By Aileen Ward
As of July 18, 2025, there has been a large-scale attempted exploitation of SharePoint on-prem instances that are vulnerable to an unauthenticated remote code execution (RCE) vulnerability chain. Vulnerabilities CVE-2025-53770 (SharePoint ToolShell Auth Bypass and RCE ) and CVE-2025-53771 (SharePoint ToolShell Path Traversal) were derivative CVEs created by Microsoft, and observed to be following the exploit chain using CVE-2025-49706 and CVE-2025-49704 disclosed in Pwn2Own Berlin in May 2025. At the time of analysis, a significant number of SharePoint endpoints remained publicly accessible, with exploitation attempts being attributed to nation-state groups including Chinese-linked actors Linen Typhoon, Violet Typhoon, and Storm-2603 (Microsoft, 2025). The veracity of this attack method demonstrates the use of SharePoint as a SaaS product being hosted and managed by Microsoft, has trumped on premises solutions with faster patching, centralized management and monitoring.
CVE-2025-53770
Vulnerability Type (CWE)
CWE-502: Deserialization of Untrusted Data

Figure 1: Mitre’s representation of CWE:502 (CVE.Mitre, 2024))
CVSS Score
Base Score: 9.8 (Critical)
Attack Vector: Network (AV:N)
Attack Complexity: Low (AC:L)
Privileges Required: None (PR:N)
User Interaction: None (UI:N)
Scope: Unchanged (S:U)
Impact on CIA: High
- Confidentiality: High (SC:H)
- Integrity: High (SI:H)
- Availability: High (SA:H)
CVE-2025-53771
Vulnerability Type (CWE)
CWE-22: Improper Limitation of a Pathname to a Restricted Directory (‘Path Traversal’)
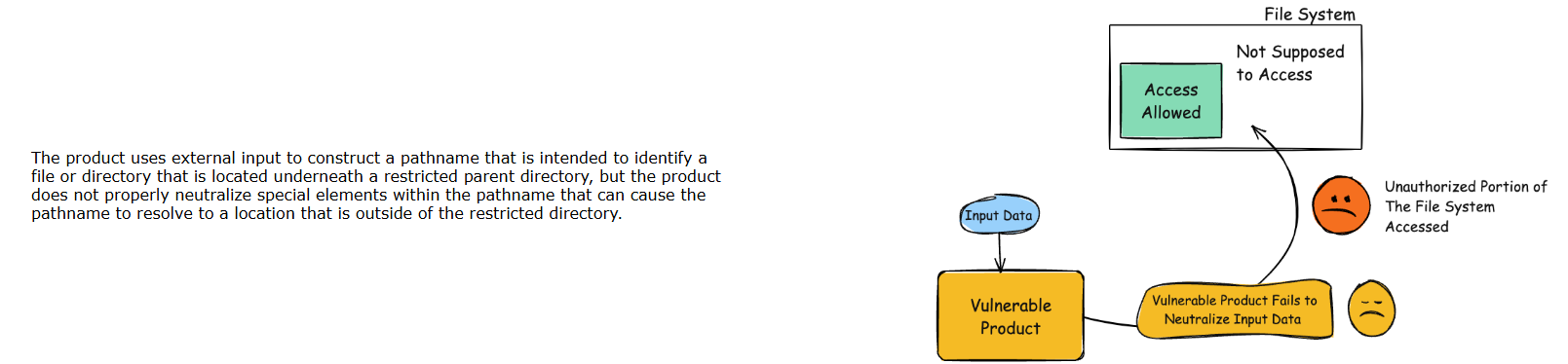
Figure 2: Mitre’s representation of CWE:22 (CVE.Mitre, 2024))
CWE-707: Improper Neutralization (CVE.Mitre, 2024)
CWE-20: Improper Input Validation
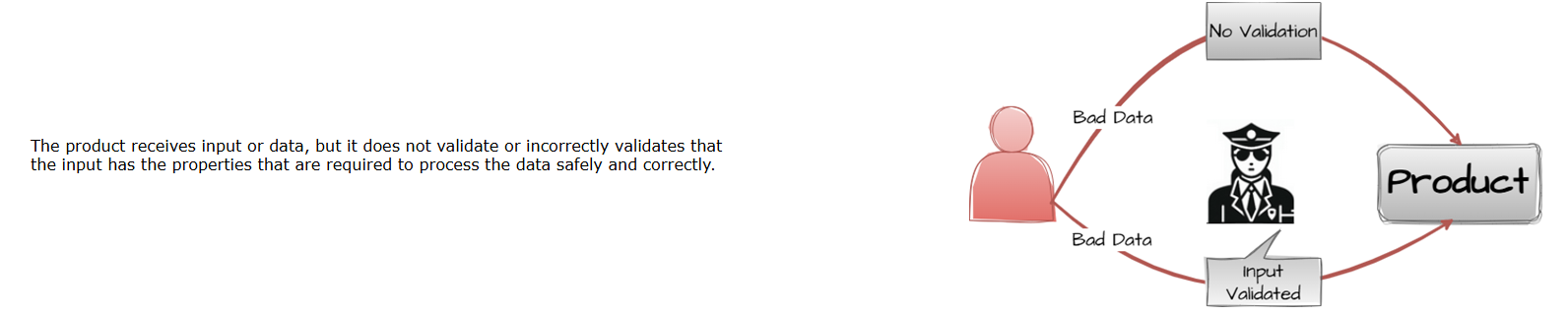
Figure 3: Mitre’s representation of CWE:502 (CVE.Mitre, 2024))
CVSS Score
Base Score: 6.3 (Medium)
Attack Vector: Network (AV:N)
Attack Complexity: Low (AC:L)
Privileges Required: Low (PR:L)
User Interaction: Required (UI:R)
Scope: Unchanged (S:U)
Impact on CIA: High
- Confidentiality: High (SC:H)
- Integrity: Low (SI:L)
- Availability: None (SA:N)
Impacted Versions
- Microsoft SharePoint Server 2019 (Patch available)
- Microsoft SharePoint Server 2016 (Patch pending)
- Microsoft SharePoint Server Subscription Edition (Patch available)
SharePoint Online is not affected.
Mitigation Steps
Microsoft recommends that administrators take the following actions immediately to mitigate the risk of exploitation:
Apply Security Updates
- Install the July 2025 Security Update and any subsequent patches for your version of SharePoint as soon as they are available.
- SharePoint Subscription Edition and SharePoint Server 2019 have updates available. Updates for SharePoint Server 2016 are pending release.
