Proof-of-Concept Exploit Observed for Critical Zero-Day
June 17, 2025
By Anna Balabushko
CVE-2025-32756 is a critical remote code execution (RCE) vulnerability affecting multiple Fortinet products, including FortiVoice, FortiMail, FortiNDR, FortiRecorder, and FortiCamera. The flaw arises from a stack-based buffer overflow in the handling of the AuthHash cookie’s enc parameter within the /remote/hostcheck_validate HTTP endpoint. Due to insufficient input validation, unauthenticated attackers can send specially crafted requests that overwrite memory on the stack, leading to arbitrary code execution with system-level privileges. The vulnerability is remotely exploitable over the network and requires no user interaction or authentication, making it highly accessible to attackers. Public proof-of-concept (PoC) exploit code has been released, and Fortinet has confirmed in-the-wild exploitation against FortiVoice appliances. Affected systems are exposed to full compromise, with observed attack patterns including network scanning, credential harvesting via enabled fcgi debugging, and systematic erasure of system crash logs to evade detection. The issue impacts product versions released before May 2025 and has been assigned a CVSS score of 9.8 (Critical) due to its ease of exploitation and the severity of its impact on confidentiality, integrity, and availability. (Cyber Security News, Fortinet, 2025)
Vulnerability Type (CWE)
CWE-787: Out-of-Bounds Write (NIST)
Occurs when a program writes data past the end or before the beginning of a buffer. This can corrupt data, crash the application, or allow attackers to execute arbitrary code by overwriting critical memory regions such as return addresses or function pointers.
CWE-121: Stack-Based Buffer Overflow (Fortinet)
Occurs when a program writes more data to a buffer located on the stack than the buffer can hold, which can overwrite adjacent memory, including the return address of a function.
CVSS Score
Base Score: 9.8 (Critical)
Attack Vector: Network (AV:N)
Attack Complexity: Low (AC:L)
Privileges Required: None (PR:N)
User Interaction: None (UI:N)
Scope: Unchanged (S:U)
Impact on CIA: High
- Confidentiality: High (SC:H)
- Integrity: High (SI:H)
- Availability: High (SA:H)
Impacted Versions
| Product version | Vulnerable | Mitigation |
|---|---|---|
| FortiCamera 2.1 | 2.1.0 through 2.1.3 | Upgrade to 2.1.4 or above |
| FortiCamera 2.0 | 2.0 all versions | Migrate to a fixed release |
| FortiCamera 1.1 | 1.1 all versions | Migrate to a fixed release |
| FortiMail 7.6 | 7.6.0 through 7.6.2 | Upgrade to 7.6.3 or above |
| FortiMail 7.4 | 7.4.0 through 7.4.4 | Upgrade to 7.4.5 or above |
| FortiMail 7.2 | 7.2.0 through 7.2.7 | Upgrade to 7.2.8 or above |
| FortiMail 7.0 | 7.0.0 through 7.0.8 | Upgrade to 7.0.9 or above |
| FortiNDR 7.6 | 7.6.0 | Upgrade to 7.6.1 or above |
| FortiNDR 7.4 | 7.4.0 through 7.4.7 | Upgrade to 7.4.8 or above |
| FortiNDR 7.2 | 7.2.0 through 7.2.4 | Upgrade to 7.2.5 or above |
| FortiNDR 7.1 | 7.1 all versions | Migrate to a fixed release |
| FortiNDR 7.0 | 7.0.0 through 7.0.6 | Upgrade to 7.0.7 or above |
| FortiNDR 1.5 | 1.5 all versions | Migrate to a fixed release |
| FortiNDR 1.4 | 1.4 all versions | Migrate to a fixed release |
| FortiNDR 1.3 | 1.3 all versions | Migrate to a fixed release |
| FortiNDR 1.2 | 1.2 all versions | Migrate to a fixed release |
| FortiNDR 1.1 | 1.1 all versions | Migrate to a fixed release |
| FortiRecorder 7.2 | 7.2.0 through 7.2.3 | Upgrade to 7.2.4 or above |
| FortiRecorder 7.0 | 7.0.0 through 7.0.5 | Upgrade to 7.0.6 or above |
| FortiRecorder 6.4 | 6.4.0 through 6.4.5 | Upgrade to 6.4.6 or above |
| FortiVoice 7.2 | 7.2.0 | Upgrade to 7.2.1 or above |
| FortiVoice 7.0 | 7.0.0 through 7.0.6 | Upgrade to 7.0.7 or above |
| FortiVoice 6.4 | 6.4.0 through 6.4.10 | Upgrade to 6.4.11 or above |
Mitigation Steps
- Update to the latest patched versions immediately.
- Disable HTTP/HTTPS administrative interfaces on exposed devices.
- Disable SSL VPN if it is not actively used.
- Monitor logs for signs of suspicious command execution through the SSL VPN process.
- Apply zero trust access policies to restrict external access.
- Enable MFA ****across all administrative access.
