Threat actors are actively abusing a flaw in Discord’s invite link system to deliver malware through hijacked or spoofed server invites. The campaign, uncovered in mid-2025 by multiple cybersecurity research teams, leverages expired or recycled Discord invite links and redirects users through silent redirection chains that lead to multi-stage malware payloads. These payloads include AsyncRAT, Skuld Stealer, and ChromeKatz malware families designed to exfiltrate sensitive data such as credentials, browser cookies, and Discord session tokens. The campaign leverages user trust in Discord branding, making it highly effective for social engineering.
Attack Flow
An in-depth analysis by security firm Check Point (CheckPoint, 2025) details how threat actors exploit unused or expired Discord invite links to lure victims into malicious servers that ultimately deliver malware payloads (Figure 1). The report goes beyond surface-level technical observations, providing insight into more advanced techniques uncovered by researchers, including obfuscation and encryption methods used to conceal a multi-stage infection chain, as illustrated in Figure 2.
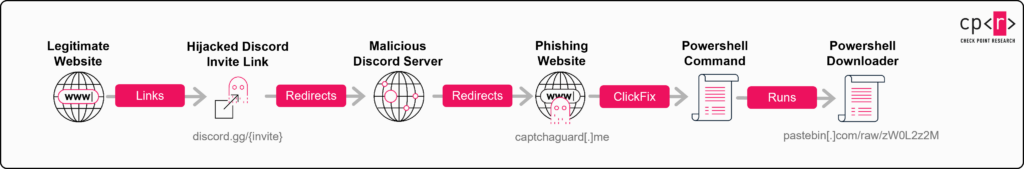
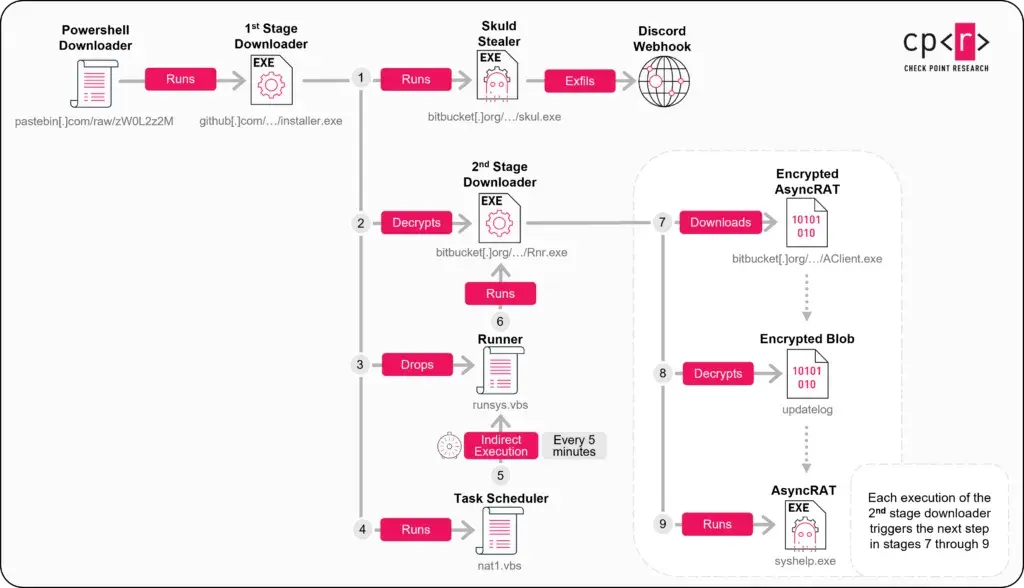
Attack Chain
Stage 1 – Reconnaissance & Lure Setup
- Target Audience: Gamers, Discord community members, modding forums, crypto users, and occasionally corporate users with Discord access.
- Initial Setup:
- Threat actors harvest expired or weakly protected Discord invite links.
- Alternatively, they generate new fake Discord invites mimicking legitimate communities (e.g., with vanity URLs or similar names).
- Malicious links are crafted to resemble normal discord[.]gg/abc123 invites.
Stage 2 – Distribution / Social Engineering
- Delivery Methods:
- Phishing emails (Discord-themed invites or game giveaways).
- Direct Messages (DMs) inside Discord, often from compromised accounts.
- Malvertising on game mod sites, cracked software sites, cheat forums.