Enable Antimalware Scan Interface (AMSI) (Not to be applied in lieu of patching)
- Ensure AMSI is enabled and configured in Full Mode.
- Use a compatible antivirus solution.
- AMSI support was introduced in the September 2023 update for SharePoint 2016/2019 and Version 23H2 for Subscription Edition.
- If AMSI cannot be enabled, consider disconnecting the SharePoint server from the internet until updates are applied.
Deploy Endpoint Detection and Response (EDR)
- Deploy Microsoft Defender for Endpoint or an equivalent EDR solution to monitor and block post-exploitation activity.
Rotate ASP.NET Machine Keys
- After applying security updates or enabling AMSI, rotate SharePoint Server ASP.NET machine keys to invalidate any potentially compromised keys.
- Restart IIS on all SharePoint servers following key rotation.
- To rotate via PowerShell:
Update-SPMachineKey - To rotate via Central Administration:
- Go to Central Admin → Monitoring → Review job definitions
- Locate “Machine Key Rotation Job” and select “Run Now”
- After completion, run
iisreset.exeon each server
Follow National Authority and Microsoft’s Direction
US federal agencies are required to apply mitigations by July 21, 2025, as per the CISA KEV catalog directive. European agencies have also issued advisories based on the Microsoft Guidance (Microsoft, 2025).
Hunt for Compromise
Review server logs for the Indicators of Compromise (IOCs) listed below to determine if your systems have been targeted.
Exploit Process
The attack follows a multi-step process to achieve unauthenticated RCE and steal sensitive keys:
- Authentication Bypass (
CVE-2025-53771): The attacker sends a specially crafted POST request to the$../_layouts/15/ToolPane.aspx$endpoint. By setting the HTTPRefererheader to/_layouts/SignOut.aspx, they bypass authentication checks. - Payload Drop: The successful bypass allows the execution of an encoded PowerShell command. This command decodes a Base64 string and writes a malicious ASPX file,
spinstall0.aspx, to a web-accessible directory. - Cryptographic Key Theft: The attacker sends a GET request to the newly dropped
$../_layouts/15/spinstall0.aspx$file. This is not a typical webshell; its sole purpose is to use .NET methods to read the server’sMachineKeyconfiguration (including theValidationKeyandDecryptionKey) and return it in the HTTP response. __VIEWSTATEPayload Generation: With the stolenValidationKey, the attacker uses a tool likeysoserial.netto craft a malicious, serialized__VIEWSTATEpayload containing arbitrary commands.- Remote Code Execution (
CVE-2025-53770): The attacker submits the malicious__VIEWSTATEpayload to any valid SharePoint page. The server deserializes the payload, which it now trusts due to the valid signature, and executes the embedded commands.
