By Bruce Skillern
Cybersecurity firm Trellix uncovered a sophisticated spear-phishing operation in late May 2025 that exploited NetBird, a legitimate open-source remote access platform, to infiltrate organizations worldwide.
The campaign has targeted financial executives across Europe, Africa, Canada, the Middle East, and South Asia, with companies in the banking, insurance, investment, and energy sectors especially affected (Trellix, 2025; The Hacker News, 2025). Following a detailed analysis by security firm Trellix, NetBird confirmed the attacks originated from a single malicious account that registered 197 machines, which was subsequently disabled. The total number of distinct organizations remains unknown as multiple machines could have been breached within a single entity (Trellix, 2025; NetBird, 2025).
The campaign which is being tracked by researchers, but has not yet been attributed to a known threat actor group, observed fake recruiter emails impersonating Rothschild & Co. offering “strategic opportunities” to lure victims. These messages initiated a multi-stage infection sequence designed to covertly install NetBird and OpenSSH on victim systems (Bobsguide, 2025). Despite the abuse, NetBird confirmed that no vulnerability was exploited, the attackers leveraged admin privileges gained through social engineering (NetBird, 2025).
Attack Chain
- Initial Lure: A phishing email posing as a Rothschild & Co recruiter contains a PDF attachment that links to a Firebase-hosted site (Trellix, 2025).
- CAPTCHA Gate: The phishing site hides the real URL using encrypted JavaScript, which is only revealed after solving a custom CAPTCHA (Insikt, 2025).
- Downloader:
- Stage One : Victims download a ZIP archive named
Rothschild_&*Co-6745763.zip, containing a 1KB VBScript (Rothschild*&_Co-6745763.vbs). This script contacts a C2 server to retrieve and execute a secondary script (pull.vbs) usingwscript.exe(The Hacker News, 2025). - Stage Two: The secondary VBScript downloads a payload (
trm), renames it totrm.zip, and extracts NetBird and OpenSSH MSI installers. These tools are silently installed, and their services are launched (The Hacker News, 2025).
- Stage One : Victims download a ZIP archive named
- Persistence Setup: The script creates a hidden local admin account named “
user” with passwordBs@202122, enables RDP, schedules NetBird auto-launch on reboot, modifies firewall rules, and removes NetBird shortcuts to stay undetected (NetBird, 2025).
Mitigation Strategies
For Executives
- Approach unsolicited job opportunities with skepticism, especially ZIP attachments.
- Do not bypass security alerts or enable content from suspicious sources.
- Immediately report suspicious messages to IT or security teams.
For Security Teams
- Deploy EDR tools to monitor abnormal VBS/PowerShell use and MSIExec behavior.
- Track creation of new local admin accounts with generic names.
- Implement a high-priority alert for
.zipfiles containing.vbsscripts delivered via email, especially when the VBScript is small (<5KB) and makes external network connections. - Continuously audit firewall modifications and scheduled task changes.
- Integrate phishing trends and simulations into employee training (Bobsguide, 2025).
TTPs & IOCs
MITRE ATT&CK Mapping
| T1566.002 | T1204.002 | T1059.005 | T1105 |
|---|---|---|---|
| Spearphishing via Link | User Execution (ZIP/VBS) | VBScript Execution | Tool Transfer (via HTTP) |
| T1059.001 | T1218.007 | T1543.003 | T1136.001 |
| PowerShell Execution | Signed Binary Proxy Execution (msiexec) | Windows Service Creation | Local Account Creation |