- Lure Examples:
- “Join our exclusive modding Discord”
- “Claim your Nitro gift here”
- “Private server invite for testers”
Stage 3 – Silent Redirection / Hijack
- Clicking the malicious discord[.]gg/* link triggers:
- Silent redirect chains, often hosted on cloaking or analytics platforms.
- In some cases, the attacker abuses a Discord flaw allowing reuse of expired invite codes to inject redirects or custom content (BleepingComputer, 2025).
- Intermediate redirect platforms:
- discordgift[.]net, cdn.discordfiles[.]app, ngrok[.]io, .buzz, .shop, etc.
- Often obfuscated or shortened with services like bit[.]ly.
Stage 4 – Payload Delivery
- The redirection eventually lands on:
- Fake download pages (e.g., for mods, installers, Discord Nitro tools).
- Browser exploit kits (occasionally detected).
- Direct malware drop (ZIP, EXE, or PowerShell loaders).
- ClickFix Lure:
- Victims are tricked into interacting with a fake “verification” or “security” prompt.
- Clicking triggers background execution of CMD or PowerShell commands via malicious JavaScript or embedded scripts. (Centripetal, 2025)
- Common payloads:
- RedLine Stealer
- Lumma Stealer
- Quasar RAT / AsyncRAT
- Clipper malware for wallet address manipulation
Stage 5 – Execution & Persistence
Malware executes to:
- Exfiltrate credentials, browser cookies, Discord tokens.
- Establish persistence via startup entries or scheduled tasks.
- Contact C2 via Discord webhook, PasteBin clones, or Telegram bots.
In some cases, the infected system is used to further spread the lure via Discord DMs.
Stage 6 – Lateral Movement / Secondary Targeting
Indicators observed in isolated cases:
- Stolen tokens used to compromise high-permission Discord users.
- Internal Discord channels targeted to phish others.
- RDP credentials and saved browser passwords used for further intrusion into corporate systems.
Mitigation Strategies
While attackers continue to find new ways to exploit trusted platforms like Discord, security experts are actively working in parallel to identify vulnerabilities and develop effective mitigation strategies. In response to this campaign, the broader security community has published a number of recommendations to help reduce associated risks. The following list compiles key mitigation strategies drawn from those efforts.
Discord Users
- Avoid untrusted links and downloads – Refrain from clicking on unfamiliar links or downloading files from unknown or unverified sources.
- Be wary of fake verification prompts: Do not trust invites that require you to run manual commands (such as PowerShell) or download software as part of a “verification” process.
- Confirm the legitimacy of invite links: Only accept Discord invites verified through official channels, such as an organization’s website or social media. Avoid links from outdated forums or unofficial sources.
- Protect your personal information: Exercise caution when sharing personal or sensitive information, even within seemingly trustworthy online communities.
Discord server owners and administrators
- Avoid temporary invite links – Use permanent invite links where possible and limit who can generate them. Temporary or limited-use links are more vulnerable to hijacking if they expire and the associated server name remains cached or referenced publicly.
- Audit and remove unused invites – Regularly review active, expired, or unused invite links via your server settings. Delete any links that are no longer in use to minimize the attack surface.
- Implement moderation bots – Use trusted moderation bots to monitor new joins, detect suspicious patterns and take automatic actions like flagging or banning suspicious users.
- Review server permissions regularly – Audit who has admin or elevated permissions. Pay special attention to roles that can manage webhooks or external integrations, as these are commonly abused in malware distribution campaigns.
- Educate your community – Create a pinned message or a dedicated #security channel to regularly share updates on scams, phishing tactics, or impersonation attempts. Educated users are your first line of defense.
TTPs & IOCs
The following list of Indicators of Compromise (IOCs) was extracted from the in-depth technical analysis conducted by Check Point Research, as detailed in their 2025 publication titled “From Trust to Threat: Hijacked Discord Invites Used for Multi-Stage Malware Delivery” (CheckPoint, 2025). This report outlines how threat actors leverage expired or hijacked Discord invite links to initiate complex infection chains involving malware such as AsyncRAT, Skuld Stealer, and ChromeKatz. The IOCs below reflect the domains, URLs, IPs, and payload sources identified throughout the campaign.