Timeline
| Date | Description |
|---|---|
| May 2025 | “ToolShell” (CVE-2025-49706 + CVE-2025-49704) demonstrated at Pwn2Own Berlin |
| July 18, 2025 | Active, in-the-wild exploitation of a new variant chain begins |
| July 19, 2025 | Eye Security, Palo Alto Networks, and Microsoft publish advisories and IOCs. (See “Public Resources” section) |
| July 20, 2025 | CISA adds CVE-2025-53770 to its Known Exploited Vulnerabilities (KEV) catalog |
| July 21, 2025 | Microsoft releases patches for SharePoint Server 2019 & Subscription Edition and clarifies that CVE-2025-53770 is the code injection flaw and CVE-2025-53771 is the auth bypass |
| July 22, 2025 | Microsoft attributes nation-state actors to exploiting these chain vulnerabilities |
TTPs & IOCs
Tactics, Techniques, and Procedures (TTPs)
- Initial Access:
- T1190: Exploit Public-Facing Application
- Execution:
- T1668.001: Server-Side Template Injection
- T1059.001: PowerShell
- Persistence & Credential Access:
- T1505.003: Web Shell
- T1528: Steal Application Access Token by exfiltrating cryptographic machine keys
- Defense Evasion:
- T1027.002: Obfuscated Files or Information: Encoded Command
Indicators of Compromise (IoCs)
IP Addresses:
Initially released Indictors:
107.191.58[.]76
104.238.159[.]149
96.9.125[.]147
103.186.30[.]186
Extended Indicators referenced by EyeSecurity:
45.191.66[.]77
45.77.155[.]170
64.176.50[.]109
206.166.251[.]228
34.72.225[.]196
34.121.207[.]116
141.164.60[.]10
File Indicators:
- Filename:
spinstall0.aspx - File Path:
$C:\\PROGRA~1\\COMMON~1\\MICROS~1\\WEBSER~1\\16\\TEMPLATE\\LAYOUTS\\spinstall0.aspx$(and similar paths for other versions) - SHA256 Hash:
92bb4ddb98eeaf11fc15bb32e71d0a63256a0ed826a03ba293ce3a8bf057a514
Network Indicators:
- User-Agent:
Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0 - Exploit Path (POST):
/_layouts/15/ToolPane.aspx?DisplayMode=Edit&a=/ToolPane.aspx - Key HTTP Header:
Referer: /_layouts/SignOut.aspx - Payload Exfiltration (GET): Request to
/_layouts/15/spinstall0.aspx
Centripetal’s Perspective
Monitored inbound web traffic was first observed targeting a customer’s environment on July 21, 2025. The traffic from the previously unreported IPs outlined below were observed to be crafting the malicious POST requests that were being used for the exploit path. Further traffic composed of the specifically crafted GET requests to achieve payload exfiltration. Centripetal’s Intelligence Operations team responded to this traffic by shielding all of our customers from the identified IPs, and kicking off our customer incident protocols to support and provide guidance. Centripetal’s Intelligence Operations team continues to monitor for this activity against our customer’s environments and this activity is proactively shielded by CleanINTERNET® as the threat intelligence evolves for this campaign.
Indicators observed by Centripetal's Intelligence Operations Team:
116.234.34[.]5
60.178.230[.]96
129.227.230[.]84
117.182.107[.]175
154.205.143[.]3
103.186.30[.]186
Wider Landscape
The wider intelligence community continues to monitor the evolution of these vulnerabilities. At the time of analysis, over 16,400 SharePoint publicly exposed assets were identified on Shodan (Figure 7). As referenced by SocRadar (SocRadar, 2025), the composition of associated countries of these servers rank the United States and Iran as having the highest counts with Malaysia, Netherlands and Ireland completing the top 5 rank.