- Deploy IPS/IDS rules to monitor abnormal POST
/remote/hostcheck_validatetraffic.
Exploit Process
The exploitation process follows the following steps according to Fortinet’s PSIRT advisory (FG-IR-25-254).
Phase 1: Target Discovery and Reconnaissance
- Threat Actor (TA) scans network segments to identify vulnerable Fortinet devices (FortiVoice, FortiMail, FortiNDR, FortiRecorder, FortiCamera).
- Tools like nmap, masscan, or a custom Python scanner may be used to detect open ports and identify systems exposing the
/remote/hostcheck_validateendpoint.
Phase 2: Exploitation via Buffer Overflow
- TA uses a publicly available or custom script (e.g., fortinet_cve_2025_32756_poc.py) to initiate the exploit:
python3 fortinet_cve_2025_32756_poc.py <target_ip> [-p <port>] [-d] - The script sends a malformed HTTP POST request to:
http://<target_ip>/remote/hostcheck_validate- Within this request, the
AuthHashcookie contains a maliciousencparameter, which is carefully crafted to trigger a stack-based buffer overflow, allowing arbitrary code execution.
- Within this request, the
Phase 3: Initial Payload Execution
- On successful exploitation, the attacker achieves unauthenticated Remote Code Execution (RCE) on the device.
- Initial payload usually involves:
- Dropping malware files (e.g.,
/bin/wpad_ac_helper) - Gaining a reverse shell or persistent access mechanism
- Modifying system logs or disabling logging
- Dropping malware files (e.g.,
Phase 4: Establish Persistence and Credential Harvesting
- TA enable fcgi debugging to extract sensitive data:
diag debug application fcgi- The setting
general to-file ENABLEDis activated. - This is non-default and serves as an Indicator of Compromise (IoC).
- The setting
- Modify crontab entries to capture credentials:
- File:
/data/etc/crontabor/var/spool/cron/crontabs/root - Example cron job added:
0 */12 * * * root busybox grep -rn passw /var/spool/crashlog/fcgi.debug > /var/spool/.sync; cat /dev/null > /var/spool/crashlog/fcgi.debug - This greps password strings from debug logs and saves to /
var/spool/.sync.
- File:
- Deploy additional files for persistence and lateral movement:
/lib/libfmlogin.so: Malicious SSH credential sniffer/tmp/.sshdpm: Captures stolen credentials/bin/busybox,/bin/fmtest: Utility and scanning tools/etc/httpd.conf: Modified to include SOCKS proxy module:LoadModule socks5_module modules/mod_socks5.so
Phase 5: Lateral Movement and Network Reconnaissance
- TA use ****
/bin/fmtest****(MD5: 2c8834a52faee8d87cff7cd09c4fb946) to scan internal networks for additional exploitable devices. - Setup SOCKS5 tunneling via the modified
httpd.confto facilitate pivoting through the compromised device.
Phase 6: Anti-Forensics and Log Erasure
- Attackers periodically erase or rotate log files to hide tracks:
- Crash log contents redirected to
.syncFileslikefcgi.debugare wiped with:cat /dev/null > /var/spool/crashlog/fcgi.debug
- Crash log contents redirected to
- Injected logs such as:
mod_fcgid: error reading data, FastCGI server closed connectionmod_fcgid:process exit(communication error), get unexpected signal 11- May serve as a technical IoC showing fcgid instability after tampering
Phase 7: Command and Control (C2) and Data Exfiltration
- TA uses established reverse shells or SOCKS proxies for C2 communication.
- Credentials stored in the following file get exfiltrated regularly:
/var/spool/.sync/tmp/.sshdpmare ****
Timeline
2025-05-07 - Initial Fortinet telemetry identifies anomalous exploitation attempts.
2025-05-13 - Official Fortinet PSIRT advisory (FG-IR-25-254) released.
2025-05-14 - Added reference to the CISA KEV listing.
IOCs
The following IOCs were stated in Fortinet’s PSIRT advisory (FG-IR-25-254).
IP Addresses:
- 198.105.127[.]124
- 43.228.217[.]173
- 43.228.217[.]82
- 156.236.76[.]90
- 218.187.69[.]244
- 218.187.69[.]59
Files & Hashes
| File | Description | MD5 |
|---|---|---|
/bin/wpad_ac_helper | Main malware component | 4410352e110f82eabc0bf160bec41d21 |
/lib/libfmlogin.so | SSH login sniffer | 364929c45703a84347064e2d5de45bcd |
/bin/fmtest | Network scanner | 2c8834a52faee8d87cff7cd09c4fb946 |
/bin/busybox | Multi-purpose binary (2 variants) | ebce43017d2cb316ea45e08374de7315 / 489821c38f429a21e1ea821f8460e590 |
Network Behaviors:
- Unexpected requests to
/remote/hostcheck_validate - Enabling of fcgi debugging (used to capture login attempts)
- Removal of system crash logs post-exploitation
Persistence Indicators:
- Rewritten binaries with embedded credential harvesters
- Malicious cron jobs running under root
- SSH credential siphoning via modified shared libraries
CVE-2025-32756 is a critical remote code execution vulnerability in multiple Fortinet products that has been actively exploited in the wild. With a CVSS score of 9.8 and evidence of sophisticated post-exploitation activity, including credential harvesting, system modification, and persistence mechanisms, this vulnerability poses a severe risk to enterprise environments. Organizations are strongly urged to apply vendor patches immediately, audit systems for known indicators of compromise (IOCs), and proactively shield against identified malicious IPs. Comprehensive monitoring, log review, and hardening of exposed services are essential to detect and prevent further exploitation (Cyber Security News, 2025).