Phishing Website
- captchaguard[.]me
- hxxps[:]//captchaguard[.]me/?key=
PowerShell Script
- hxxps[:]//pastebin[.]com/raw/zW0L2z2M
Bitbucket Repositories
- hxxps[:]//bitbucket[.]org/updatevak/upd/downloads
- hxxps[:]//bitbucket[.]org/syscontrol6/syscontrol/downloads
- hxxps[:]//bitbucket[.]org/updateservicesvar/serv/downloads
- hxxps[:]//bitbucket[.]org/registryclean1/fefsed/downloads
- hxxps[:]//bitbucket[.]org/htfhtthft/simshelper/downloads
First Stage Downloader (GitHub)
- hxxps[:]//github[.]com/frfs1/update/raw/refs/heads/main/installer.exe
- hxxps[:]//github[.]com/shisuh/update/raw/refs/heads/main/installer.exe
- hxxps[:]//github[.]com/gkwdw/wffaw/raw/refs/heads/main/installer.exe
Second Stage Downloader (Bitbucket)
- hxxps[:]//bitbucket[.]org/updatevak/upd/downloads/Rnr.exe
- hxxps[:]//bitbucket[.]org/syscontrol6/syscontrol/downloads/Rnr.exe
Skuld Stealer Payload
- hxxps[:]//bitbucket[.]org/updatevak/upd/downloads/skul.exe
- hxxps[:]//bitbucket[.]org/syscontrol6/syscontrol/downloads/skul.exe
AsyncRAT Payload
- hxxps[:]//bitbucket[.]org/updatevak/upd/downloads/AClient.exe
- hxxps[:]//bitbucket[.]org/syscontrol6/syscontrol/downloads/AClient.exe
AsyncRAT Dead Drop Resolvers (Pastebin)
- hxxps[:]//pastebin[.]com/raw/ftknPNF7
- hxxps[:]//pastebin[.]com/raw/NYpQCL7y
- hxxps[:]//pastebin[.]com/raw/QdseGsQL
AsyncRAT C2 Infrastructure
- 101[.]99[.]76[.]120
- 87[.]120[.]127[.]37
- 185[.]234[.]247[.]8
- microads[.]top
Discord Webhooks Used by Skuld
- hxxps[:]//discord[.]com/api/webhooks/1355186248578502736/_RDywh_K6GQKXiM5T05ueXSSjYopg9nY6XFJo1o5Jnz6v9sih59A8p-6HkndI_nOTicO