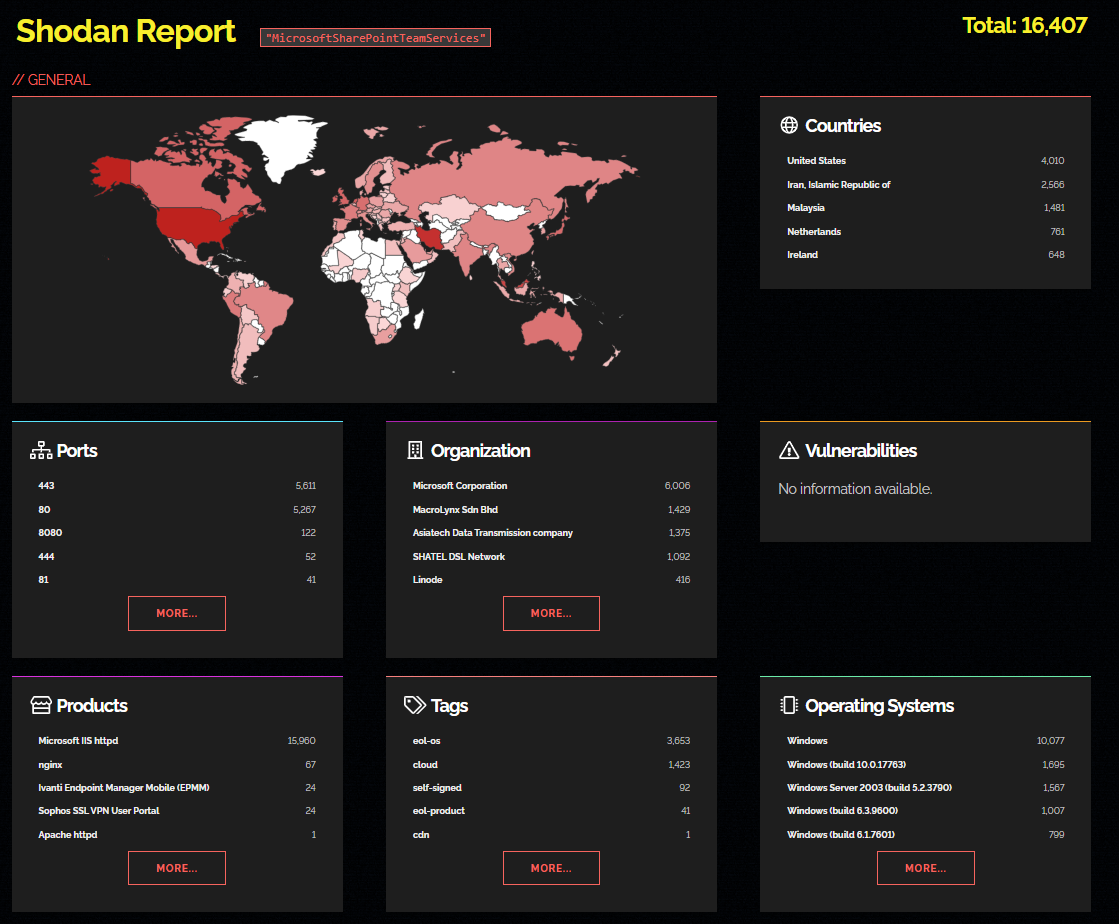
Figure 4: Snapshot of Shodan’s data on SharePoint assets (Shodan.io, 2025)
SEO term search worldwide as per Google rends. There is a general correlation between the affected regions and the Google searches uptick observed.
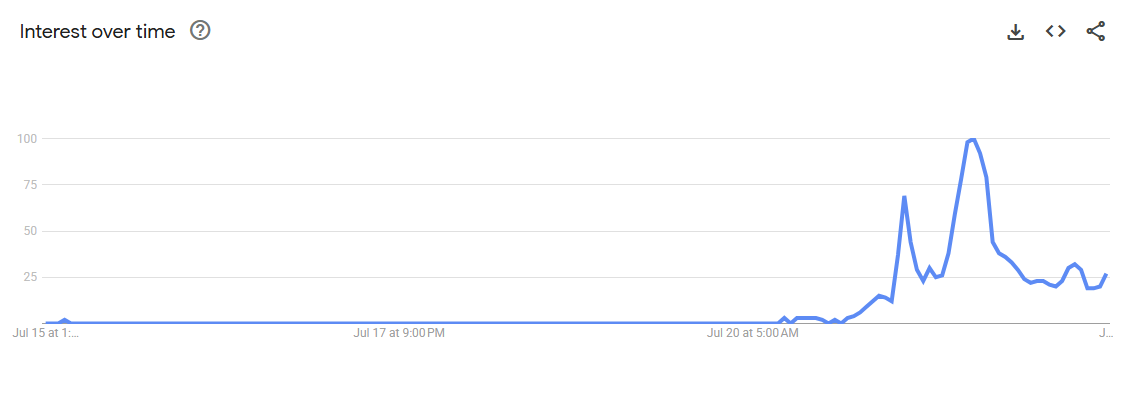
Figure 5: The interest in the term “sharepoint vulnerability” unsurprisingly spiked on 21 July, 2025
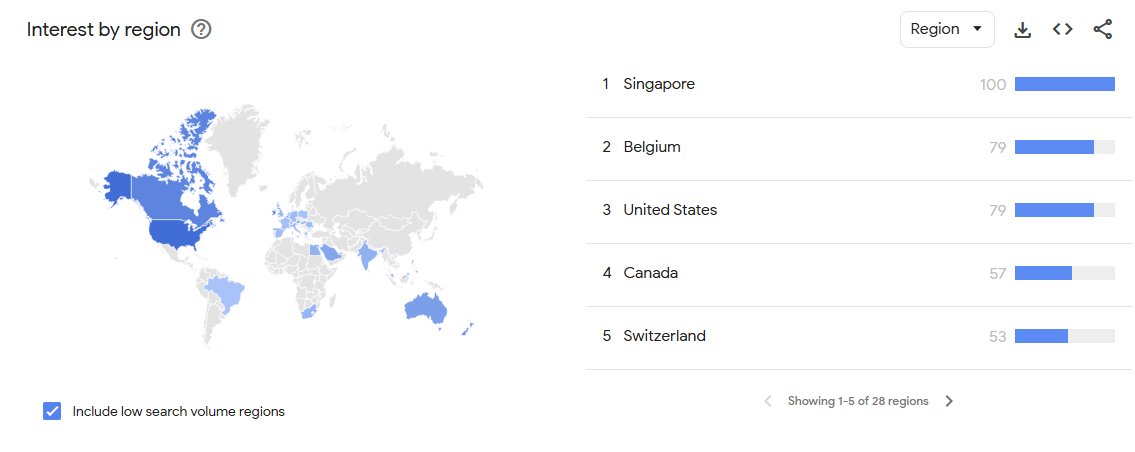
Figure 6: SEO results by region ranking Singapore and Belgium as the top searchers
Centripetal is actively monitoring for network indicators indicating the exploitation of CVE-2025-53770, CVE-2025-53771, CVE-2025-49704 and CVE-2025-49706. At the time of publishing, Centripetal offered maximum coverage across known indicators.
Leveraging billions of threat indicators, CleanINTERNET dynamically blocks malicious traffic using real-time global threat feeds and augmented human analysis, proactively protecting organizations from exploitation attempts involving known IoCs. This approach ensures reduced attack surface, enhanced security operations, and uninterrupted business continuity, enabling organizations to adopt a proactive and adaptive cybersecurity strategy against evolving threats.
As SharePoint is broadly used as a Microsoft product, the impact observed by this widespread exploitation has continued to evolve. From the disclosure of the initial CVE exploit chain in Pwn2Own Berlin in May 2025, the CVE variants have affected multiple organizations and have had extensive coverage from the security community. The disclosure of these CVEs illustrates that patching is often not enough to protect an environment from threat actors, however, having a proactive defense and a hardened security posture helps mitigate novel attack methods.