Centripetal’s Perspective
Centripetal’s CleanINTERNET® service provides a proactive, intelligence-driven defense against vulnerabilities like CVE-2025-32756, which has been exploited in the wild to gain unauthenticated remote code execution on Fortinet appliances through a stack-based buffer overflow in the /remote/hostcheck_validate endpoint. At the time of the POC’s release, Centripetal had 100% coverage against the network indicators disclosed.
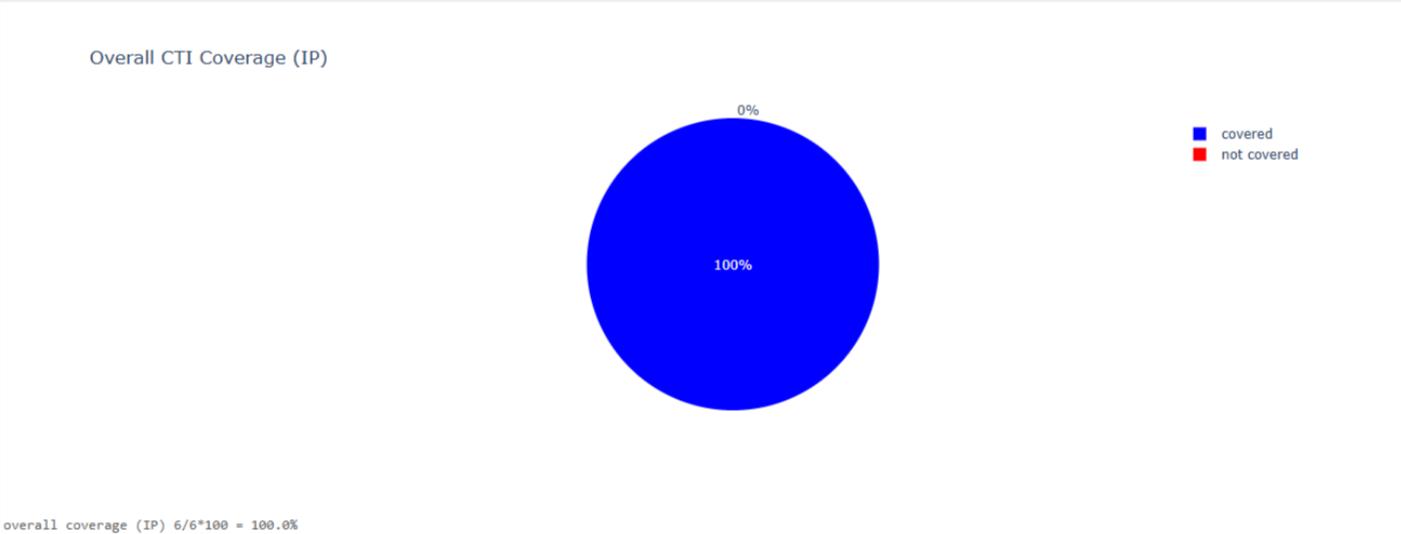
Leveraging billions of threat indicators, CleanINTERNET dynamically blocks malicious traffic using real-time global threat feeds and augmented human analysis, proactively protecting organizations from exploitation attempts involving known IoCs. This approach ensures reduced attack surface, enhanced security operations, and uninterrupted business continuity, enabling organizations to adopt a proactive and adaptive cybersecurity strategy against evolving threats.
If you are a current client of Fortinet please contact support@centripetal.ai.
Centripetal is also pleased to offer Penetration Testing and Vulnerability Assessment services to help organizations identify vulnerabilities and reduce risk. If interested, please contact our Professional Services team at profservs@centripetal.ai or reach out to your Centripetal Account Representative.
Resources
- Fortinet - Stack-based buffer overflow vulnerability in API
- Cyber Security News - PoC Exploit Released for Fortinet 0-Day Vulnerability that Allows Remote Code Execution
- NIST - CVE-2025-32756
Know what’s coming. Stop what’s next.
Sign up for our free threat alert bulletin service here.
The Cybercrime Barrier Your Organization Deserves
Sign up for a custom demonstration from our security team of how we bring together the best minds and most complete collection of threat intelligence to provide you with a shocking level of relief.