| T1053.005 | T1548.002 | T1112 | T1562.004 |
| Scheduled Task Creation | Bypass UAC | Registry Modification | Firewall Rule Manipulation |
| T1021.001 | T1021.004 | ||
| RDP Remote Access | SSH Remote Access |
Indicators of Compromise (IOCs)
| Indicator Type | Indicator |
|---|---|
| IP Address | 192[.]3[.]95[.]152 |
| Stage-0 URL | https://googl-6c11f.firebaseapp[.]com/… |
| Redirect URL | https://googl-6c11f.web[.]app/… |
| Stage-1 VBScript | Rothschild_&_Co-6745763.vbs (53192b6ba65a6abd44f167b3a8d0e52d) |
| Stage-2 VBScript | pull.vbs (b91162a019934b9cb3c084770ac03efe) |
| Payload Archive | trm.zip |
| Local Admin Account | user / Bs@202122 |
| Services | netbird, sshd |
| Setup Key | E48E4A70-4CF4-4A77-946B-C8E50A60855A |
Centripetal’s Perspective
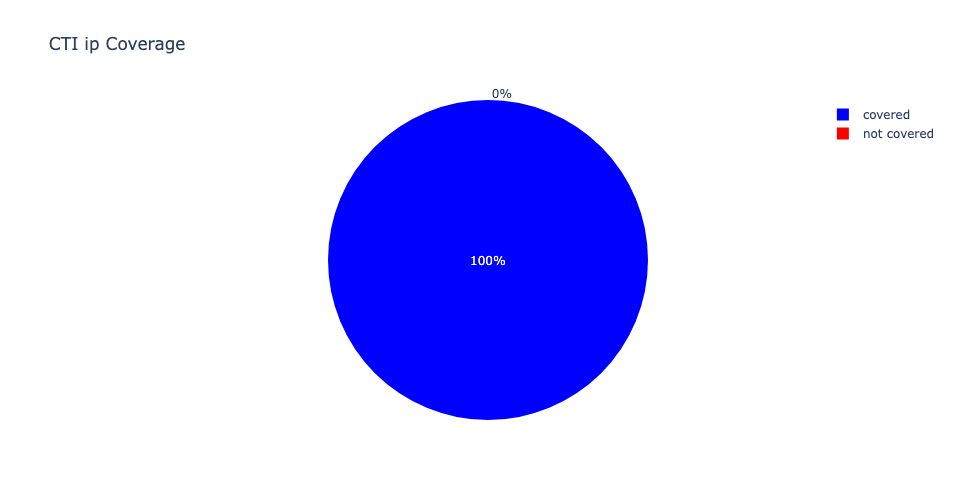
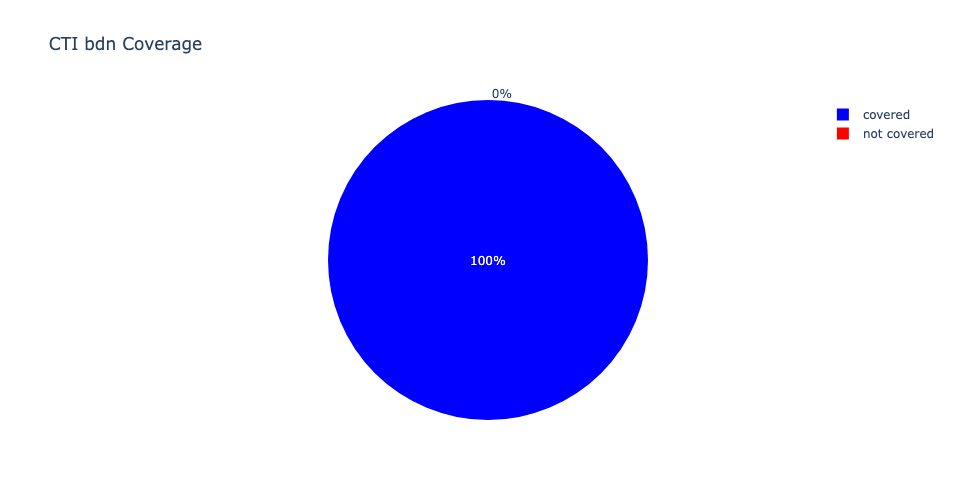
This campaign demonstrates a blend of evasive delivery tactics and abuse of legitimate software to establish persistent access on executive endpoints. Centripetal’s network intelligence capabilities provided early visibility into the adversary’s infrastructure. Notably, the command-and-control IP address 192.3.95[.]152, used for second-stage payload retrieval, was observed and classified on June 4, 2025, with 100% detection coverage across internal threat intelligence feeds. In addition, the stage-zero and redirect domains: googl-6c11f.firebaseapp[.]com and googl-6c11f.web[.]app, were matched and covered within external DNS intelligence sources as early as May 17, 2025. This dual-layer coverage across both IP and domain observables ensured pre- and post-compromise visibility, bolstering early mitigation capabilities.
Cross-feed coverage analysis showed full threat recognition using the minimal necessary provider set. Combined with high-confidence CTI matching, this enabled effective disruption of the attack chain before adversaries could progress to lateral movement or data theft. Centripetal’s detection data underscores the importance of maintaining comprehensive coverage of remote-access infrastructure across diverse intelligence sources.
The NetBird spear-phishing campaign serves as a stark reminder that an attacker’s most effective tool can be one already running in the target’s environment. With persistent techniques and evasive phishing lures, the attackers demonstrated a methodical and patient approach targeting high-level executives which calls for aggressive defense-in-depth security strategies. Organizations must prioritize executive protection, enhance endpoint visibility, and institutionalize ongoing awareness training. NetBird remains a secure product; however, its abuse by attackers underlines the importance of access controls and anomaly detection across enterprise endpoints to detect adversaries who hide in plain sight.
Centripetal is also pleased to offer Penetration Testing and Vulnerability Assessment services to help organizations identify vulnerabilities and reduce risk. If interested, please contact our Professional Services team at profservs@centripetal.ai or reach out to your Centripetal Account Representative.
Resources
- https://www.trellix.com/blogs/research/cfo-spear-phishing-netbird-attack/
- https://x.com/threatinsight/status/1927871419934986330
- https://www.cybersecuritydive.com/news/spearphishing-remote-access-campaign-cfos-finance-executives-trellix/749192/?&web_view=true
- https://netbird.io/knowledge-hub/netbird-response-to-spear-phishing-campaign-targeting-financial-executives
- https://www.bobsguide.com/cfos-targeted-globally-by-phishing-attacks/