Centripetal is also pleased to offer Penetration Testing and Vulnerability Assessment services to help organizations identify vulnerabilities and reduce risk. If interested, please contact our Professional Services team at profservs@centripetal.ai or reach out to your Centripetal Account Representative.
Resources
- https://nvd.nist.gov/vuln/detail/CVE-2025-49704
- https://nvd.nist.gov/vuln/detail/CVE-2025-49706
- https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-53770
- https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-53771
- https://research.eye.security/sharepoint-under-siege/#timeline
- https://msrc.microsoft.com/blog/2025/07/customer-guidance-for-sharepoint-vulnerability-cve-2025-53770/
- https://github.com/PaloAltoNetworks/Unit42-timely-threat-intel/blob/main/2025-07-19-Microsoft-SharePoint-vulnerabilities-CVE-2025-49704-and-49706.txt
- https://www.helpnetsecurity.com/2025/07/20/microsoft-sharepoint-servers-under-attack-via-zero-day-vulnerability-with-no-patch-cve-2025-53770/
- https://www.theregister.com/2025/07/21/infosec_in_brief/
- CVE-2025-53770
- CVE-2025-53771
- https://cwe.mitre.org/data/definitions/22.html
- https://cwe.mitre.org/data/definitions/707.html
- https://cwe.mitre.org/data/definitions/20.html
- https://cwe.mitre.org/data/definitions/502.html
- https://www.wiz.io/blog/sharepoint-vulnerabilities-cve-2025-53770-cve-2025-53771-everything-you-need-to-k
- https://x.com/codewhitesec/status/1944743478350557232