripetal is also pleased to offer Penetration Testing and Vulnerability Assessment services to help organizations identify vulnerabilities and reduce risk. If interested, please contact our Professional Services team at profservs@centripetal.ai or reach out to your Centripetal Account Representative.
Resources
- Infoblox – RDGAs: The Next Chapter in Domain Generation Algorithms
- MySecurityMarketplace – Registered DGAs : The Prolific New Menace No One Is Talking About
- Infoblox – Revolver Rabbit’s Million-Dollar Masquerade: Infoblox Uncovers The Hidden World of RDGAs
- Infoblox Threat Intel – Revolver Rabbit
- BleepingComputer – Revolver Rabbit gang registers 500,000 domains for malware campaigns
- TechRadar – Criminals are spending millions on malicious domains — and it’s paying off for them in a big way
- Infoblox Research Report – Registered DGAs : The Prolific New Menace No One Is Talking About