- hxxps[:]//discord[.]com/api/webhooks/1348629600560742462/RJgSAE7cYY-1eKMkl5EI-qZMuHaujnRBMVU_8zcIaMKyQi4mCVjc9R0zhDQ7wmPoD7Xp
Centripetal’s Perspective
Centripetal’s contribution to the broader analysis of this campaign places special emphasis on the phishing domain captchaguard[.]me, which was used to lure victims into interacting with a ClickFix-style social engineering prompt. Our focus is to dive deeper into this specific domain to uncover additional behavioral indicators and techniques not covered in other public reports, particularly those related to user deception and social engineering. While Check Point has published an extensive technical breakdown of the malware’s delivery mechanisms and infection stages (CheckPoint, 2025), our analysis aims to complement their findings by shifting attention to the psychological and interaction-based tactics employed in the initial stages of the attack.
Using open-source intelligence (OSINT), we gathered the following insights regarding the domain of interest:
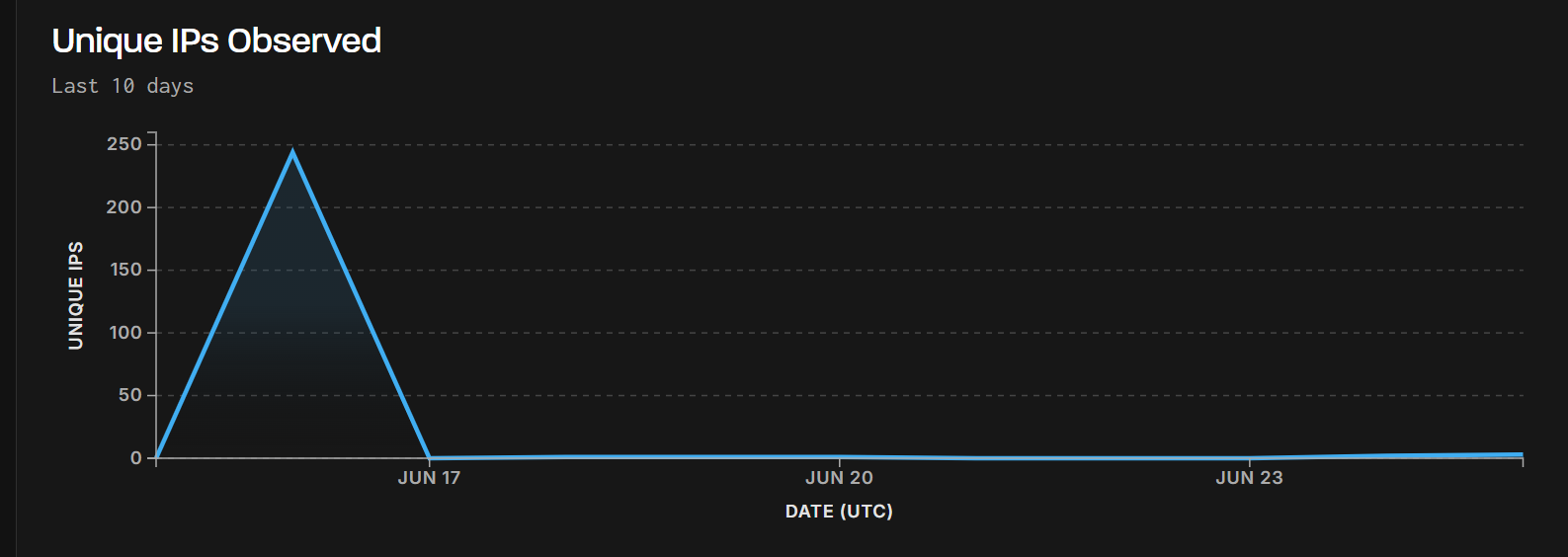
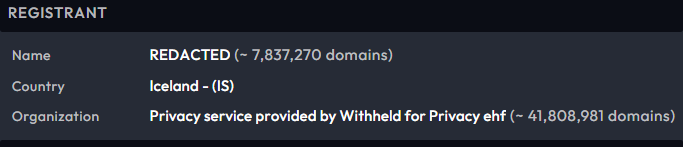

At Centripetal, we apply a rigorous vetting process when identifying and analyzing potential phishing domains. Key indicators we prioritize include:
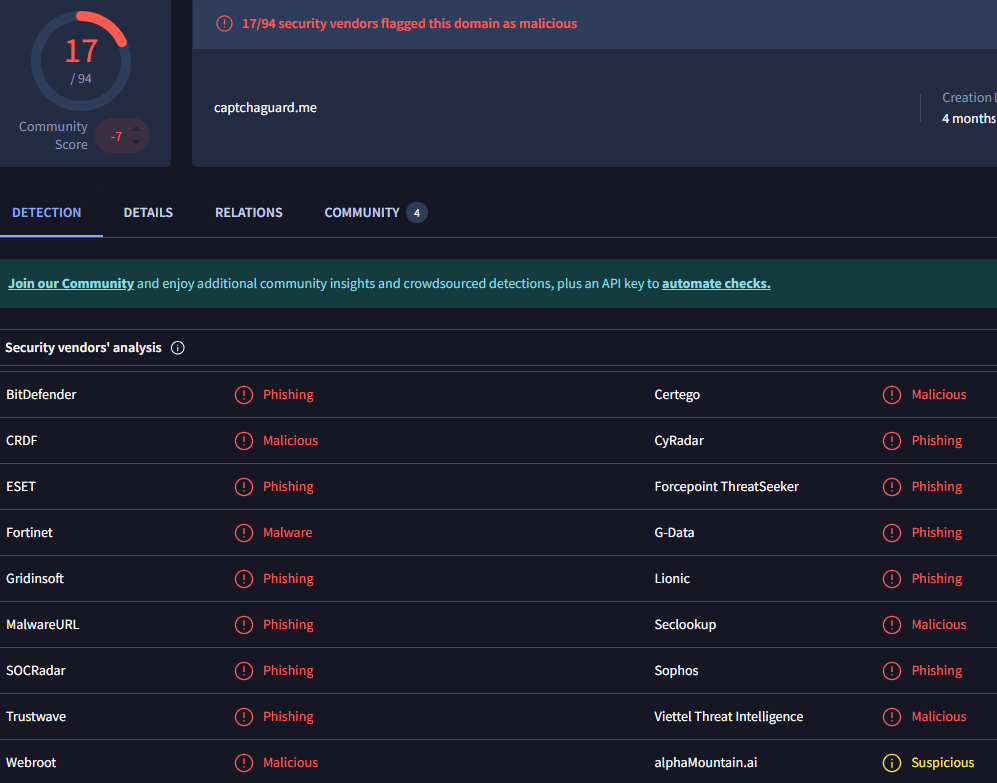
- Domain age Phishing domains are typically short-lived and newly registered, designed to operate briefly before being flagged and taken down. As shown in Figure 3, this domain is only 4 months old, a common trait among phishing infrastructure.
- Registration privacy While domain privacy is not inherently malicious, it is frequently used in phishing campaigns to obscure registrant identity. As seen in Figure 4, the registrant’s information has been redacted for privacy, which raises a red flag.
- Domain name Threat actors often register domains that mimic or slightly alter legitimate brand names to mislead users. Figure 5 highlights how reputable names are frequently repurposed or altered to create convincing phishing lures.
- Uncommon TLDs According to a Unit 42 report (Unit 42, 2025), cybercriminals often favor uncommon top-level domains (TLDs) such as .me, due to lower registration costs, wider availability, and lax oversight. This tactic helps reduce detection by standard filters.
- Security Vendor Detection As illustrated in Figure 6, numerous security vendors have flagged the domain as malicious, with multiple engines specifically categorizing it as phishing-related.
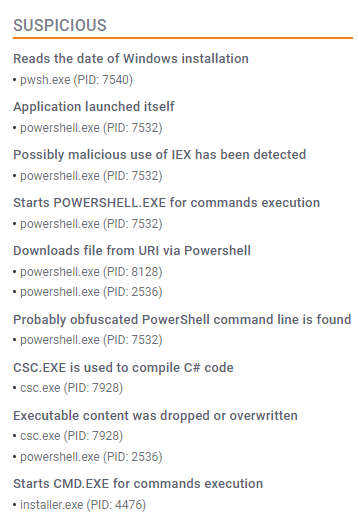
Next, we examine behavioral indicators commonly associated with phishing domains. According to sandbox analysis conducted by AnyRun (AnyRun, 2025), several red flags were observed for the domain in question.
The sandbox trace reveals strong indicators of a fileless PowerShell-driven malware infection chain, employing techniques such as obfuscation, remote command execution, and in-memory C# compilation. This behavior aligns with threats like Lumma Stealer, ClickFix, and other custom .NET-based loaders frequently observed in fake CAPTCHA or drive-by download campaigns, corroborating findings previously reported by Check Point. (Figure 7)
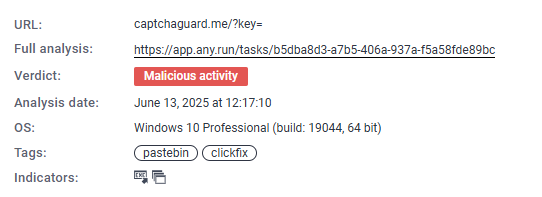
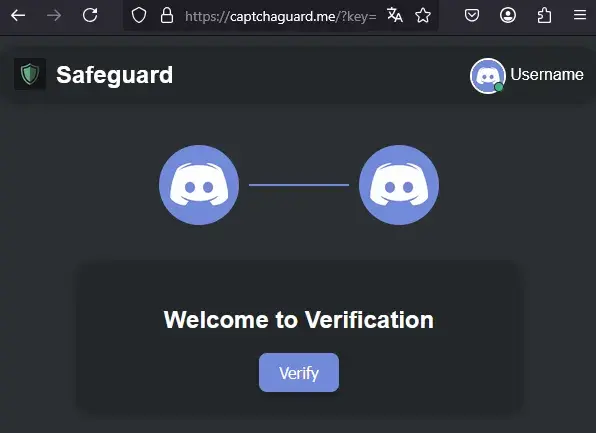
The final verdict from AnyRun (AnyRun, 2025) classifies the domain as malicious under the Pastebin/ClickFix category, confirming the use of deceptive CAPTCHA interstitials designed to socially engineer user interaction and deliver PowerShell payloads (e.g., XPowershell) or malware. (Figure 8) Additionally, reviewing historical images of the domain confirms the presence of a phishing lure crafted to mimic a Discord-like landing page, designed to deceive victims into engaging with the attack (Figure 9). According to CheckPoint “Clicking Verify executes JavaScript that silently copies a malicious PowerShell command to the user’s clipboard.”
An analysis of Centripetal’s visibility into the campaign, focusing on the domain captchaguard[.]me, reveals that it was first recorded in our threat intelligence database five days after its initial registration. (Figure 10: Centripetal’s first observed timestamp on the left; Domain Tools WHOIS record on the right.) This delay suggests a possible detection gap, potentially caused by evasion tactics used by the threat actors to avoid early identification and automated scanning.
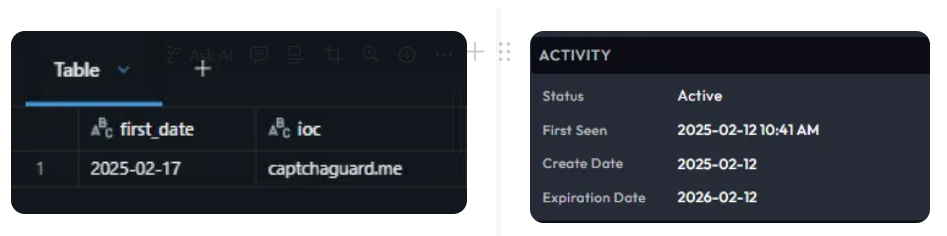
At the time of this writing, our coverage for this domain remains at 100%, meaning all observed resolution or connection attempts to captchaguard[.]me from our customers’ environments are actively shielded by our CleanINTERNET® and CleanINTERNET® DNS services. This ensures that any potential exposure to the associated threat infrastructure is blocked in real time, with no known instances of successful access or payload delivery (Figure 11).
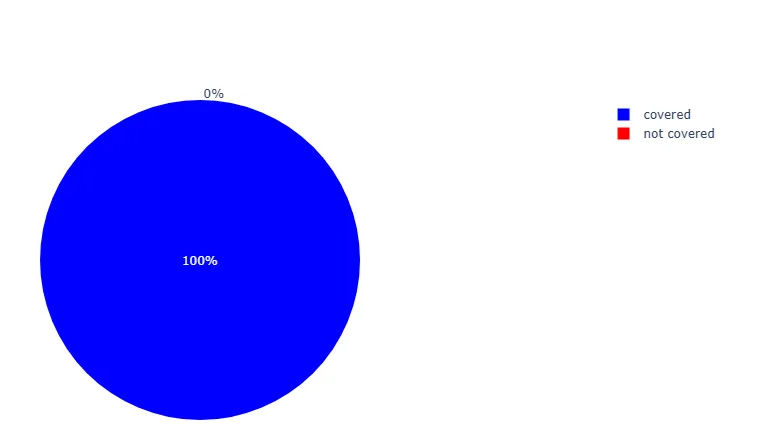
Although this analysis focused on a single domain observed in the campaign, blocking access to it significantly disrupts the attack chain. In this case, captchaguard[.]me served as a key redirection point for delivering the ClickFix lure. Preventing access to the domain stops the redirection flow and blocks malware execution before it begins, effectively neutralizing the threat at an early stage.
This campaign highlights how threat actors continue to exploit trusted platforms such as Discord to launch highly targeted, multi stage malware attacks. By abusing expired or spoofed invite links and deploying social engineering tactics like ClickFix lures, attackers are able to bypass traditional defenses and compromise end users with tools like AsyncRAT, Skuld Stealer, and ChromeKatz. While the campaign’s infrastructure may seem fragmented, as demonstrated with captchaguard[.]me, blocking even a single critical domain can effectively disrupt the attack chain. Continuous monitoring, early detection, and proactive user education remain essential to minimizing the impact of evolving social engineering threats within widely used platforms.
Centripetal is also pleased to offer Penetration Testing and Vulnerability Assessment services to help organizations identify vulnerabilities and reduce risk. If interested, please contact our Professional Services team at profservs@centripetal.ai or reach out to your Centripetal Account Representative.
Resources
- Discord Invite Link Hijacking Delivers AsyncRAT and Skuld Stealer Targeting Crypto Wallets
- Hackers Abuse Discord Invite to Spread Malicious Links and Deliver AsyncRAT
- From Trust to Threat: Hijacked Discord Invites Used for Multi-Stage Malware Delivery
- Hackers Compromise Discord Invite to Inject Malicious Links Delivering AsyncRAT
- The Silent Redirect: A Deep Dive into Discord Invite Hijacking and Advanced Malware
- Discord flaw lets hackers reuse expired invites in malware campaign
- Are You at Risk from Discord Invite Link Flaws? Here’s What You Need to Know
- Security Bulletin: ClickFix and the New Era of Social Engineering
- A Peek into Top-Level Domains and Cybercrime
- Trigger Domain Analysis
- Sandbox analysis of trigger domain
